source: http://www.securityfocus.com/bid/10471/info
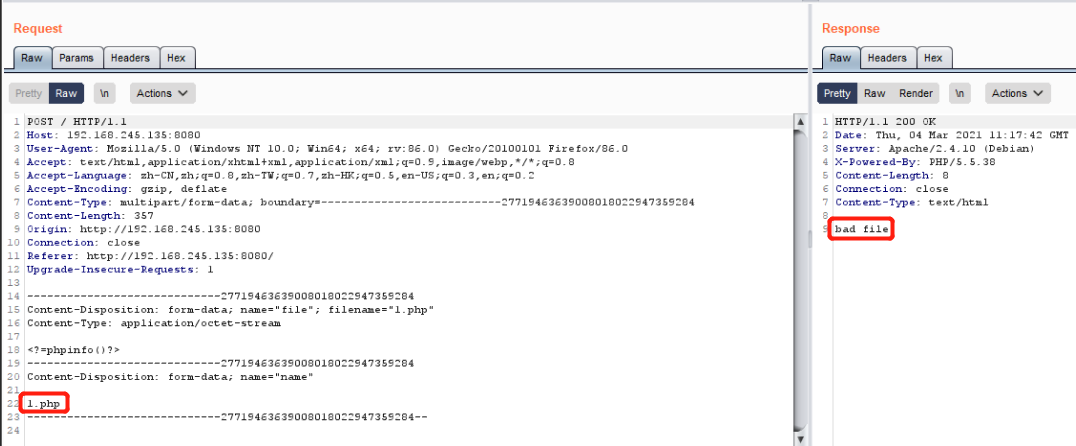
PHP is reportedly prone to a command execution vulnerability in its shell escape functions. This issue is due to a failure of PHP to properly sanitize function arguments.
This issue might allow an attacker to execute arbitrary shell commands on a computer running the vulnerable software within the security context of the web server; potentially leading to unauthorized access. Other attacks are also possible.
This issue is reported to affect PHP under Microsoft Windows version 4.3.3 and 4.3.5, it is likely that other Microsoft Windows versions are affected as well.
" || dir ||
![图片[1]-PHP 4.3.x – Microsoft Windows Shell Escape functions Command Execution-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号
CVE编号
![图片[2]-PHP 4.3.x – Microsoft Windows Shell Escape functions Command Execution-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID
CNNVD-ID

















恐龙抗狼扛1年前0
kankan啊啊啊啊3年前0
66666666666666