source: http://www.securityfocus.com/bid/1201/info
Netscape Communicator version 4.73 and prior may be susceptible to a /tmp file race condition when importing certificates. Netscape creates a /tmp file which is world readable and writable in /tmp, without calling stat() or fstat() on the file. As such, it is possible, should a user be able to predict the file name, to cause a symbolic link to be created, and followed elsewhere on the file system.
Additionally, as the file is created mode 666 prior to being fchmod()'d to 600, there may be a window of opportunity for altering the contents of this file.
This issue has only been demonstrated on the Linux binary, for glibc. The sparc Solaris binary does not behave this way.
Predict the name of the temporary file.
ln -sf /elsewhere /tmp/<tmpfilename>
Alternately, a program which watches for the creation of these temporary files, opens them upon their creation, and alters the contents can be written.
![图片[1]-Netscape 通信机 /tmp 符号链接漏洞-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号
CVE编号
![图片[2]-Netscape 通信机 /tmp 符号链接漏洞-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID
CNNVD-ID









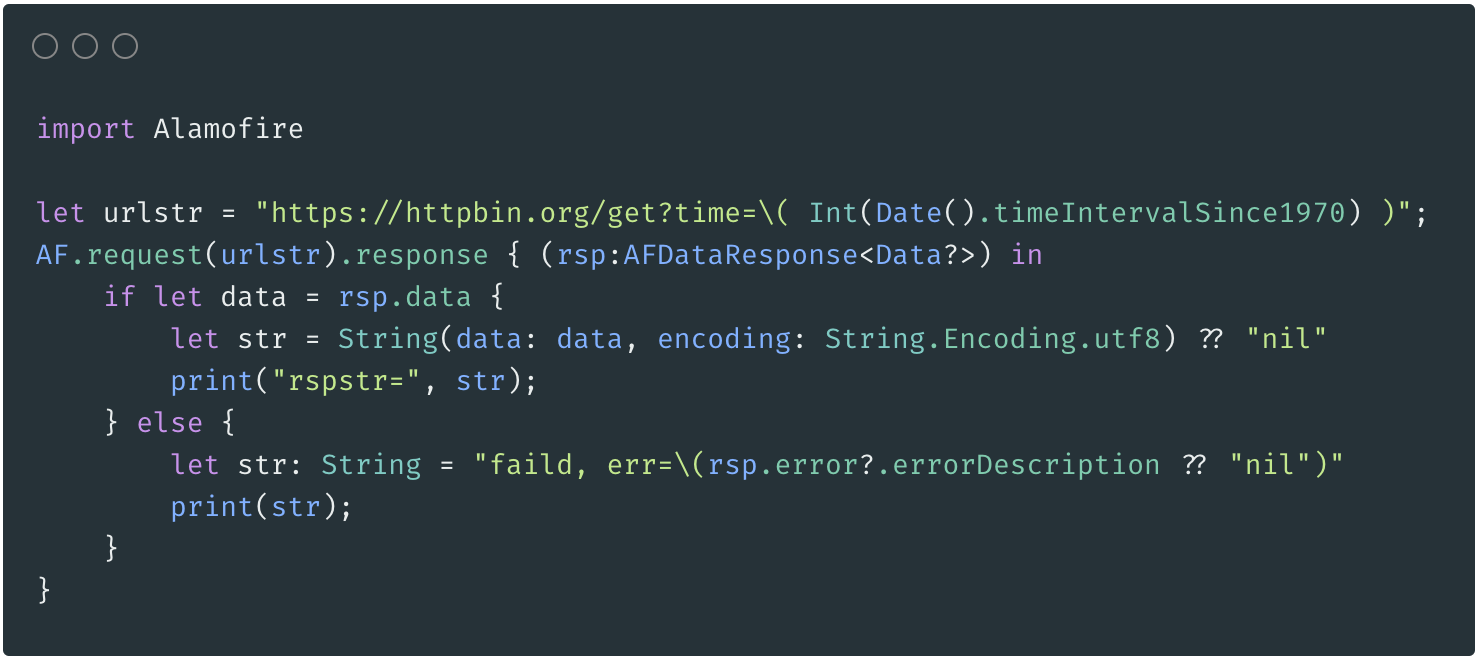







恐龙抗狼扛1年前0
kankan啊啊啊啊3年前0
66666666666666