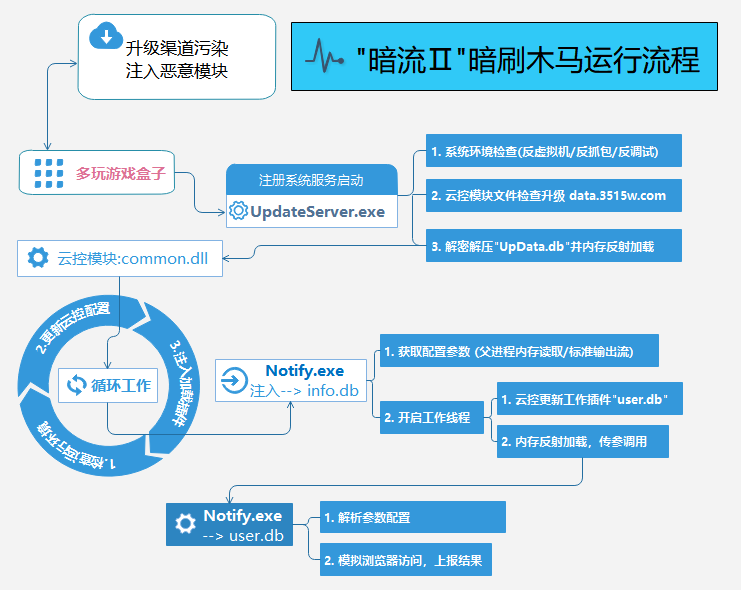
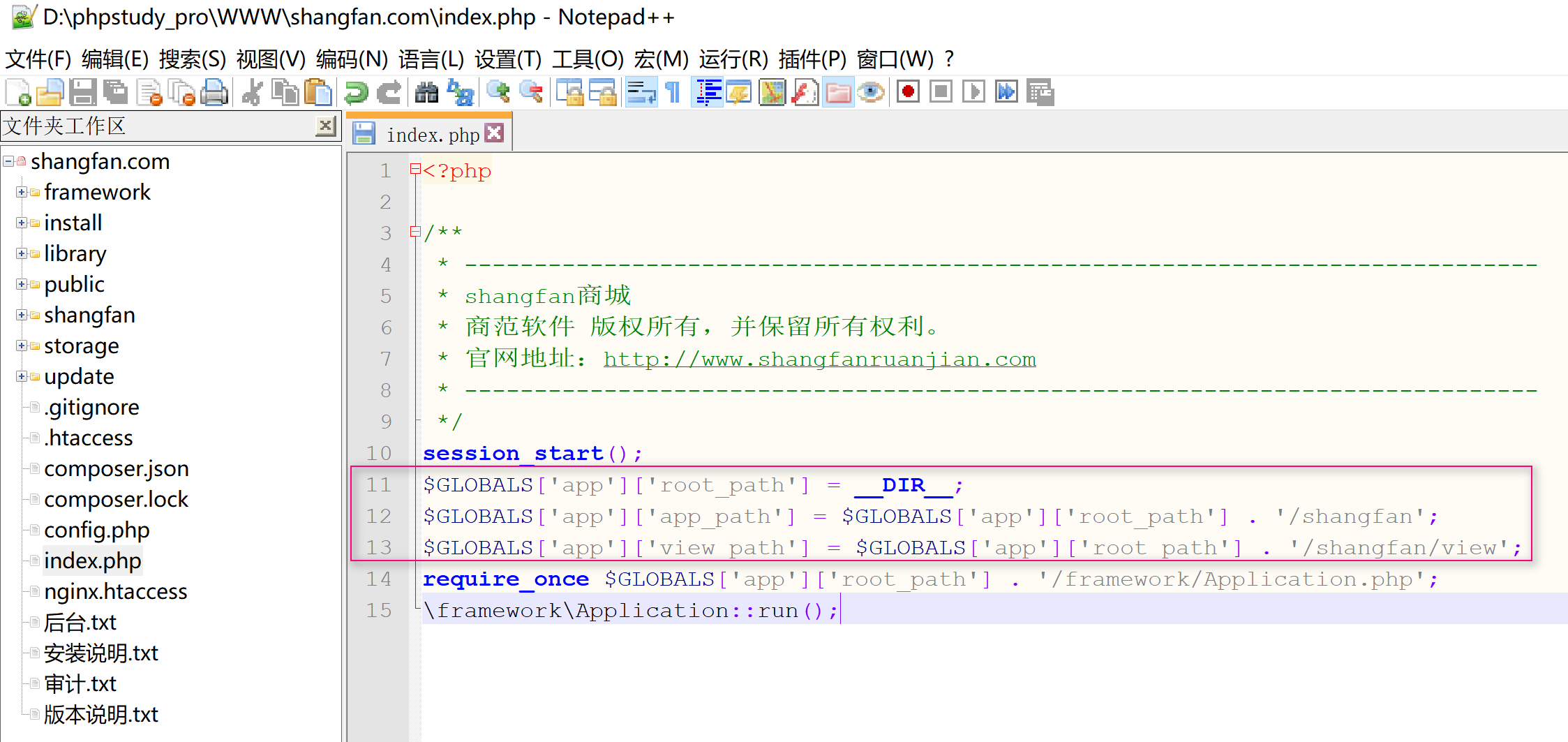
source: http://www.securityfocus.com/bid/5255/info
Python is an open source, object oriented programming language. The Python Pickle module is provided to convert object variables into a serialized form ("pickling"), and later recover the data back into an object hierarchy ("unpickling").
A vulnerability has been reported in the Pickle implementation included with some versions of Python. If malicious data is "unpickled", it may execute arbitrary Python commands. It is also possible to make system() calls.
Exploitation of this vulnerability will be highly dependent on a specific Python application which accepts a "pickle" string from an untrusted source. This behavior has been reported in some implementations of the Python SmartCookie class.
"S''*__import__('os').system('echo 0wn3d')np0n."
![图片[1]-Python 1.5.2 Pickle – Unsafe ‘eval()’ Code Execution-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号
CVE编号
![图片[2]-Python 1.5.2 Pickle – Unsafe ‘eval()’ Code Execution-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID
CNNVD-ID